
Data Solutions and Ransomware Decrypter
StoneFly Blog
Your go-to resource for insights on storage, hyperconverged, backup, disaster recovery, cloud, and unraveling the world of ransomware.
 Zero Trust: Enterprise Security for Ransomware Protection - Dive into our blog to discover how StoneFly's backup and disaster recovery appliances incorporate key features like air-gapped storage, immutability, and multi-factor authentication to fortify Zero Trust architecture and safeguard… Continue Reading
Zero Trust: Enterprise Security for Ransomware Protection - Dive into our blog to discover how StoneFly's backup and disaster recovery appliances incorporate key features like air-gapped storage, immutability, and multi-factor authentication to fortify Zero Trust architecture and safeguard… Continue Reading Malvertising: The Dark Side of Online Advertising - In our comprehensive guide, explore the shadowy world of malvertising—a pervasive threat to enterprises. From its evolution to detection strategies, delve into tactics and notable case studies to bolster your… Continue Reading
Malvertising: The Dark Side of Online Advertising - In our comprehensive guide, explore the shadowy world of malvertising—a pervasive threat to enterprises. From its evolution to detection strategies, delve into tactics and notable case studies to bolster your… Continue Reading Conti Ransomware: In-Depth Technical Breakdown - Explore the intricate workings of Conti ransomware, from its origins to notable attacks. Uncover mitigation strategies to fortify your defenses against this pervasive cyber threat. Continue Reading
Conti Ransomware: In-Depth Technical Breakdown - Explore the intricate workings of Conti ransomware, from its origins to notable attacks. Uncover mitigation strategies to fortify your defenses against this pervasive cyber threat. Continue Reading Supply Chain Attack: The Achilles’ Heel of Enterprise Security - Delve into the technical nuances of supply chain ransomware attacks and learn actionable strategies to improve your data security. Protect your critical data and mitigate risks effectively. Continue Reading
Supply Chain Attack: The Achilles’ Heel of Enterprise Security - Delve into the technical nuances of supply chain ransomware attacks and learn actionable strategies to improve your data security. Protect your critical data and mitigate risks effectively. Continue Reading How to Set Up S3 Object Storage for Veeam Data Platform - Step-by-step guide on configuring AWS S3 object storage or S3-compatible object storage as a Veeam backup and archiving target repository. This blog covers the complete process from mapping storage resources… Continue Reading
How to Set Up S3 Object Storage for Veeam Data Platform - Step-by-step guide on configuring AWS S3 object storage or S3-compatible object storage as a Veeam backup and archiving target repository. This blog covers the complete process from mapping storage resources… Continue Reading Watering Hole Attacks Unveiled: A Comprehensive Cyberthreat Overview - Dive into the intricate realm of watering hole cyberattacks and fortify your enterprise defenses. Uncover nuanced tactics, countermeasures, and emerging trends to stay one step ahead of cyberthreats. Continue Reading
Watering Hole Attacks Unveiled: A Comprehensive Cyberthreat Overview - Dive into the intricate realm of watering hole cyberattacks and fortify your enterprise defenses. Uncover nuanced tactics, countermeasures, and emerging trends to stay one step ahead of cyberthreats. Continue Reading Man-in-the-Middle Attack: Cyberthreat Amidst Data Streams - Discover proactive strategies against Man-in-the-Middle attacks. Stay ahead of evolving cyber threats with insights on prevention and emerging trends. Continue Reading
Man-in-the-Middle Attack: Cyberthreat Amidst Data Streams - Discover proactive strategies against Man-in-the-Middle attacks. Stay ahead of evolving cyber threats with insights on prevention and emerging trends. Continue Reading Innovate, Test, Patch, and Update: The Role of On-Demand Sandbox - Embark on a transformative journey in data management as we delve into the revolutionary realm of On-Demand Sandboxes. Explore seamless integration, purpose-built solutions, and cloud flexibility, unlocking the true potential… Continue Reading
Innovate, Test, Patch, and Update: The Role of On-Demand Sandbox - Embark on a transformative journey in data management as we delve into the revolutionary realm of On-Demand Sandboxes. Explore seamless integration, purpose-built solutions, and cloud flexibility, unlocking the true potential… Continue Reading How is Ransomware Delivered: 7 Common Delivery Methods - Explore the intricate world of cyber threats as we unveil the 7 ways how ransomware is delivered. From strategic tactics to stealthy approaches, fortify your defenses against evolving dangers. Continue Reading
How is Ransomware Delivered: 7 Common Delivery Methods - Explore the intricate world of cyber threats as we unveil the 7 ways how ransomware is delivered. From strategic tactics to stealthy approaches, fortify your defenses against evolving dangers. Continue Reading Cactus Ransomware: Decrypting the Tactics of the Latest Cyberthreat - Explore the intricate workings of Cactus Ransomware, a potent cyber threat targeting large entities since March 2023. Uncover its tactics, mitigation strategies, and a call to fortify cybersecurity measures in… Continue Reading
Cactus Ransomware: Decrypting the Tactics of the Latest Cyberthreat - Explore the intricate workings of Cactus Ransomware, a potent cyber threat targeting large entities since March 2023. Uncover its tactics, mitigation strategies, and a call to fortify cybersecurity measures in… Continue Reading BlackCat/ALPHV Ransomware: In-Depth Analysis and Mitigation - Explore the ins and outs of BlackCat/ALPHV ransomware – from its evolving tactics to proactive defense strategies. Arm yourself with insights to safeguard your digital landscape against this ever-adapting cyber… Continue Reading
BlackCat/ALPHV Ransomware: In-Depth Analysis and Mitigation - Explore the ins and outs of BlackCat/ALPHV ransomware – from its evolving tactics to proactive defense strategies. Arm yourself with insights to safeguard your digital landscape against this ever-adapting cyber… Continue Reading 5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing… Continue Reading
5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing… Continue Reading The Spear Phishing Survival Guide - Dive into the realm of spear phishing – understanding its tactics, preparing against it, and mitigating risks. Arm yourself with actionable insights for robust cybersecurity. Continue Reading
The Spear Phishing Survival Guide - Dive into the realm of spear phishing – understanding its tactics, preparing against it, and mitigating risks. Arm yourself with actionable insights for robust cybersecurity. Continue Reading Understanding Detection and Response: EDR vs MDR vs XDR vs NDR - iscover the pillars of modern cybersecurity — EDR, MDR, XDR, and NDR. Uncover the distinctions, working mechanisms, and benefits of each to fortify your organization's digital defenses. Continue Reading
Understanding Detection and Response: EDR vs MDR vs XDR vs NDR - iscover the pillars of modern cybersecurity — EDR, MDR, XDR, and NDR. Uncover the distinctions, working mechanisms, and benefits of each to fortify your organization's digital defenses. Continue Reading Trigona Ransomware: What is it and How to Defend Against it - Explore the shadowy world of Trigona ransomware, a formidable cyberthreat. Delve into its origins, infection methods, and impacts. Discover how to prepare for and defend against this digital menace. Continue Reading
Trigona Ransomware: What is it and How to Defend Against it - Explore the shadowy world of Trigona ransomware, a formidable cyberthreat. Delve into its origins, infection methods, and impacts. Discover how to prepare for and defend against this digital menace. Continue Reading Lockbit Ransomware: Inside the Cyberthreat and Defense Strategies - Discover the inner workings of LockBit ransomware, its origins, and its continuous evolution in the relentless world of cybercrime. Learn how to safeguard your organization against this potent threat. Continue Reading
Lockbit Ransomware: Inside the Cyberthreat and Defense Strategies - Discover the inner workings of LockBit ransomware, its origins, and its continuous evolution in the relentless world of cybercrime. Learn how to safeguard your organization against this potent threat. Continue Reading What Defending Against Ransomware-as-a-Service (RaaS) Entails - Ransomware-as-a-Service (RaaS) has emerged as a formidable adversary. This blog delves into what RaaS entails and offers insights on how to fortify your defenses against this evolving peril. Continue Reading
What Defending Against Ransomware-as-a-Service (RaaS) Entails - Ransomware-as-a-Service (RaaS) has emerged as a formidable adversary. This blog delves into what RaaS entails and offers insights on how to fortify your defenses against this evolving peril. Continue Reading What are Advanced Persistent Threats (APTs) and How to Stop Them - Explore the realm of Advanced Persistent Threat (APT) attacks, understand their strategies, detection methods, and fortify your defenses for unyielding data security. Continue Reading
What are Advanced Persistent Threats (APTs) and How to Stop Them - Explore the realm of Advanced Persistent Threat (APT) attacks, understand their strategies, detection methods, and fortify your defenses for unyielding data security. Continue Reading Remote Code Execution (RCE) Attack and Vulnerabilities: Complete Overview - Dive into the realm of Remote Code Execution (RCE) attacks and fortify your cybersecurity. Discover how air-gapped and immutable backups can be your shield against evolving cyber threats. Continue Reading
Remote Code Execution (RCE) Attack and Vulnerabilities: Complete Overview - Dive into the realm of Remote Code Execution (RCE) attacks and fortify your cybersecurity. Discover how air-gapped and immutable backups can be your shield against evolving cyber threats. Continue Reading DDoS Attacks Decoded: Defending Against Modern Cyber Onslaughts - Delve into the disruptive realm of DDoS attacks, understanding their operations and motives. Learn how air-gapping and immutability fortify defenses, ensuring a resilient cybersecurity posture against relentless online assaults. Continue Reading
DDoS Attacks Decoded: Defending Against Modern Cyber Onslaughts - Delve into the disruptive realm of DDoS attacks, understanding their operations and motives. Learn how air-gapping and immutability fortify defenses, ensuring a resilient cybersecurity posture against relentless online assaults. Continue Reading Botnets Unveiled: Navigating the Underworld of Cyber Threats - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security. Continue Reading
Botnets Unveiled: Navigating the Underworld of Cyber Threats - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security. Continue Reading Demystifying SQL Injection: How It Works and How to Defend Against It - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security. Continue Reading
Demystifying SQL Injection: How It Works and How to Defend Against It - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security. Continue Reading Remote Access Trojans (RATs): The Silent Invaders of Cybersecurity - Delve into the realm of Remote Access Trojans (RATs) – their tactics, impact, and defense strategies. Explore the evolving landscape of cyber threats. Continue Reading
Remote Access Trojans (RATs): The Silent Invaders of Cybersecurity - Delve into the realm of Remote Access Trojans (RATs) – their tactics, impact, and defense strategies. Explore the evolving landscape of cyber threats. Continue Reading How to Set Up Immutable Snapshots for Ransomware Protection - Discover the significance of immutable snapshots for enhanced data security. Explore their benefits, practical applications, and step-by-step setup guide to bolster your data protection strategy. Continue Reading
How to Set Up Immutable Snapshots for Ransomware Protection - Discover the significance of immutable snapshots for enhanced data security. Explore their benefits, practical applications, and step-by-step setup guide to bolster your data protection strategy. Continue Reading Finance Industry at Risk: Navigating the Ransomware Threat Landscape - As cyber threats loom large over the finance industry, understanding the gravity of ransomware's impact is paramount. Explore the repercussions, regulatory concerns, and proven strategies to safeguard your financial systems. Continue Reading
Finance Industry at Risk: Navigating the Ransomware Threat Landscape - As cyber threats loom large over the finance industry, understanding the gravity of ransomware's impact is paramount. Explore the repercussions, regulatory concerns, and proven strategies to safeguard your financial systems. Continue Reading Defending Your Data: The Vital Role of Multi-Factor Authentication - Discover the power of multi-factor authentication (MFA) in modern data security. StoneFly's innovative storage solutions offer a seamless and robust approach to safeguarding your critical data. Enhance your data protection… Continue Reading
Defending Your Data: The Vital Role of Multi-Factor Authentication - Discover the power of multi-factor authentication (MFA) in modern data security. StoneFly's innovative storage solutions offer a seamless and robust approach to safeguarding your critical data. Enhance your data protection… Continue Reading Immutable File-Level WORM: Setup Guide and Best Practices - Unleash the strength of Immutable File-Level WORM (FileLock) to secure your critical data. Safeguard against unauthorized changes and ransomware threats. Explore our step-by-step guide to implement this advanced data protection… Continue Reading
Immutable File-Level WORM: Setup Guide and Best Practices - Unleash the strength of Immutable File-Level WORM (FileLock) to secure your critical data. Safeguard against unauthorized changes and ransomware threats. Explore our step-by-step guide to implement this advanced data protection… Continue Reading How to Integrate Azure/AWS Object Storage to On-Premises Appliance - Discover how to integrate Azure Blob, AWS, or other S3-compatible clouds with your on-premises appliance. Seamlessly manage and store data, leverage cloud benefits, and enhance your data management capabilities across… Continue Reading
How to Integrate Azure/AWS Object Storage to On-Premises Appliance - Discover how to integrate Azure Blob, AWS, or other S3-compatible clouds with your on-premises appliance. Seamlessly manage and store data, leverage cloud benefits, and enhance your data management capabilities across… Continue Reading Preventing Data Loss: Importance of Volume Deletion Protection - Volume deletion protection provides the necessary safeguard to ensure data integrity and availability. Learn the importance of this feature and how it enhances data security and business continuity in this… Continue Reading
Preventing Data Loss: Importance of Volume Deletion Protection - Volume deletion protection provides the necessary safeguard to ensure data integrity and availability. Learn the importance of this feature and how it enhances data security and business continuity in this… Continue Reading How to Stop Ransomware Attacks from Deleting Backup Data - Ransomware attacks pose a significant threat to backup data, leaving organizations vulnerable and with limited options. Discover effective strategies to protect your valuable backups and thwart ransomware's hold. Learn about… Continue Reading
How to Stop Ransomware Attacks from Deleting Backup Data - Ransomware attacks pose a significant threat to backup data, leaving organizations vulnerable and with limited options. Discover effective strategies to protect your valuable backups and thwart ransomware's hold. Learn about… Continue Reading From Production to Protection: Securing Manufacturing Against Ransomware - Discover why the manufacturing industry is a prime target for ransomware attacks and learn crucial steps to protect your operations, data, and reputation from evolving cyber threats. Continue Reading
From Production to Protection: Securing Manufacturing Against Ransomware - Discover why the manufacturing industry is a prime target for ransomware attacks and learn crucial steps to protect your operations, data, and reputation from evolving cyber threats. Continue Reading Compare Array vs Host vs Hypervisor vs Network-Based Replication - Explore the array, host, hypervisor, and network-based replication techniques. This blog provides a detailed comparison, covering use cases, advantages, and disadvantages. Make informed decisions for your data protection and disaster… Continue Reading
Compare Array vs Host vs Hypervisor vs Network-Based Replication - Explore the array, host, hypervisor, and network-based replication techniques. This blog provides a detailed comparison, covering use cases, advantages, and disadvantages. Make informed decisions for your data protection and disaster… Continue Reading Mirroring vs Replication vs Clustering: A Data Protection Comparison - Explore the essential concepts of high availability, fault tolerance, and disaster recovery, and understand how they contribute to ensuring uninterrupted business operations. Discover the key differences and benefits of each… Continue Reading
Mirroring vs Replication vs Clustering: A Data Protection Comparison - Explore the essential concepts of high availability, fault tolerance, and disaster recovery, and understand how they contribute to ensuring uninterrupted business operations. Discover the key differences and benefits of each… Continue Reading Comparing High Availability vs Fault Tolerance vs Disaster Recovery - Explore the essential concepts of high availability, fault tolerance, and disaster recovery, and understand how they contribute to ensuring uninterrupted business operations. Discover the key differences and benefits of each… Continue Reading
Comparing High Availability vs Fault Tolerance vs Disaster Recovery - Explore the essential concepts of high availability, fault tolerance, and disaster recovery, and understand how they contribute to ensuring uninterrupted business operations. Discover the key differences and benefits of each… Continue Reading BaaS vs RaaS vs DRaaS Comparison – Which is Best - Are you confused about whether your business needs Backup as a Service (BaaS), Recovery as a Service (RaaS), or Disaster Recovery as a Service (DRaaS)? With so many options available,… Continue Reading
BaaS vs RaaS vs DRaaS Comparison – Which is Best - Are you confused about whether your business needs Backup as a Service (BaaS), Recovery as a Service (RaaS), or Disaster Recovery as a Service (DRaaS)? With so many options available,… Continue Reading How to Size Air-gapped and Immutable Storage for Veeam v12 - When used correctly with Veeam v12, air-gapped and immutable storage provides an additional layer of protection against cyber threats and ransomware attacks. However, it's important to properly size your storage… Continue Reading
How to Size Air-gapped and Immutable Storage for Veeam v12 - When used correctly with Veeam v12, air-gapped and immutable storage provides an additional layer of protection against cyber threats and ransomware attacks. However, it's important to properly size your storage… Continue Reading How to Calculate and Improve Recovery Time and Point Objectives - In disaster recovery, Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) are crucial metrics to ensure minimum data loss and maximum recovery speed. Calculating the right RTPO values depends… Continue Reading
How to Calculate and Improve Recovery Time and Point Objectives - In disaster recovery, Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) are crucial metrics to ensure minimum data loss and maximum recovery speed. Calculating the right RTPO values depends… Continue Reading From Backup to Video Editing: 5 Use-Cases for NAS Storage - This blog explores the primary use-cases for Network-Attached Storage (NAS) and emphasizes the importance of choosing the right NAS solution for specific business needs. Readers will gain insights into how… Continue Reading
From Backup to Video Editing: 5 Use-Cases for NAS Storage - This blog explores the primary use-cases for Network-Attached Storage (NAS) and emphasizes the importance of choosing the right NAS solution for specific business needs. Readers will gain insights into how… Continue Reading Azure Backup vs AWS Backup: Which Cloud Backup Solution is More Secure - In this blog, we compare and contrast the security and backup features of two major cloud platforms, Azure and AWS. We delve into the key differences between Azure and AWS… Continue Reading
Azure Backup vs AWS Backup: Which Cloud Backup Solution is More Secure - In this blog, we compare and contrast the security and backup features of two major cloud platforms, Azure and AWS. We delve into the key differences between Azure and AWS… Continue Reading Safeguarding Your Data: Best Practices for Secure Cloud Storage - Are you concerned about the security of your data in the cloud? Do you struggle with planning and managing your storage capacity effectively? Are you looking for ways to maximize… Continue Reading
Safeguarding Your Data: Best Practices for Secure Cloud Storage - Are you concerned about the security of your data in the cloud? Do you struggle with planning and managing your storage capacity effectively? Are you looking for ways to maximize… Continue Reading Maximizing Data Protection with Cloud Backup and Recovery - Protecting your enterprise data is crucial, and having a comprehensive cloud backup and recovery solution is vital for your business continuity. StoneFly offers enterprise-grade cloud backup and recovery solutions in… Continue Reading
Maximizing Data Protection with Cloud Backup and Recovery - Protecting your enterprise data is crucial, and having a comprehensive cloud backup and recovery solution is vital for your business continuity. StoneFly offers enterprise-grade cloud backup and recovery solutions in… Continue Reading Guide to Sizing Your Enterprise SAN Appliance for Optimal Storage - This blog provides IT managers with practical tips on sizing an enterprise SAN storage appliance, including storage capacity, CPU, and system memory. It also covers data protection, disaster recovery, and… Continue Reading
Guide to Sizing Your Enterprise SAN Appliance for Optimal Storage - This blog provides IT managers with practical tips on sizing an enterprise SAN storage appliance, including storage capacity, CPU, and system memory. It also covers data protection, disaster recovery, and… Continue Reading On-Premise vs Private Cloud: Choosing the Right Infrastructure for Your Business Needs - Learn how to choose the right cloud infrastructure for your business with this comprehensive guide from StoneFly. Explore the pros and cons of on-premise data centers and private clouds, the… Continue Reading
On-Premise vs Private Cloud: Choosing the Right Infrastructure for Your Business Needs - Learn how to choose the right cloud infrastructure for your business with this comprehensive guide from StoneFly. Explore the pros and cons of on-premise data centers and private clouds, the… Continue Reading Enterprise Cybersecurity Solutions: Best Practices and Strategies for Data Protection - Protecting enterprise data and assets is critical in today's threat landscape. This blog discusses the importance of enterprise cybersecurity and provides an overview of different solutions and best practices. Don't… Continue Reading
Enterprise Cybersecurity Solutions: Best Practices and Strategies for Data Protection - Protecting enterprise data and assets is critical in today's threat landscape. This blog discusses the importance of enterprise cybersecurity and provides an overview of different solutions and best practices. Don't… Continue Reading Upgrade 3-2-1 Rule with Veeam ONE v12’s Immutability and Monitoring - The 3-2-1 rule is a proven method for safeguarding data with multiple recoverable copies. In today's threat landscape, it's crucial to enhance the rule by incorporating immutability and continuous monitoring… Continue Reading
Upgrade 3-2-1 Rule with Veeam ONE v12’s Immutability and Monitoring - The 3-2-1 rule is a proven method for safeguarding data with multiple recoverable copies. In today's threat landscape, it's crucial to enhance the rule by incorporating immutability and continuous monitoring… Continue Reading 2022 Ransomware Attack Trend Report: Key Findings - Comprehensive report about ransomware attack trends including common attack vectors, industries targeted by ransomware, and ransomware costs for 2022. Continue Reading
2022 Ransomware Attack Trend Report: Key Findings - Comprehensive report about ransomware attack trends including common attack vectors, industries targeted by ransomware, and ransomware costs for 2022. Continue Reading How is Ransomware Affecting the Healthcare Industry - Healthcare sector continues to be a prime target for ransomware attacks. Hackers attempt to steal patient data, and sensitive information to sell in the dark web. This makes ransomware protection… Continue Reading
How is Ransomware Affecting the Healthcare Industry - Healthcare sector continues to be a prime target for ransomware attacks. Hackers attempt to steal patient data, and sensitive information to sell in the dark web. This makes ransomware protection… Continue Reading What to Consider when Implementing DRaaS for ransomware protection - Looking to set up disaster recovery as a service (DRaaS) to protect your critical systems from ransomware? In this blog, we’ve compiled a list of questions IT managers need to… Continue Reading
What to Consider when Implementing DRaaS for ransomware protection - Looking to set up disaster recovery as a service (DRaaS) to protect your critical systems from ransomware? In this blog, we’ve compiled a list of questions IT managers need to… Continue Reading Downtime Cost: How to Calculate and Minimize it - Downtime costs are more than lost revenue. It includes reputational damage, SLA fines, recovery, and PR costs. Learn how to calculate IT downtime costs, and the best practices to minimize… Continue Reading
Downtime Cost: How to Calculate and Minimize it - Downtime costs are more than lost revenue. It includes reputational damage, SLA fines, recovery, and PR costs. Learn how to calculate IT downtime costs, and the best practices to minimize… Continue Reading Disaster Recovery as a Service (DRaaS) or On-Site DR Appliance? - Disaster Recovery-as-a-Service (DRaaS) vs On-Site DR Appliance: Serverless recovery where service provider is responsible for management versus a secondary site that delivers faster recovery and helps with compliance. Which one… Continue Reading
Disaster Recovery as a Service (DRaaS) or On-Site DR Appliance? - Disaster Recovery-as-a-Service (DRaaS) vs On-Site DR Appliance: Serverless recovery where service provider is responsible for management versus a secondary site that delivers faster recovery and helps with compliance. Which one… Continue Reading FC SAN vs iSCSI SAN: What’s the Difference? - Differentiate between Fibre Channel (FC) SAN vs iSCSI SAN: which is suitable for which use-case, and what are the pros and cons of each. Continue Reading
FC SAN vs iSCSI SAN: What’s the Difference? - Differentiate between Fibre Channel (FC) SAN vs iSCSI SAN: which is suitable for which use-case, and what are the pros and cons of each. Continue Reading What is BCDR – A Guide to Business Continuity and Disaster Recovery - A business continuity and disaster recovery (BCDR) plan protects an organization from disruption, downtime, and data loss in the event of a disaster such as ransomware attack, human error, accidental/malicious… Continue Reading
What is BCDR – A Guide to Business Continuity and Disaster Recovery - A business continuity and disaster recovery (BCDR) plan protects an organization from disruption, downtime, and data loss in the event of a disaster such as ransomware attack, human error, accidental/malicious… Continue Reading NAS Security: What to Expect and How to Secure your NAS - Qlocker, Deadbolt, and other ransomware target NAS appliances. Learn what to expect and how to protect your file-level unstructured data from cyberthreats. Continue Reading
NAS Security: What to Expect and How to Secure your NAS - Qlocker, Deadbolt, and other ransomware target NAS appliances. Learn what to expect and how to protect your file-level unstructured data from cyberthreats. Continue Reading Log Archiving: What Challenges to Expect and How to Overcome Them - Challenges with log archiving, how to overcome them, and how to build a secure, low power, low carbon, zero ransomware log archiving system. Continue Reading
Log Archiving: What Challenges to Expect and How to Overcome Them - Challenges with log archiving, how to overcome them, and how to build a secure, low power, low carbon, zero ransomware log archiving system. Continue Reading Physical vs Virtual Backup Appliances – A Comparison - Physical vs virtual backup appliances: High performance secondary site versus portable and scalable virtual machine - which one is best for your business? Continue Reading
Physical vs Virtual Backup Appliances – A Comparison - Physical vs virtual backup appliances: High performance secondary site versus portable and scalable virtual machine - which one is best for your business? Continue Reading Cloud Disaster Recovery vs On-Premise – Which is Best? - Cybersecurity threats are aimed at accessing an organization's sensitive data. In 2021, cyberattacks were at an all-time high, and they will not be slowing down any time soon. Continue Reading
Cloud Disaster Recovery vs On-Premise – Which is Best? - Cybersecurity threats are aimed at accessing an organization's sensitive data. In 2021, cyberattacks were at an all-time high, and they will not be slowing down any time soon. Continue Reading What you need to know about cybersecurity threats in 2022 - Cybersecurity threats are aimed at accessing an organization's sensitive data. In 2021, cyberattacks were at an all-time high, and they will not be slowing down any time soon. Continue Reading
What you need to know about cybersecurity threats in 2022 - Cybersecurity threats are aimed at accessing an organization's sensitive data. In 2021, cyberattacks were at an all-time high, and they will not be slowing down any time soon. Continue Reading How to add air-gapping and immutability to Veeam backup appliance - Even with a Veeam backup appliance, if your Veeam backups are accessible via the production network, then your backup and DR is vulnerable. Learn how to add air-gapping and immutability… Continue Reading
How to add air-gapping and immutability to Veeam backup appliance - Even with a Veeam backup appliance, if your Veeam backups are accessible via the production network, then your backup and DR is vulnerable. Learn how to add air-gapping and immutability… Continue Reading Backup and Disaster Recovery Best Practices for Dental Offices - Dental clinics need to protect patient dental records and comply with HIPAA using backup and DR. Here are some best practices that can help with the process. Continue Reading
Backup and Disaster Recovery Best Practices for Dental Offices - Dental clinics need to protect patient dental records and comply with HIPAA using backup and DR. Here are some best practices that can help with the process. Continue Reading What is Automated Backup and Why Should You Use it - Automated backups enable you to automate backup and recovery for critical workloads. Learn what automated backups are, and how to use them effectively in this blog. Continue Reading
What is Automated Backup and Why Should You Use it - Automated backups enable you to automate backup and recovery for critical workloads. Learn what automated backups are, and how to use them effectively in this blog. Continue Reading Agentless Backups vs Agent Based Backups: Which is Best? - Agentless-backups versus agent based backups: what's the difference between the two? which costs more? which is more effective? Find the answers and more in this blog. Continue Reading
Agentless Backups vs Agent Based Backups: Which is Best? - Agentless-backups versus agent based backups: what's the difference between the two? which costs more? which is more effective? Find the answers and more in this blog. Continue Reading NAS vs Cloud Storage – Which is Best for Your Hybrid Workforce - NAS vs cloud storage: what’s the difference between the two storage technologies and which one should you use for your hybrid workforce? Continue Reading
NAS vs Cloud Storage – Which is Best for Your Hybrid Workforce - NAS vs cloud storage: what’s the difference between the two storage technologies and which one should you use for your hybrid workforce? Continue Reading What Ransomware Taught us in 2021 - In 2021, ransomware attacks grew in number, scale, and complexity disrupting healthcare, education, and more. Here's what we learned from ransomware in 2021. Continue Reading
What Ransomware Taught us in 2021 - In 2021, ransomware attacks grew in number, scale, and complexity disrupting healthcare, education, and more. Here's what we learned from ransomware in 2021. Continue Reading Ransomware Recovery: How to Plan for and Recover from Ransomware - A complete guide to ransomware recovery: how to recover ransomware encrypted files, how backup and DR mitigate the risk of ransomware attacks and more. Continue Reading
Ransomware Recovery: How to Plan for and Recover from Ransomware - A complete guide to ransomware recovery: how to recover ransomware encrypted files, how backup and DR mitigate the risk of ransomware attacks and more. Continue Reading Ransomware Attacks Report 2021 - A comprehensive report of notable ransomware attacks, the most targeted industry, and the new ransomware groups per quarter. Continue Reading
Ransomware Attacks Report 2021 - A comprehensive report of notable ransomware attacks, the most targeted industry, and the new ransomware groups per quarter. Continue Reading 8 Things You Can Do to Protect Your Endpoints from Ransomware - Ransomware looks for vulnerabilities and exploits them to attack your network. In this blog, we share 8 things you can do to protect your endpoints from cyber-attacks and ensure disruption-free… Continue Reading
8 Things You Can Do to Protect Your Endpoints from Ransomware - Ransomware looks for vulnerabilities and exploits them to attack your network. In this blog, we share 8 things you can do to protect your endpoints from cyber-attacks and ensure disruption-free… Continue Reading SAN vs NAS vs DAS – A Closer Look - What's the difference between SAN vs NAS vs DAS? What are the advantages of each? When should you use them? And which data storage platform should you choose for your… Continue Reading
SAN vs NAS vs DAS – A Closer Look - What's the difference between SAN vs NAS vs DAS? What are the advantages of each? When should you use them? And which data storage platform should you choose for your… Continue Reading Meet Cyber Insurance Requirements with Immutable Backups - Cyber insurance protects your business from liability in the event of a cyber-attack. In order to satisfy cyber insurance requirements, you need to set up regular backups, air-gapping, and immutability… Continue Reading
Meet Cyber Insurance Requirements with Immutable Backups - Cyber insurance protects your business from liability in the event of a cyber-attack. In order to satisfy cyber insurance requirements, you need to set up regular backups, air-gapping, and immutability… Continue Reading Best Cloud Backup: Veeam Cloud Connect to Azure - It's risky to store all your data at one place because your business becomes vulnerable to ransomware attacks. Cloud backup & DR offers an affordable and reliable solution to that… Continue Reading
Best Cloud Backup: Veeam Cloud Connect to Azure - It's risky to store all your data at one place because your business becomes vulnerable to ransomware attacks. Cloud backup & DR offers an affordable and reliable solution to that… Continue Reading On-Prem vs. Cloud Solutions: Which is Best for Your Business? - Learn the difference between on-premises vs. cloud infrastructure so that you can choose the right infrastructure for your business that supports your day-to-day operations within your budget. Continue Reading
On-Prem vs. Cloud Solutions: Which is Best for Your Business? - Learn the difference between on-premises vs. cloud infrastructure so that you can choose the right infrastructure for your business that supports your day-to-day operations within your budget. Continue Reading Keep Your Data Safe: S3 Object Lockdown for Compliance and Security - Learn more about S3 object lockdown, why should you use it, and how you can add it to your existing environment(s) to protect your critical object-level workloads from ransomware attacks. Continue Reading
Keep Your Data Safe: S3 Object Lockdown for Compliance and Security - Learn more about S3 object lockdown, why should you use it, and how you can add it to your existing environment(s) to protect your critical object-level workloads from ransomware attacks. Continue Reading Protecting Video Surveillance Storage: How To Keep Video Data Safe - Learn why do you need to protect your video surveillance storage systems and how to do so using backup and disaster recovery solutions with air-gapping, immutability, and snapshots. Continue Reading
Protecting Video Surveillance Storage: How To Keep Video Data Safe - Learn why do you need to protect your video surveillance storage systems and how to do so using backup and disaster recovery solutions with air-gapping, immutability, and snapshots. Continue Reading How safe is tape storage against ransomware? - Is tape storage safe from ransomware attacks? Is it the same as air-gapped nodes? And can you use tape storage for backup and recovery? Find the answers and more in… Continue Reading
How safe is tape storage against ransomware? - Is tape storage safe from ransomware attacks? Is it the same as air-gapped nodes? And can you use tape storage for backup and recovery? Find the answers and more in… Continue Reading Choosing the Right Data Backup Solution for Educational Sector - Educational institutes aren't safe from ransomware attacks. In this blog post, we explore the different data backup solutions that schools, colleges, and universities can implement to protect their administrative and… Continue Reading
Choosing the Right Data Backup Solution for Educational Sector - Educational institutes aren't safe from ransomware attacks. In this blog post, we explore the different data backup solutions that schools, colleges, and universities can implement to protect their administrative and… Continue Reading A Definitive Guide to Hybrid Cloud Computing - What is hybrid cloud? Why should you use it? How to implement a hybrid cloud architecture? Find the answers and more in this blog post. Continue Reading
A Definitive Guide to Hybrid Cloud Computing - What is hybrid cloud? Why should you use it? How to implement a hybrid cloud architecture? Find the answers and more in this blog post. Continue Reading 11 Reasons to Choose StoneFly Azure Cloud Storage for Your Business - Here are 11 reasons why Azure cloud storage is a better choice for your business and how StoneFly uses the platform to deliver enterprise storage capabilities with integrated data services. Continue Reading
11 Reasons to Choose StoneFly Azure Cloud Storage for Your Business - Here are 11 reasons why Azure cloud storage is a better choice for your business and how StoneFly uses the platform to deliver enterprise storage capabilities with integrated data services. Continue Reading Finding the Right Data Backup Strategy: 3-2-1 vs 3-2-1-1-0 vs 4-3-2 - Differentiate between 3-2-1 vs 3-2-1-1-0 vs 4-3-2 backup strategies and learn which backup strategy works best for your organization. Continue Reading
Finding the Right Data Backup Strategy: 3-2-1 vs 3-2-1-1-0 vs 4-3-2 - Differentiate between 3-2-1 vs 3-2-1-1-0 vs 4-3-2 backup strategies and learn which backup strategy works best for your organization. Continue Reading Cloud Backup – A Comprehensive Overview - What is cloud backup, how can you backup your data to the cloud, and how can you use cloud backups to restore data and restore business operations. Find the answers… Continue Reading
Cloud Backup – A Comprehensive Overview - What is cloud backup, how can you backup your data to the cloud, and how can you use cloud backups to restore data and restore business operations. Find the answers… Continue Reading Simplify your Data Center with a Unified Veeam Ready Appliance - Read how you can simplify your IT infrastructure by replacing multiple dedicated servers with our unified Veeam ready appliance (DR365V) - in turn, reducing costs and simplifying management. Continue Reading
Simplify your Data Center with a Unified Veeam Ready Appliance - Read how you can simplify your IT infrastructure by replacing multiple dedicated servers with our unified Veeam ready appliance (DR365V) - in turn, reducing costs and simplifying management. Continue Reading What is virtual SAN (vSAN) and why is it better than traditional SAN? - Learn everything you need to know about virtual SAN (vSAN) from its benefits, uses, features & why it's better than traditional SAN in this blog. Continue Reading
What is virtual SAN (vSAN) and why is it better than traditional SAN? - Learn everything you need to know about virtual SAN (vSAN) from its benefits, uses, features & why it's better than traditional SAN in this blog. Continue Reading Backup versus Replication – What’s the Difference - This article takes a look at data backup and data replication, two solutions that are very similar but have distinct differences. Continue Reading
Backup versus Replication – What’s the Difference - This article takes a look at data backup and data replication, two solutions that are very similar but have distinct differences. Continue Reading Backups aren’t Enough – Here’s Why Air-Gapping and Immutability are Necessary - Most IT professionals think about backups when they're considering data security, but the truth is that this isn't enough. Data can still be breached with a backup. Continue Reading
Backups aren’t Enough – Here’s Why Air-Gapping and Immutability are Necessary - Most IT professionals think about backups when they're considering data security, but the truth is that this isn't enough. Data can still be breached with a backup. Continue Reading What Is A Software Storage Solution (SDS)? Introduction & Benefits - Software defined storage is a term that has been making the rounds in recent years. It’s not entirely new, but it’s an evolving concept and as such, there are still… Continue Reading
What Is A Software Storage Solution (SDS)? Introduction & Benefits - Software defined storage is a term that has been making the rounds in recent years. It’s not entirely new, but it’s an evolving concept and as such, there are still… Continue Reading Business Continuity with Veeam Replication, Failover & Failback - You can leverage Veeam replication, failover, and failback to ensure business continuity and reduce RTOs and RPOs. Learn more about how the Veeam replication capabilities work and how StoneFly solutions… Continue Reading
Business Continuity with Veeam Replication, Failover & Failback - You can leverage Veeam replication, failover, and failback to ensure business continuity and reduce RTOs and RPOs. Learn more about how the Veeam replication capabilities work and how StoneFly solutions… Continue Reading Remote Office/Branch Office Backup & DR: How to do it right - In this blog post, explore remote office/branch office backup and recovery challenges, how to overcome them, and how StoneFly backup & DR solutions help. Continue Reading
Remote Office/Branch Office Backup & DR: How to do it right - In this blog post, explore remote office/branch office backup and recovery challenges, how to overcome them, and how StoneFly backup & DR solutions help. Continue Reading 5 ways to protect your servers from ransomware attack - In this blog post, we’ll share 5 things that you can do to prevent successful ransomware attacks. Considering how frequent ransomware attacks target a business, if you aren’t prepared, your… Continue Reading
5 ways to protect your servers from ransomware attack - In this blog post, we’ll share 5 things that you can do to prevent successful ransomware attacks. Considering how frequent ransomware attacks target a business, if you aren’t prepared, your… Continue Reading How StoneFly and Veeam offer the best ransomware protection - Find out what makes StoneFly’s Veeam-ready backup and DR solution different than most mainstream solutions – and how it offers the best ransomware protection Continue Reading
How StoneFly and Veeam offer the best ransomware protection - Find out what makes StoneFly’s Veeam-ready backup and DR solution different than most mainstream solutions – and how it offers the best ransomware protection Continue Reading How to update your StoneFusion & SCVM to the latest version - This blog shares the process of updating StoneFly’s patented storage OS (StoneFusion & SCVM) to the latest version. Each new update brings new features, bug fixes (if any), and patches… Continue Reading
How to update your StoneFusion & SCVM to the latest version - This blog shares the process of updating StoneFly’s patented storage OS (StoneFusion & SCVM) to the latest version. Each new update brings new features, bug fixes (if any), and patches… Continue Reading Protect your servers from ransomware attacks with backup & DR - The most effective way to ransomware-proof your servers is by using backup and DR. Typical practices like offsite storage, tape archiving, or anti-malware software just won’t cut it. Read why… Continue Reading
Protect your servers from ransomware attacks with backup & DR - The most effective way to ransomware-proof your servers is by using backup and DR. Typical practices like offsite storage, tape archiving, or anti-malware software just won’t cut it. Read why… Continue Reading Why should you worry about ransomware attacks? - Ransomware attacks are dangerous. They can cost you money, your reputation, and even your business. Read this blog to find out why ransomware should worry you and why you should… Continue Reading
Why should you worry about ransomware attacks? - Ransomware attacks are dangerous. They can cost you money, your reputation, and even your business. Read this blog to find out why ransomware should worry you and why you should… Continue Reading How to setup NAS backup repository for Veeam backup software - Learn how to create NFS or CIFS/SMB NAS volumes using StoneFly storage concentrator (SCVM) and configure them as target backup repositories for Veeam Availability suite version 10. Continue Reading
How to setup NAS backup repository for Veeam backup software - Learn how to create NFS or CIFS/SMB NAS volumes using StoneFly storage concentrator (SCVM) and configure them as target backup repositories for Veeam Availability suite version 10. Continue Reading How to Setup & Use StoneFly’s Free Data Migration Software - Learn how to install, setup, and use StoneFly’s free data migration software and migrate your unstructured data volumes effortlessly. Continue Reading
How to Setup & Use StoneFly’s Free Data Migration Software - Learn how to install, setup, and use StoneFly’s free data migration software and migrate your unstructured data volumes effortlessly. Continue Reading How Clustered HCI Appliances Ensure Hyper-Availability - What makes StoneFly TwinHCI systems the best high availability clustered HCI appliance solution in the market? Find the answer to this question and more in this blog post. Continue Reading
How Clustered HCI Appliances Ensure Hyper-Availability - What makes StoneFly TwinHCI systems the best high availability clustered HCI appliance solution in the market? Find the answer to this question and more in this blog post. Continue Reading What makes converged storage the best data storage infrastructure - In this blog post, we take a look at converged storage infrastructure, what is it, how it works, how can you use it effectively, and what makes StoneFly USO the… Continue Reading
What makes converged storage the best data storage infrastructure - In this blog post, we take a look at converged storage infrastructure, what is it, how it works, how can you use it effectively, and what makes StoneFly USO the… Continue Reading AWS Hybrid Cloud Storage for Media and Entertainment Industry - AWS hybrid cloud storage technology allows users to share data and work in collaboration from multiple locations. StoneFly cloud storage gateway enables you to build a data life cycle which… Continue Reading
AWS Hybrid Cloud Storage for Media and Entertainment Industry - AWS hybrid cloud storage technology allows users to share data and work in collaboration from multiple locations. StoneFly cloud storage gateway enables you to build a data life cycle which… Continue Reading Veeam-Ready Appliance with Immutable / WORM Storage - StoneFly Veeam-ready appliance enables users to provision WORM storage repositories for secure & compliant backup data storage. Learn more about the feature in this blog post. Continue Reading
Veeam-Ready Appliance with Immutable / WORM Storage - StoneFly Veeam-ready appliance enables users to provision WORM storage repositories for secure & compliant backup data storage. Learn more about the feature in this blog post. Continue Reading Enhance Your AWS Cloud Storage Experience with StoneFly - Amazon cloud storage is the single place for whatever data your business needs to store, manage and analyze. And StoneFly cloud storage gateway gives you the tools to fully leverage… Continue Reading
Enhance Your AWS Cloud Storage Experience with StoneFly - Amazon cloud storage is the single place for whatever data your business needs to store, manage and analyze. And StoneFly cloud storage gateway gives you the tools to fully leverage… Continue Reading Best VMware Live VM Migration Solution in the Market - VM migration is typically a disruptive process. Many businesses need an alternative to this disruptive migration process. To help with that, we’ve introduced live VM migration solutions that include a… Continue Reading
Best VMware Live VM Migration Solution in the Market - VM migration is typically a disruptive process. Many businesses need an alternative to this disruptive migration process. To help with that, we’ve introduced live VM migration solutions that include a… Continue Reading 8 Best Practices of Disaster Recovery - In this article we are going to talk about the best practices of DR; how can you effectively plan for it, set it up and test it. Continue Reading
8 Best Practices of Disaster Recovery - In this article we are going to talk about the best practices of DR; how can you effectively plan for it, set it up and test it. Continue Reading Coronavirus & Ransomware Infection – What’s the Connection? - Opportunistic scammers are using Coronavirus as an excuse to infect your storage infrastructure with ransomware attacks using phishing emails. One wrong click can lead to data loss, data breach, or… Continue Reading
Coronavirus & Ransomware Infection – What’s the Connection? - Opportunistic scammers are using Coronavirus as an excuse to infect your storage infrastructure with ransomware attacks using phishing emails. One wrong click can lead to data loss, data breach, or… Continue Reading Business Continuity & Disaster Recovery: What’s the difference? - In this article, we differentiate business continuity from disaster recovery and discuss how StoneFly DR solutions can play an integral part in enterprise business continuity. Continue Reading
Business Continuity & Disaster Recovery: What’s the difference? - In this article, we differentiate business continuity from disaster recovery and discuss how StoneFly DR solutions can play an integral part in enterprise business continuity. Continue Reading Disaster Recovery Challenges & Solutions: A Brief Overview - What are the challenges data owners have to face when setting up disaster recovery and how can they overcome them? This is the question we’ll be tackling in this article. Continue Reading
Disaster Recovery Challenges & Solutions: A Brief Overview - What are the challenges data owners have to face when setting up disaster recovery and how can they overcome them? This is the question we’ll be tackling in this article. Continue Reading GDPR Compliance & Its Importance for an Organization - What is GDPR compliance? What does it mean to your organization? Why is it important to achieve it? And how can StoneFly and Veeam help with GDPR compliance? Continue Reading
GDPR Compliance & Its Importance for an Organization - What is GDPR compliance? What does it mean to your organization? Why is it important to achieve it? And how can StoneFly and Veeam help with GDPR compliance? Continue Reading Considerations to Make While Planning NAS in AWS Cloud - This blog includes an overview of key deployment considerations including NAS in AWS cloud instance size, networking requirements and memory. Continue Reading
Considerations to Make While Planning NAS in AWS Cloud - This blog includes an overview of key deployment considerations including NAS in AWS cloud instance size, networking requirements and memory. Continue Reading Taking a Closer Look at Cloud Storage Gateways - What are cloud storage gateways? When should you use them? And what makes StoneFly Smart cloud storage gateway the best in the market? Find answers to these questions and more… Continue Reading
Taking a Closer Look at Cloud Storage Gateways - What are cloud storage gateways? When should you use them? And what makes StoneFly Smart cloud storage gateway the best in the market? Find answers to these questions and more… Continue Reading StoneFly 2019 Review: New Products, Features & More - 2019 was a busy year for us. We introduced additional compliance and security features to our hardware and software solutions. We also introduced solutions for MSPs along with data migration… Continue Reading
StoneFly 2019 Review: New Products, Features & More - 2019 was a busy year for us. We introduced additional compliance and security features to our hardware and software solutions. We also introduced solutions for MSPs along with data migration… Continue Reading Another Review – Another Award for Our Storage Operating System - FinancesOnline, a leading business software review platform awarded our enterprise storage operating system the 2019 Rising Star and Premium Usability awards in their recent review. Their survey concluded our user… Continue Reading
Another Review – Another Award for Our Storage Operating System - FinancesOnline, a leading business software review platform awarded our enterprise storage operating system the 2019 Rising Star and Premium Usability awards in their recent review. Their survey concluded our user… Continue Reading Medical Record Storage and PACS Archiving: Challenges & StoneFly’s Solutions - This article explores PACS, the challenges with medical record storage and PACS archiving, what kind of data archive solutions can healthcare organizations employ for medical record storage and PACS Archiving;… Continue Reading
Medical Record Storage and PACS Archiving: Challenges & StoneFly’s Solutions - This article explores PACS, the challenges with medical record storage and PACS archiving, what kind of data archive solutions can healthcare organizations employ for medical record storage and PACS Archiving;… Continue Reading Data Center Hardware Overview: Disaggregated HA Appliances - This blog is the fourth in the series of blogs that explain StoneFly’s innovative data storage appliance hardware architecture. In this blog, explore the appliance architecture and key components of… Continue Reading
Data Center Hardware Overview: Disaggregated HA Appliances - This blog is the fourth in the series of blogs that explain StoneFly’s innovative data storage appliance hardware architecture. In this blog, explore the appliance architecture and key components of… Continue Reading Data Center Hardware Overview: Scale Out Appliances - This blog is the third in the series of blogs that explore StoneFly’s innovative storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and the… Continue Reading
Data Center Hardware Overview: Scale Out Appliances - This blog is the third in the series of blogs that explore StoneFly’s innovative storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and the… Continue Reading Data Center Hardware Overview: Dual Node Shared Nothing - This blog is the second in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading
Data Center Hardware Overview: Dual Node Shared Nothing - This blog is the second in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading Data Center Hardware Overview: Integrated Appliance - This blog is the first in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading
Data Center Hardware Overview: Integrated Appliance - This blog is the first in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading What makes StoneFly SSO NAS Appliances Ransomware-Proof? - This article explores the vulnerabilities of traditional NAS systems and what makes them prone to data loss. The article also provides insight on what makes StoneFly SSO NAS appliances the… Continue Reading
What makes StoneFly SSO NAS Appliances Ransomware-Proof? - This article explores the vulnerabilities of traditional NAS systems and what makes them prone to data loss. The article also provides insight on what makes StoneFly SSO NAS appliances the… Continue Reading StoneFly & a Free Cup of Coffee Waiting for You at VMworld 2019 US - We're at VMworld 2019 and we're waiting to talk to you about your enterprise projects, problems, and challenges. We've got the solutions, the expertise, and a hot cup of coffee… Continue Reading
StoneFly & a Free Cup of Coffee Waiting for You at VMworld 2019 US - We're at VMworld 2019 and we're waiting to talk to you about your enterprise projects, problems, and challenges. We've got the solutions, the expertise, and a hot cup of coffee… Continue Reading Public versus Private: Which Cloud is Best for Enterprise Backups? - Enterprises have to make a decision when it comes to selecting which cloud is the best for their use-case either public or private. It tends to be a difficult decision.… Continue Reading
Public versus Private: Which Cloud is Best for Enterprise Backups? - Enterprises have to make a decision when it comes to selecting which cloud is the best for their use-case either public or private. It tends to be a difficult decision.… Continue Reading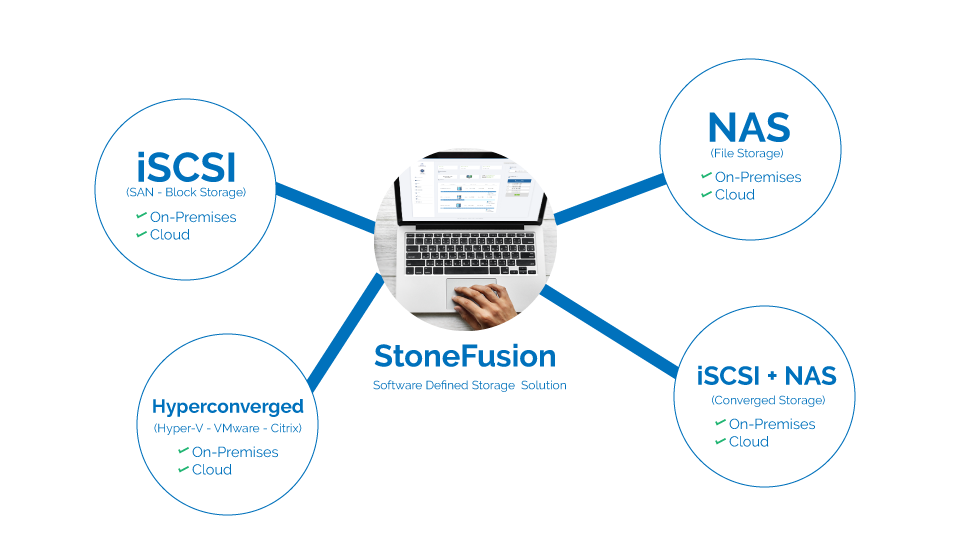 iSCSI, NAS, Hyperconverged: Manage All with Award-Winning Software - StoneFusion is the ultimate software defined storage solution capable of facilitating NAS, iSCSI, converged, and hyperconverged enterprise workloads. StoneFusion enables data service integration and cloud storage integration making data storage… Continue Reading
iSCSI, NAS, Hyperconverged: Manage All with Award-Winning Software - StoneFusion is the ultimate software defined storage solution capable of facilitating NAS, iSCSI, converged, and hyperconverged enterprise workloads. StoneFusion enables data service integration and cloud storage integration making data storage… Continue Reading Best Use-Case of Enterprise Cloud Storage Technology - Enterprise cloud is used for storage, running enterprise workloads, archiving data, and backups; but what is the best use-case for it? This article answers that question and provides insight on… Continue Reading
Best Use-Case of Enterprise Cloud Storage Technology - Enterprise cloud is used for storage, running enterprise workloads, archiving data, and backups; but what is the best use-case for it? This article answers that question and provides insight on… Continue Reading Best Way to Remove Single Point of Failure from Your Storage Infrastructure - Business continuity is important for every industry. Single point of failure in data storage systems risk disruption and disruption is very costly. In this blog learn what’s single point of… Continue Reading
Best Way to Remove Single Point of Failure from Your Storage Infrastructure - Business continuity is important for every industry. Single point of failure in data storage systems risk disruption and disruption is very costly. In this blog learn what’s single point of… Continue Reading Cloud Storage Adoption: Challenges & Solutions - Enterprise cloud storage integration can be challenging since they have to consider costs, bandwidth usage, integration complexities and other similar questions. StoneFly helps meet these challenges and deliver more value… Continue Reading
Cloud Storage Adoption: Challenges & Solutions - Enterprise cloud storage integration can be challenging since they have to consider costs, bandwidth usage, integration complexities and other similar questions. StoneFly helps meet these challenges and deliver more value… Continue Reading Ransomware Attack Targets City Departments of Baltimore - Baltimore city services were disrupted by Robinhood ransomware attack shutting down most of its servers. Due to not having an effective backup, they expect high volume of data loss. StoneFly… Continue Reading
Ransomware Attack Targets City Departments of Baltimore - Baltimore city services were disrupted by Robinhood ransomware attack shutting down most of its servers. Due to not having an effective backup, they expect high volume of data loss. StoneFly… Continue ReadingDo you want scalable architecture? - Ask yourself, will it not be amazing if you get automated scalable solution? If you don’t have to waste your money on extra racks of storage. Well, Of course for… Continue Reading
 Exploring StoneFly Enterprise Cloud Storage in Azure - In order to facilitate businesses and make data storage easier, StoneFly offers Enterprise Cloud Storage in Azure. In this article we briefly explore what makes StoenFly Cloud Storage Solutions different… Continue Reading
Exploring StoneFly Enterprise Cloud Storage in Azure - In order to facilitate businesses and make data storage easier, StoneFly offers Enterprise Cloud Storage in Azure. In this article we briefly explore what makes StoenFly Cloud Storage Solutions different… Continue Reading Surveillance Video Archive: Enterprise Requirements & StoneFly Archiving Solutions - Compliance regulations need businesses to retain surveillance video archives for months or even years. What kind of technology and features should businesses look-for for their surveillance video archives? And what… Continue Reading
Surveillance Video Archive: Enterprise Requirements & StoneFly Archiving Solutions - Compliance regulations need businesses to retain surveillance video archives for months or even years. What kind of technology and features should businesses look-for for their surveillance video archives? And what… Continue Reading Secure, Reliable & Simple Email Archiving for the Enterprise - Email archiving reduces cost and enables IT administrators to effectively protect email data. This article explores email archiving and why businesses should set it up. The article also explores how… Continue Reading
Secure, Reliable & Simple Email Archiving for the Enterprise - Email archiving reduces cost and enables IT administrators to effectively protect email data. This article explores email archiving and why businesses should set it up. The article also explores how… Continue Reading Demystifying Cloud Archiving & its Role in Business Environments - What are the challenges that businesses face without cloud archiving? What really is cloud archiving and what are its benefits? This article answers these questions and introduces the idea that… Continue Reading
Demystifying Cloud Archiving & its Role in Business Environments - What are the challenges that businesses face without cloud archiving? What really is cloud archiving and what are its benefits? This article answers these questions and introduces the idea that… Continue Reading What’s a Backup Gateway and how can it solve data protection challenges - Businesses running storage infrastructures always find themselves perplexed about the decision of setting up dedicated backup infrastructure; mostly due to the cost implications. In this article explore how StoneFly BG365™… Continue Reading
What’s a Backup Gateway and how can it solve data protection challenges - Businesses running storage infrastructures always find themselves perplexed about the decision of setting up dedicated backup infrastructure; mostly due to the cost implications. In this article explore how StoneFly BG365™… Continue Reading Benefits of Using the StoneFly Cloud Archiving Solution - The StoneFly Cloud Archiving solution provides a low-cost storage service built for data archival. One of the benefits of the Cloud Archiving solution is you can start archiving your storage… Continue Reading
Benefits of Using the StoneFly Cloud Archiving Solution - The StoneFly Cloud Archiving solution provides a low-cost storage service built for data archival. One of the benefits of the Cloud Archiving solution is you can start archiving your storage… Continue Reading What have we been doing in 2018 - In 2018, StoneFly introduced three products to our diverse range of enterprise products: CDR365, StoneWAN and the VSO™ appliance series. This article reviews 2018 and provides insight about these three… Continue Reading
What have we been doing in 2018 - In 2018, StoneFly introduced three products to our diverse range of enterprise products: CDR365, StoneWAN and the VSO™ appliance series. This article reviews 2018 and provides insight about these three… Continue Reading Transforming Traditional Data centers with the StoneFly USS Hyper-converged Appliance - The StoneFly USS Hyperconverged appliance combines server, networking and storage in as little as 3U of Rackspace and presents a solution for traditional datacenters to run any application or consolidate… Continue Reading
Transforming Traditional Data centers with the StoneFly USS Hyper-converged Appliance - The StoneFly USS Hyperconverged appliance combines server, networking and storage in as little as 3U of Rackspace and presents a solution for traditional datacenters to run any application or consolidate… Continue Reading Short Story: The Relation between Cloud Storage and Cloud Backup - The term “Cloud” has become mainstream but there’s still quite a bit of confusion on the application of the cloud. In this article, explore the difference between cloud storage and… Continue Reading
Short Story: The Relation between Cloud Storage and Cloud Backup - The term “Cloud” has become mainstream but there’s still quite a bit of confusion on the application of the cloud. In this article, explore the difference between cloud storage and… Continue Reading Backup and Archiving with the Smart Cloud Gateway - Smart Cloud Gateway is a service that connects your on-premise appliance with cloud-based storage. You can use the Smart Cloud Gateway to store data in Microsoft Azure Cloud, Amazon AWS,… Continue Reading
Backup and Archiving with the Smart Cloud Gateway - Smart Cloud Gateway is a service that connects your on-premise appliance with cloud-based storage. You can use the Smart Cloud Gateway to store data in Microsoft Azure Cloud, Amazon AWS,… Continue Reading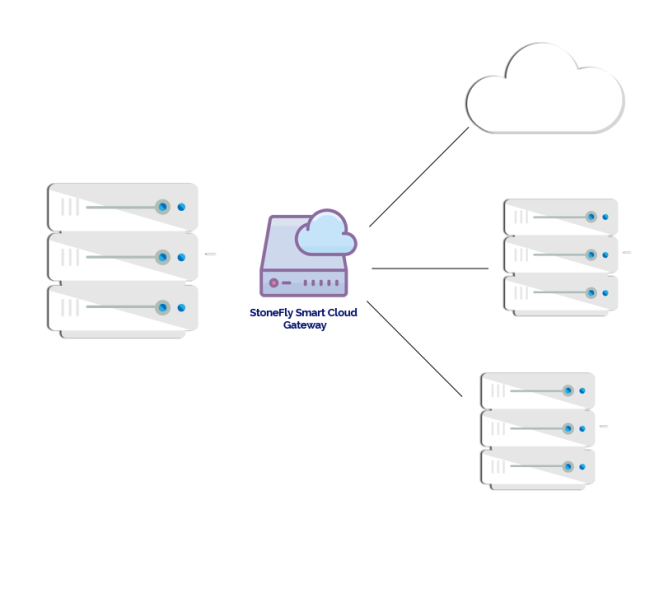 Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading
Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading 8th Generation DR365 Backup and Disaster Recovery Appliances - The 8th Generation of the StoneFly DR365 Backup and Disaster Recovery Appliances is the latest update of the StoneFly comprehensive data protection and disaster recovery solutions. The 8th generation of… Continue Reading
8th Generation DR365 Backup and Disaster Recovery Appliances - The 8th Generation of the StoneFly DR365 Backup and Disaster Recovery Appliances is the latest update of the StoneFly comprehensive data protection and disaster recovery solutions. The 8th generation of… Continue Reading Protecting AWS Workloads with Veeam backup & replication to StoneFly Cloud - Veeam backup & replication to StoneFly Cloud provides a backup and disaster recovery for your Amazon EC2 instances. It is gives you the ability to automatically backup and recover data… Continue Reading
Protecting AWS Workloads with Veeam backup & replication to StoneFly Cloud - Veeam backup & replication to StoneFly Cloud provides a backup and disaster recovery for your Amazon EC2 instances. It is gives you the ability to automatically backup and recover data… Continue Reading Affordable Data Backup in Microsoft Azure and AWS Cloud - In our latest webinar “Affordable Data Backup in Microsoft Azure and AWS Cloud”, we discussed StoneFly CDR365™ - cloud backup and disaster recovery solution. In this blog post, we will… Continue Reading
Affordable Data Backup in Microsoft Azure and AWS Cloud - In our latest webinar “Affordable Data Backup in Microsoft Azure and AWS Cloud”, we discussed StoneFly CDR365™ - cloud backup and disaster recovery solution. In this blog post, we will… Continue Reading Backup your Data to Microsoft Azure and Amazon AWS with CDR365 - CDR365 is StoneFly’s backup solution that is built for the cloud. It allows you to backup your data to major public clouds like Microsoft Azure and Amazon AWS. You can… Continue Reading
Backup your Data to Microsoft Azure and Amazon AWS with CDR365 - CDR365 is StoneFly’s backup solution that is built for the cloud. It allows you to backup your data to major public clouds like Microsoft Azure and Amazon AWS. You can… Continue Reading Rapid recovery of large data sets with flash array backup and DR appliance - StoneFly and Veeam are delivering innovation to customers in the storage and the backup industries, that is simplifying operations, increasing availability and driving net new agility to organizations. Read this… Continue Reading
Rapid recovery of large data sets with flash array backup and DR appliance - StoneFly and Veeam are delivering innovation to customers in the storage and the backup industries, that is simplifying operations, increasing availability and driving net new agility to organizations. Read this… Continue Reading Leveraging Purpose Built Cloud Service Provider for Backup and Disaster Recovery - Backup and disaster recovery top the list of applications that companies hope to migrate to the cloud. Storing backup data offsite, retaining it for long-term, scaling up, and testing and… Continue Reading
Leveraging Purpose Built Cloud Service Provider for Backup and Disaster Recovery - Backup and disaster recovery top the list of applications that companies hope to migrate to the cloud. Storing backup data offsite, retaining it for long-term, scaling up, and testing and… Continue Reading VSO™ Appliance: Affordable Data Storage, Backup & Disaster Recovery - Data storage, backup and disaster recovery are costly but important for IT driven businesses. In order to facilitate budget conscious businesses, StoneFly offers the VSO™ appliance series comprising of affordable… Continue Reading
VSO™ Appliance: Affordable Data Storage, Backup & Disaster Recovery - Data storage, backup and disaster recovery are costly but important for IT driven businesses. In order to facilitate budget conscious businesses, StoneFly offers the VSO™ appliance series comprising of affordable… Continue Reading Tech or Treat: StoneFly’s Special Halloween offers - This Halloween, StoneFly is joining the fun and offering a number of treats for our Halloween enthusiastic IT administrators. In this article, explore the special Halloween offers that we have… Continue Reading
Tech or Treat: StoneFly’s Special Halloween offers - This Halloween, StoneFly is joining the fun and offering a number of treats for our Halloween enthusiastic IT administrators. In this article, explore the special Halloween offers that we have… Continue Reading Microsoft Office 365 Backup – Why is it Important? - Adoption of Office 365 is growing exponentially. Customers need to mitigate the risk of losing access to email and ensure availability for Office 365 users. In this blog we discuss… Continue Reading
Microsoft Office 365 Backup – Why is it Important? - Adoption of Office 365 is growing exponentially. Customers need to mitigate the risk of losing access to email and ensure availability for Office 365 users. In this blog we discuss… Continue Reading Data Availability in the Digital Financial Services Enterprise - Financial services organizations face many challenges in order to comply with rapidly evolving regulatory requirements for data security and integrity. In addition, volumes of stored data continues to grow at… Continue Reading
Data Availability in the Digital Financial Services Enterprise - Financial services organizations face many challenges in order to comply with rapidly evolving regulatory requirements for data security and integrity. In addition, volumes of stored data continues to grow at… Continue ReadingBuild a Scalable & Future-proof Data center - StoneFly offers a number of enterprise-grade solutions that can be used to build a scalable and future proof data center. This article explores some of StoneFly’s enterprise-grade storage technology that… Continue Reading
 The Business Value of using StoneFly and Veeam Backup & Disaster Recovery Solution - Data is increasingly at the core of any business or organization, and is fueling new digital transformation initiatives. Data runs nearly every aspect of a company, from customer and employee… Continue Reading
The Business Value of using StoneFly and Veeam Backup & Disaster Recovery Solution - Data is increasingly at the core of any business or organization, and is fueling new digital transformation initiatives. Data runs nearly every aspect of a company, from customer and employee… Continue Reading How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading
How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading Network Attached Storage (NAS) for Unstructured Big Data - Unstructured big data is growing exponentially. Analyzing and managing this data enables IT driven businesses to add value to their core operations. With StoneFly’s Network Attached Storage appliances businesses can… Continue Reading
Network Attached Storage (NAS) for Unstructured Big Data - Unstructured big data is growing exponentially. Analyzing and managing this data enables IT driven businesses to add value to their core operations. With StoneFly’s Network Attached Storage appliances businesses can… Continue Reading Purpose-built Backup and DR appliance for Nutanix - Explore what risks businesses take by not deploying reliable backup and disaster recovery solutions for enterprise-level infrastructures like Nutanix. The article also sheds light on StoneFly’s purpose-built backup and DR… Continue Reading
Purpose-built Backup and DR appliance for Nutanix - Explore what risks businesses take by not deploying reliable backup and disaster recovery solutions for enterprise-level infrastructures like Nutanix. The article also sheds light on StoneFly’s purpose-built backup and DR… Continue Reading Veeam Backup & Replication Best Practices: # 4 – Data reduction techniques - Optimizing the cost or benefit of various backup techniques and storage technologies means we will need to understand business requirements associated with the use of backup data and retention requirements.… Continue Reading
Veeam Backup & Replication Best Practices: # 4 – Data reduction techniques - Optimizing the cost or benefit of various backup techniques and storage technologies means we will need to understand business requirements associated with the use of backup data and retention requirements.… Continue Reading Hurricane Florence – Protect Enterprise IT Infrastructures - Hurricane Florence and its triggered floods are major threats for IT driven businesses in South Carolina. IT administrators can deploy cloud disaster recovery solutions and ensure that their IT systems… Continue Reading
Hurricane Florence – Protect Enterprise IT Infrastructures - Hurricane Florence and its triggered floods are major threats for IT driven businesses in South Carolina. IT administrators can deploy cloud disaster recovery solutions and ensure that their IT systems… Continue Reading Veeam Backup & Replication Best Practices: #3 – Architecture overview - Veeam Backup & Replication has a scale out architecture, in which multiple components (both for data processing and control) work together in a coordinated fashion. This blog provides a brief… Continue Reading
Veeam Backup & Replication Best Practices: #3 – Architecture overview - Veeam Backup & Replication has a scale out architecture, in which multiple components (both for data processing and control) work together in a coordinated fashion. This blog provides a brief… Continue Reading Veeam Backup & Replication Best Practices: #2 – Hypervisor, Backup Job and Restore - StoneFly and Veeam Offer state of the Art backup and disaster recovery solutions for Commercial, Public Sector and Cloud Service Providers. Veeam is the premier availability software for StoneFly, which… Continue Reading
Veeam Backup & Replication Best Practices: #2 – Hypervisor, Backup Job and Restore - StoneFly and Veeam Offer state of the Art backup and disaster recovery solutions for Commercial, Public Sector and Cloud Service Providers. Veeam is the premier availability software for StoneFly, which… Continue Reading Veeam Backup and Replication Best Practices: #1 – Backup Proxies - This article is the first in the series about the best practices about Veeam backup and replication. The article explores how enterprise IT environments can deploy and use backup proxies.… Continue Reading
Veeam Backup and Replication Best Practices: #1 – Backup Proxies - This article is the first in the series about the best practices about Veeam backup and replication. The article explores how enterprise IT environments can deploy and use backup proxies.… Continue Reading Deploy a Complete Business Model in the Cloud with the StoneFly SCVM™ - Data is essential for delivering value to your customers and outpacing your competitors. But as data growth accelerates and with 80% of new data being unstructured, finding a way to… Continue Reading
Deploy a Complete Business Model in the Cloud with the StoneFly SCVM™ - Data is essential for delivering value to your customers and outpacing your competitors. But as data growth accelerates and with 80% of new data being unstructured, finding a way to… Continue Reading Data Encryption Essential for Data Storage - A lot of data is transmitted these days, lots of private information is exchanged. In order to save the private data from any malicious attack encryption is used. This article… Continue Reading
Data Encryption Essential for Data Storage - A lot of data is transmitted these days, lots of private information is exchanged. In order to save the private data from any malicious attack encryption is used. This article… Continue Reading Affordable Enterprise Cloud Based Server - Cloud has changed the way people do business. Cloud has empowered many people to consume technology. You have to choose a cloud service provider that handles all for you. StoneFly… Continue Reading
Affordable Enterprise Cloud Based Server - Cloud has changed the way people do business. Cloud has empowered many people to consume technology. You have to choose a cloud service provider that handles all for you. StoneFly… Continue Reading How Media Organizations Can Protect Themselves from Ransomware Attacks - Cyber-crime is on the rise and it is affecting all types of industries worldwide. Media industry is also vulnerable to cyber-attacks. StoneFly™ helps the media and entertainment industry to secure… Continue Reading
How Media Organizations Can Protect Themselves from Ransomware Attacks - Cyber-crime is on the rise and it is affecting all types of industries worldwide. Media industry is also vulnerable to cyber-attacks. StoneFly™ helps the media and entertainment industry to secure… Continue Reading Protect your Law firm from Ransomware with DR365™ - Law firms and departments process, store and manage important and sensitive data. A successful ransomware attack results in confidentiality concerns, law suits and financial losses. For law organizations, ransomware is… Continue Reading
Protect your Law firm from Ransomware with DR365™ - Law firms and departments process, store and manage important and sensitive data. A successful ransomware attack results in confidentiality concerns, law suits and financial losses. For law organizations, ransomware is… Continue Reading Protecting Finance Industry from Ransomware Attacks - Ransomware is a major threat to FinTech Organizations and the Finance industry needs effective backup and disaster recovery solutions. However, there are a number of challenges associated with the industry.… Continue Reading
Protecting Finance Industry from Ransomware Attacks - Ransomware is a major threat to FinTech Organizations and the Finance industry needs effective backup and disaster recovery solutions. However, there are a number of challenges associated with the industry.… Continue Reading How Healthtech can be made Ransomware-proof with DR365™ - Healthcare industry deals with PII and mission-critical data that cannot tolerate downtime or disruption. Ransomware is a global threat that does not spare healthcare IT environments. Using StoneFly's feature-rich backup… Continue Reading
How Healthtech can be made Ransomware-proof with DR365™ - Healthcare industry deals with PII and mission-critical data that cannot tolerate downtime or disruption. Ransomware is a global threat that does not spare healthcare IT environments. Using StoneFly's feature-rich backup… Continue Reading Make IT environments Ransomware-proof with DR365™ - Ransomware is a continuously growing and forever lingering cyber-threat to enterprise IT environments worldwide. A successful attack can lead to millions of dollars in losses, discontinuity, data loss and brand… Continue Reading
Make IT environments Ransomware-proof with DR365™ - Ransomware is a continuously growing and forever lingering cyber-threat to enterprise IT environments worldwide. A successful attack can lead to millions of dollars in losses, discontinuity, data loss and brand… Continue Reading Eradicating storage and disaster recovery challenges with StoneFly SCVM - There is an increase in data day by day. With this increase in data, the traditional ways of data storage have failed to answer the data storage requirements of the… Continue Reading
Eradicating storage and disaster recovery challenges with StoneFly SCVM - There is an increase in data day by day. With this increase in data, the traditional ways of data storage have failed to answer the data storage requirements of the… Continue Reading Integrating Automated Tiering to Empower Enterprise IT environments - Automated tiering enables IT environments to effectively leverage storage resources and reduce the overall cost of data storage. StoneFly SCVM™ offers automated data tiering and a range of enterprise-scale services… Continue Reading
Integrating Automated Tiering to Empower Enterprise IT environments - Automated tiering enables IT environments to effectively leverage storage resources and reduce the overall cost of data storage. StoneFly SCVM™ offers automated data tiering and a range of enterprise-scale services… Continue Reading Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading
Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading Why is SCVM™ perfect for Microsoft and VMware hypervisors - StoneFly’s SCVM™ delivers an enterprise-level, highly available and feature-rich storage solution that also provides native data protection. It’s a single solution that addresses storage requirements and backup and disaster recovery… Continue Reading
Why is SCVM™ perfect for Microsoft and VMware hypervisors - StoneFly’s SCVM™ delivers an enterprise-level, highly available and feature-rich storage solution that also provides native data protection. It’s a single solution that addresses storage requirements and backup and disaster recovery… Continue Reading Backup Nutanix Infrastructures in Microsoft Azure with StoneFly and Veeam - This article explores what kind of enterprises can integrate cloud backup and disaster recovery to ensure business continuity and recovery for their enterprise workloads. Also explore the cloud backup and… Continue Reading
Backup Nutanix Infrastructures in Microsoft Azure with StoneFly and Veeam - This article explores what kind of enterprises can integrate cloud backup and disaster recovery to ensure business continuity and recovery for their enterprise workloads. Also explore the cloud backup and… Continue Reading StoneFly Data Protection Solutions for Enterprise Workloads - Hyper-converged infrastructure efficiently delivers according to enterprise storage requirements. However, the infrastructure cannot ensure high availability and data recoverability for enterprise workloads. In this article explore the major causes of… Continue Reading
StoneFly Data Protection Solutions for Enterprise Workloads - Hyper-converged infrastructure efficiently delivers according to enterprise storage requirements. However, the infrastructure cannot ensure high availability and data recoverability for enterprise workloads. In this article explore the major causes of… Continue Reading Microsoft Azure Cloud Security for Enterprise Data and Applications - Microsoft Azure cloud supports businesses around the globe. The Azure cloud processes gigantic chunks of sensitive and confidential data on a daily basis. Data security and privacy is of paramount… Continue Reading
Microsoft Azure Cloud Security for Enterprise Data and Applications - Microsoft Azure cloud supports businesses around the globe. The Azure cloud processes gigantic chunks of sensitive and confidential data on a daily basis. Data security and privacy is of paramount… Continue Reading How to configure volume and copy volumes in SAN? - These series of articles are the step to step guide for the StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software. The articles will be discussing that, how you… Continue Reading
How to configure volume and copy volumes in SAN? - These series of articles are the step to step guide for the StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software. The articles will be discussing that, how you… Continue Reading How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading
How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading How to discover and add Storage resources in Storage Concentrator SCVM™ - This article will discuss the resources section in StoneFly Storage Concentrator, how to discover resources and how to add resources in StoneFly Storage Concentrator (SCVM). Continue Reading
How to discover and add Storage resources in Storage Concentrator SCVM™ - This article will discuss the resources section in StoneFly Storage Concentrator, how to discover resources and how to add resources in StoneFly Storage Concentrator (SCVM). Continue Reading Introduction to storage concentrator GUI - This article, is the second article which is meant to guide you, how to deploy different segments of GUI. The introductory article went through the process of launching the administrative… Continue Reading
Introduction to storage concentrator GUI - This article, is the second article which is meant to guide you, how to deploy different segments of GUI. The introductory article went through the process of launching the administrative… Continue Reading How to launch the administrative interface in your StoneFly Storage Concentrator - This article will guide you about StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software provides the interface through which a system administrator can configure and monitor different parts… Continue Reading
How to launch the administrative interface in your StoneFly Storage Concentrator - This article will guide you about StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software provides the interface through which a system administrator can configure and monitor different parts… Continue Reading How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading
How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading How to deploy software defined Virtual Machine (SCVM) on VMWare ESXi? - These articles will guide you that how can the users deploy software defined SCVM on VMware ESXi. This article is meant to guide you through the process of deploying. The… Continue Reading
How to deploy software defined Virtual Machine (SCVM) on VMWare ESXi? - These articles will guide you that how can the users deploy software defined SCVM on VMware ESXi. This article is meant to guide you through the process of deploying. The… Continue Reading Ensuring business continuity by Veeam recovery to Microsoft Azure - Business continuity is one of the major considerations of organizations. When it comes to business continuity data backup and data restoration goes hand to hand. This article discusses about how… Continue Reading
Ensuring business continuity by Veeam recovery to Microsoft Azure - Business continuity is one of the major considerations of organizations. When it comes to business continuity data backup and data restoration goes hand to hand. This article discusses about how… Continue Reading Resilience from ransomware with StoneFly SCVM - Today's cyber security threats are constantly evolving. Most companies have preventive security software to stop these types of attacks but no matter how secure we are vulnerable to cyber-crimes. Ransomware… Continue Reading
Resilience from ransomware with StoneFly SCVM - Today's cyber security threats are constantly evolving. Most companies have preventive security software to stop these types of attacks but no matter how secure we are vulnerable to cyber-crimes. Ransomware… Continue Reading Things to know before considering SAN - SAN appliances can store files and can work as storage for specific applications like databases and Virtual machine file systems. In SAN data transportation is much efficient and reliable. Each… Continue Reading
Things to know before considering SAN - SAN appliances can store files and can work as storage for specific applications like databases and Virtual machine file systems. In SAN data transportation is much efficient and reliable. Each… Continue Reading Multi-cloud solutions for your data storage needs - With multi-cloud data storage solutions you can acquire not one but more than one cloud hosting environments. Multi-cloud in simple terms means the utilization of more than one cloud. This… Continue Reading
Multi-cloud solutions for your data storage needs - With multi-cloud data storage solutions you can acquire not one but more than one cloud hosting environments. Multi-cloud in simple terms means the utilization of more than one cloud. This… Continue Reading How StoneFly delivers Data Transportability - Data Transportability is the migration of data between applications or cloud services; however, StoneFly adds more to the concept of data transportability. With StoneFly’s application of data transportability, it delivers… Continue Reading
How StoneFly delivers Data Transportability - Data Transportability is the migration of data between applications or cloud services; however, StoneFly adds more to the concept of data transportability. With StoneFly’s application of data transportability, it delivers… Continue Reading Understanding Erasure Coding - Erasure Coding is the data protection method through which data is broken into sectors. Then data is encoded with redundant data pieces and stored across different storage media. This article… Continue Reading
Understanding Erasure Coding - Erasure Coding is the data protection method through which data is broken into sectors. Then data is encoded with redundant data pieces and stored across different storage media. This article… Continue Reading Implementation of Data redundancy in data storage - Data redundancy means: two copies of data in a single database or two different spots in multiple software environments or platforms. This article explains what data redundancy is, what level… Continue Reading
Implementation of Data redundancy in data storage - Data redundancy means: two copies of data in a single database or two different spots in multiple software environments or platforms. This article explains what data redundancy is, what level… Continue Reading Storage Snapshot technology: techniques and details - When selecting a snapshot technology from a vendor one must carefully consider the requirements and the environment of the enterprise, which is about to deploy the technology. The main aim… Continue Reading
Storage Snapshot technology: techniques and details - When selecting a snapshot technology from a vendor one must carefully consider the requirements and the environment of the enterprise, which is about to deploy the technology. The main aim… Continue Reading Understanding Scalability in Data Storage - The demands of storage are increasing, scalability is the feature which will address the data growth and enable businesses to effectively leverage their data. This article explores the concept, working… Continue Reading
Understanding Scalability in Data Storage - The demands of storage are increasing, scalability is the feature which will address the data growth and enable businesses to effectively leverage their data. This article explores the concept, working… Continue Reading Data Replication Technology: What it is & how does it work? - Data Replication delivers data redundancy for the enterprise; it also empowers disaster recovery technology to ensure reduced downtime. This article explores data replication technology: what it is, how it works… Continue Reading
Data Replication Technology: What it is & how does it work? - Data Replication delivers data redundancy for the enterprise; it also empowers disaster recovery technology to ensure reduced downtime. This article explores data replication technology: what it is, how it works… Continue Reading What is Scalability in the Cloud? - Data growth demands storage, backup and disaster recovery at scale. Cloud technology effectively addresses the demands imposed by continuously growing data. Scalability in the cloud facilitates data growth and enables… Continue Reading
What is Scalability in the Cloud? - Data growth demands storage, backup and disaster recovery at scale. Cloud technology effectively addresses the demands imposed by continuously growing data. Scalability in the cloud facilitates data growth and enables… Continue Reading Understanding Thin Provisioning and How it works - Thin provisioning optimizes storage utilization rates and enables enterprises to effectively leverage their storage resources. This article explains what Thin Provisioning is, how it works and how it’s different from… Continue Reading
Understanding Thin Provisioning and How it works - Thin provisioning optimizes storage utilization rates and enables enterprises to effectively leverage their storage resources. This article explains what Thin Provisioning is, how it works and how it’s different from… Continue Reading Exploring Data Deduplication for the Enterprise - Data deduplication is essential for effective storage space utilization. Enterprises can reduce their storage and backup costs by integrating deduplication in their solutions. This article explores what is deduplication and… Continue Reading
Exploring Data Deduplication for the Enterprise - Data deduplication is essential for effective storage space utilization. Enterprises can reduce their storage and backup costs by integrating deduplication in their solutions. This article explores what is deduplication and… Continue Reading Network Attached Storage (NAS) Appliance: Practicality and Usage - NAS storage appliances can effectively address the storage requirements of businesses while reducing latency and facilitating remote accessibility to data. This makes NAS storage appliances the prime choice for unstructured… Continue Reading
Network Attached Storage (NAS) Appliance: Practicality and Usage - NAS storage appliances can effectively address the storage requirements of businesses while reducing latency and facilitating remote accessibility to data. This makes NAS storage appliances the prime choice for unstructured… Continue Reading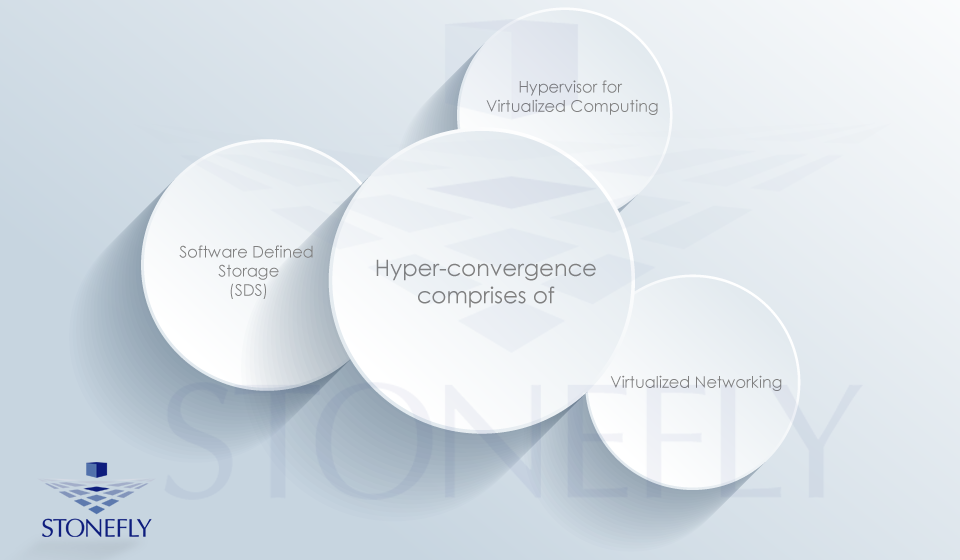 What is Hyperconverged Infrastructure (HCI)? - Hyperconvergence is required to provide easy scaling and management. It is a single system that reduces data center complexity and increases scalability. Multiple nodes of the appliance can be clustered… Continue Reading
What is Hyperconverged Infrastructure (HCI)? - Hyperconvergence is required to provide easy scaling and management. It is a single system that reduces data center complexity and increases scalability. Multiple nodes of the appliance can be clustered… Continue Reading Breaking down High Availability Configuration: Purpose and Necessity - High availability node comprises of full active active cluster with two active active head controllers plus dual active-active RAID controllers and two management engines. Data is failed over in few… Continue Reading
Breaking down High Availability Configuration: Purpose and Necessity - High availability node comprises of full active active cluster with two active active head controllers plus dual active-active RAID controllers and two management engines. Data is failed over in few… Continue Reading- SAN: Construction, Usage and its role in Business Continuity Management - For business continuity management you require SAN. SAN is a high speed network which provides shared pool of storage devices to several servers. Business continuity management is a framework that… Continue Reading
 How to add a Failover plan in StoneFly Cloud Connect - Keeping backup of your data is the essential step which you should take for your company. Through backup you can save the copies of your data and by disaster recovery… Continue Reading
How to add a Failover plan in StoneFly Cloud Connect - Keeping backup of your data is the essential step which you should take for your company. Through backup you can save the copies of your data and by disaster recovery… Continue Reading StoneFly CDR365: Innovative and Cost Effective Backup Solution for SMEs - Data protection is essential for the businesses of all sizes. If you assume that only large enterprises require it or you think that backup solutions are expensive, then you are… Continue Reading
StoneFly CDR365: Innovative and Cost Effective Backup Solution for SMEs - Data protection is essential for the businesses of all sizes. If you assume that only large enterprises require it or you think that backup solutions are expensive, then you are… Continue Reading StoneFly StoneWAN: Innovative Bandwidth Accelerator for the Multi-Branch Enterprise - Increasing the bandwidth does not deliver throughput; instead it creates a Long Fat Network (LFN). For the multi-branch enterprise, high bandwidth and high latency networks are a headache. StoneFly’s StoneWAN… Continue Reading
StoneFly StoneWAN: Innovative Bandwidth Accelerator for the Multi-Branch Enterprise - Increasing the bandwidth does not deliver throughput; instead it creates a Long Fat Network (LFN). For the multi-branch enterprise, high bandwidth and high latency networks are a headache. StoneFly’s StoneWAN… Continue Reading Closer look: StoneFly’s Innovative Storage Concentrator Virtual Machine (SCVM) - Software-defined storage (SDS), as purists argue, is any storage product that requires software to manage underlying hardware and control. The marketing term, software-defined storage is however, commonly associated with software… Continue Reading
Closer look: StoneFly’s Innovative Storage Concentrator Virtual Machine (SCVM) - Software-defined storage (SDS), as purists argue, is any storage product that requires software to manage underlying hardware and control. The marketing term, software-defined storage is however, commonly associated with software… Continue Reading How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading
How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading Enabling Automation for HIPAA/HITRUST Compliance in Microsoft Azure Cloud - Microsoft introduces automation for HIPAA/HITRUST compliance; facilitating enterprises to deploy industry compliant systems. The new release also includes a blueprint with a test sample, an FAQ and a video to… Continue Reading
Enabling Automation for HIPAA/HITRUST Compliance in Microsoft Azure Cloud - Microsoft introduces automation for HIPAA/HITRUST compliance; facilitating enterprises to deploy industry compliant systems. The new release also includes a blueprint with a test sample, an FAQ and a video to… Continue Reading Erasure Coding: Innovative Method of Robust Data Protection and Disaster Recovery - Old school backup tools are failing to prevent major outages and data loss as they place high demands on the data administrators which in turn are not able to cope… Continue Reading
Erasure Coding: Innovative Method of Robust Data Protection and Disaster Recovery - Old school backup tools are failing to prevent major outages and data loss as they place high demands on the data administrators which in turn are not able to cope… Continue Reading Enterprise Data Protection: Cloud Sync versus Cloud Backup - Although cloud sync and cloud backup feel as though they serve the same purpose, they’re not the same processes. This article explores the differences between the two and why both… Continue Reading
Enterprise Data Protection: Cloud Sync versus Cloud Backup - Although cloud sync and cloud backup feel as though they serve the same purpose, they’re not the same processes. This article explores the differences between the two and why both… Continue Reading- Innovative and Technologically Sound Considerations for Disaster Recovery and Cloud Backup - Disaster Recovery plan is a crucial step of any business continuity strategy and it often needs to be updated. In modern days, data backup has moved from traditional tapes to… Continue Reading
 Zero Trust: Enterprise Security for Ransomware Protection - Dive into our blog to discover how StoneFly's backup and disaster recovery appliances incorporate key features like air-gapped storage, immutability, and multi-factor authentication to fortify Zero Trust architecture and safeguard… Continue Reading
Zero Trust: Enterprise Security for Ransomware Protection - Dive into our blog to discover how StoneFly's backup and disaster recovery appliances incorporate key features like air-gapped storage, immutability, and multi-factor authentication to fortify Zero Trust architecture and safeguard… Continue Reading Malvertising: The Dark Side of Online Advertising - In our comprehensive guide, explore the shadowy world of malvertising—a pervasive threat to enterprises. From its evolution to detection strategies, delve into tactics and notable case studies to bolster your… Continue Reading
Malvertising: The Dark Side of Online Advertising - In our comprehensive guide, explore the shadowy world of malvertising—a pervasive threat to enterprises. From its evolution to detection strategies, delve into tactics and notable case studies to bolster your… Continue Reading Conti Ransomware: In-Depth Technical Breakdown - Explore the intricate workings of Conti ransomware, from its origins to notable attacks. Uncover mitigation strategies to fortify your defenses against this pervasive cyber threat. Continue Reading
Conti Ransomware: In-Depth Technical Breakdown - Explore the intricate workings of Conti ransomware, from its origins to notable attacks. Uncover mitigation strategies to fortify your defenses against this pervasive cyber threat. Continue Reading Supply Chain Attack: The Achilles’ Heel of Enterprise Security - Delve into the technical nuances of supply chain ransomware attacks and learn actionable strategies to improve your data security. Protect your critical data and mitigate risks effectively. Continue Reading
Supply Chain Attack: The Achilles’ Heel of Enterprise Security - Delve into the technical nuances of supply chain ransomware attacks and learn actionable strategies to improve your data security. Protect your critical data and mitigate risks effectively. Continue Reading Watering Hole Attacks Unveiled: A Comprehensive Cyberthreat Overview - Dive into the intricate realm of watering hole cyberattacks and fortify your enterprise defenses. Uncover nuanced tactics, countermeasures, and emerging trends to stay one step ahead of cyberthreats. Continue Reading
Watering Hole Attacks Unveiled: A Comprehensive Cyberthreat Overview - Dive into the intricate realm of watering hole cyberattacks and fortify your enterprise defenses. Uncover nuanced tactics, countermeasures, and emerging trends to stay one step ahead of cyberthreats. Continue Reading Man-in-the-Middle Attack: Cyberthreat Amidst Data Streams - Discover proactive strategies against Man-in-the-Middle attacks. Stay ahead of evolving cyber threats with insights on prevention and emerging trends. Continue Reading
Man-in-the-Middle Attack: Cyberthreat Amidst Data Streams - Discover proactive strategies against Man-in-the-Middle attacks. Stay ahead of evolving cyber threats with insights on prevention and emerging trends. Continue Reading Innovate, Test, Patch, and Update: The Role of On-Demand Sandbox - Embark on a transformative journey in data management as we delve into the revolutionary realm of On-Demand Sandboxes. Explore seamless integration, purpose-built solutions, and cloud flexibility, unlocking the true potential… Continue Reading
Innovate, Test, Patch, and Update: The Role of On-Demand Sandbox - Embark on a transformative journey in data management as we delve into the revolutionary realm of On-Demand Sandboxes. Explore seamless integration, purpose-built solutions, and cloud flexibility, unlocking the true potential… Continue Reading How is Ransomware Delivered: 7 Common Delivery Methods - Explore the intricate world of cyber threats as we unveil the 7 ways how ransomware is delivered. From strategic tactics to stealthy approaches, fortify your defenses against evolving dangers. Continue Reading
How is Ransomware Delivered: 7 Common Delivery Methods - Explore the intricate world of cyber threats as we unveil the 7 ways how ransomware is delivered. From strategic tactics to stealthy approaches, fortify your defenses against evolving dangers. Continue Reading Cactus Ransomware: Decrypting the Tactics of the Latest Cyberthreat - Explore the intricate workings of Cactus Ransomware, a potent cyber threat targeting large entities since March 2023. Uncover its tactics, mitigation strategies, and a call to fortify cybersecurity measures in… Continue Reading
Cactus Ransomware: Decrypting the Tactics of the Latest Cyberthreat - Explore the intricate workings of Cactus Ransomware, a potent cyber threat targeting large entities since March 2023. Uncover its tactics, mitigation strategies, and a call to fortify cybersecurity measures in… Continue Reading BlackCat/ALPHV Ransomware: In-Depth Analysis and Mitigation - Explore the ins and outs of BlackCat/ALPHV ransomware – from its evolving tactics to proactive defense strategies. Arm yourself with insights to safeguard your digital landscape against this ever-adapting cyber… Continue Reading
BlackCat/ALPHV Ransomware: In-Depth Analysis and Mitigation - Explore the ins and outs of BlackCat/ALPHV ransomware – from its evolving tactics to proactive defense strategies. Arm yourself with insights to safeguard your digital landscape against this ever-adapting cyber… Continue Reading 5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing… Continue Reading
5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing… Continue Reading The Spear Phishing Survival Guide - Dive into the realm of spear phishing – understanding its tactics, preparing against it, and mitigating risks. Arm yourself with actionable insights for robust cybersecurity. Continue Reading
The Spear Phishing Survival Guide - Dive into the realm of spear phishing – understanding its tactics, preparing against it, and mitigating risks. Arm yourself with actionable insights for robust cybersecurity. Continue Reading Understanding Detection and Response: EDR vs MDR vs XDR vs NDR - iscover the pillars of modern cybersecurity — EDR, MDR, XDR, and NDR. Uncover the distinctions, working mechanisms, and benefits of each to fortify your organization's digital defenses. Continue Reading
Understanding Detection and Response: EDR vs MDR vs XDR vs NDR - iscover the pillars of modern cybersecurity — EDR, MDR, XDR, and NDR. Uncover the distinctions, working mechanisms, and benefits of each to fortify your organization's digital defenses. Continue Reading Trigona Ransomware: What is it and How to Defend Against it - Explore the shadowy world of Trigona ransomware, a formidable cyberthreat. Delve into its origins, infection methods, and impacts. Discover how to prepare for and defend against this digital menace. Continue Reading
Trigona Ransomware: What is it and How to Defend Against it - Explore the shadowy world of Trigona ransomware, a formidable cyberthreat. Delve into its origins, infection methods, and impacts. Discover how to prepare for and defend against this digital menace. Continue Reading Lockbit Ransomware: Inside the Cyberthreat and Defense Strategies - Discover the inner workings of LockBit ransomware, its origins, and its continuous evolution in the relentless world of cybercrime. Learn how to safeguard your organization against this potent threat. Continue Reading
Lockbit Ransomware: Inside the Cyberthreat and Defense Strategies - Discover the inner workings of LockBit ransomware, its origins, and its continuous evolution in the relentless world of cybercrime. Learn how to safeguard your organization against this potent threat. Continue Reading What Defending Against Ransomware-as-a-Service (RaaS) Entails - Ransomware-as-a-Service (RaaS) has emerged as a formidable adversary. This blog delves into what RaaS entails and offers insights on how to fortify your defenses against this evolving peril. Continue Reading
What Defending Against Ransomware-as-a-Service (RaaS) Entails - Ransomware-as-a-Service (RaaS) has emerged as a formidable adversary. This blog delves into what RaaS entails and offers insights on how to fortify your defenses against this evolving peril. Continue Reading What are Advanced Persistent Threats (APTs) and How to Stop Them - Explore the realm of Advanced Persistent Threat (APT) attacks, understand their strategies, detection methods, and fortify your defenses for unyielding data security. Continue Reading
What are Advanced Persistent Threats (APTs) and How to Stop Them - Explore the realm of Advanced Persistent Threat (APT) attacks, understand their strategies, detection methods, and fortify your defenses for unyielding data security. Continue Reading Remote Code Execution (RCE) Attack and Vulnerabilities: Complete Overview - Dive into the realm of Remote Code Execution (RCE) attacks and fortify your cybersecurity. Discover how air-gapped and immutable backups can be your shield against evolving cyber threats. Continue Reading
Remote Code Execution (RCE) Attack and Vulnerabilities: Complete Overview - Dive into the realm of Remote Code Execution (RCE) attacks and fortify your cybersecurity. Discover how air-gapped and immutable backups can be your shield against evolving cyber threats. Continue Reading DDoS Attacks Decoded: Defending Against Modern Cyber Onslaughts - Delve into the disruptive realm of DDoS attacks, understanding their operations and motives. Learn how air-gapping and immutability fortify defenses, ensuring a resilient cybersecurity posture against relentless online assaults. Continue Reading
DDoS Attacks Decoded: Defending Against Modern Cyber Onslaughts - Delve into the disruptive realm of DDoS attacks, understanding their operations and motives. Learn how air-gapping and immutability fortify defenses, ensuring a resilient cybersecurity posture against relentless online assaults. Continue Reading GDPR Compliance & Its Importance for an Organization - What is GDPR compliance? What does it mean to your organization? Why is it important to achieve it? And how can StoneFly and Veeam help with GDPR compliance? Continue Reading
GDPR Compliance & Its Importance for an Organization - What is GDPR compliance? What does it mean to your organization? Why is it important to achieve it? And how can StoneFly and Veeam help with GDPR compliance? Continue Reading StoneFly 2019 Review: New Products, Features & More - 2019 was a busy year for us. We introduced additional compliance and security features to our hardware and software solutions. We also introduced solutions for MSPs along with data migration… Continue Reading
StoneFly 2019 Review: New Products, Features & More - 2019 was a busy year for us. We introduced additional compliance and security features to our hardware and software solutions. We also introduced solutions for MSPs along with data migration… Continue Reading Data Center Hardware Overview: Disaggregated HA Appliances - This blog is the fourth in the series of blogs that explain StoneFly’s innovative data storage appliance hardware architecture. In this blog, explore the appliance architecture and key components of… Continue Reading
Data Center Hardware Overview: Disaggregated HA Appliances - This blog is the fourth in the series of blogs that explain StoneFly’s innovative data storage appliance hardware architecture. In this blog, explore the appliance architecture and key components of… Continue Reading StoneFly & a Free Cup of Coffee Waiting for You at VMworld 2019 US - We're at VMworld 2019 and we're waiting to talk to you about your enterprise projects, problems, and challenges. We've got the solutions, the expertise, and a hot cup of coffee… Continue Reading
StoneFly & a Free Cup of Coffee Waiting for You at VMworld 2019 US - We're at VMworld 2019 and we're waiting to talk to you about your enterprise projects, problems, and challenges. We've got the solutions, the expertise, and a hot cup of coffee… Continue Reading What have we been doing in 2018 - In 2018, StoneFly introduced three products to our diverse range of enterprise products: CDR365, StoneWAN and the VSO™ appliance series. This article reviews 2018 and provides insight about these three… Continue Reading
What have we been doing in 2018 - In 2018, StoneFly introduced three products to our diverse range of enterprise products: CDR365, StoneWAN and the VSO™ appliance series. This article reviews 2018 and provides insight about these three… Continue Reading Tech or Treat: StoneFly’s Special Halloween offers - This Halloween, StoneFly is joining the fun and offering a number of treats for our Halloween enthusiastic IT administrators. In this article, explore the special Halloween offers that we have… Continue Reading
Tech or Treat: StoneFly’s Special Halloween offers - This Halloween, StoneFly is joining the fun and offering a number of treats for our Halloween enthusiastic IT administrators. In this article, explore the special Halloween offers that we have… Continue Reading Data Availability in the Digital Financial Services Enterprise - Financial services organizations face many challenges in order to comply with rapidly evolving regulatory requirements for data security and integrity. In addition, volumes of stored data continues to grow at… Continue Reading
Data Availability in the Digital Financial Services Enterprise - Financial services organizations face many challenges in order to comply with rapidly evolving regulatory requirements for data security and integrity. In addition, volumes of stored data continues to grow at… Continue Reading Data Encryption Essential for Data Storage - A lot of data is transmitted these days, lots of private information is exchanged. In order to save the private data from any malicious attack encryption is used. This article… Continue Reading
Data Encryption Essential for Data Storage - A lot of data is transmitted these days, lots of private information is exchanged. In order to save the private data from any malicious attack encryption is used. This article… Continue Reading Integrating Automated Tiering to Empower Enterprise IT environments - Automated tiering enables IT environments to effectively leverage storage resources and reduce the overall cost of data storage. StoneFly SCVM™ offers automated data tiering and a range of enterprise-scale services… Continue Reading
Integrating Automated Tiering to Empower Enterprise IT environments - Automated tiering enables IT environments to effectively leverage storage resources and reduce the overall cost of data storage. StoneFly SCVM™ offers automated data tiering and a range of enterprise-scale services… Continue Reading How StoneFly delivers Data Transportability - Data Transportability is the migration of data between applications or cloud services; however, StoneFly adds more to the concept of data transportability. With StoneFly’s application of data transportability, it delivers… Continue Reading
How StoneFly delivers Data Transportability - Data Transportability is the migration of data between applications or cloud services; however, StoneFly adds more to the concept of data transportability. With StoneFly’s application of data transportability, it delivers… Continue Reading Understanding Erasure Coding - Erasure Coding is the data protection method through which data is broken into sectors. Then data is encoded with redundant data pieces and stored across different storage media. This article… Continue Reading
Understanding Erasure Coding - Erasure Coding is the data protection method through which data is broken into sectors. Then data is encoded with redundant data pieces and stored across different storage media. This article… Continue Reading Implementation of Data redundancy in data storage - Data redundancy means: two copies of data in a single database or two different spots in multiple software environments or platforms. This article explains what data redundancy is, what level… Continue Reading
Implementation of Data redundancy in data storage - Data redundancy means: two copies of data in a single database or two different spots in multiple software environments or platforms. This article explains what data redundancy is, what level… Continue Reading Storage Snapshot technology: techniques and details - When selecting a snapshot technology from a vendor one must carefully consider the requirements and the environment of the enterprise, which is about to deploy the technology. The main aim… Continue Reading
Storage Snapshot technology: techniques and details - When selecting a snapshot technology from a vendor one must carefully consider the requirements and the environment of the enterprise, which is about to deploy the technology. The main aim… Continue Reading Understanding Scalability in Data Storage - The demands of storage are increasing, scalability is the feature which will address the data growth and enable businesses to effectively leverage their data. This article explores the concept, working… Continue Reading
Understanding Scalability in Data Storage - The demands of storage are increasing, scalability is the feature which will address the data growth and enable businesses to effectively leverage their data. This article explores the concept, working… Continue Reading Data Replication Technology: What it is & how does it work? - Data Replication delivers data redundancy for the enterprise; it also empowers disaster recovery technology to ensure reduced downtime. This article explores data replication technology: what it is, how it works… Continue Reading
Data Replication Technology: What it is & how does it work? - Data Replication delivers data redundancy for the enterprise; it also empowers disaster recovery technology to ensure reduced downtime. This article explores data replication technology: what it is, how it works… Continue Reading What is Scalability in the Cloud? - Data growth demands storage, backup and disaster recovery at scale. Cloud technology effectively addresses the demands imposed by continuously growing data. Scalability in the cloud facilitates data growth and enables… Continue Reading
What is Scalability in the Cloud? - Data growth demands storage, backup and disaster recovery at scale. Cloud technology effectively addresses the demands imposed by continuously growing data. Scalability in the cloud facilitates data growth and enables… Continue Reading Understanding Thin Provisioning and How it works - Thin provisioning optimizes storage utilization rates and enables enterprises to effectively leverage their storage resources. This article explains what Thin Provisioning is, how it works and how it’s different from… Continue Reading
Understanding Thin Provisioning and How it works - Thin provisioning optimizes storage utilization rates and enables enterprises to effectively leverage their storage resources. This article explains what Thin Provisioning is, how it works and how it’s different from… Continue Reading Exploring Data Deduplication for the Enterprise - Data deduplication is essential for effective storage space utilization. Enterprises can reduce their storage and backup costs by integrating deduplication in their solutions. This article explores what is deduplication and… Continue Reading
Exploring Data Deduplication for the Enterprise - Data deduplication is essential for effective storage space utilization. Enterprises can reduce their storage and backup costs by integrating deduplication in their solutions. This article explores what is deduplication and… Continue Reading Erasure Coding: Innovative Method of Robust Data Protection and Disaster Recovery - Old school backup tools are failing to prevent major outages and data loss as they place high demands on the data administrators which in turn are not able to cope… Continue Reading
Erasure Coding: Innovative Method of Robust Data Protection and Disaster Recovery - Old school backup tools are failing to prevent major outages and data loss as they place high demands on the data administrators which in turn are not able to cope… Continue Reading 5 Data Management Best Practices for Small to Mid-size Businesses (SMBs) - Small enterprises may assume that they do not need to invest in data management. However, this assumption can potentially make them fall behind competition and eventually limit their enterprise’s potential… Continue Reading
5 Data Management Best Practices for Small to Mid-size Businesses (SMBs) - Small enterprises may assume that they do not need to invest in data management. However, this assumption can potentially make them fall behind competition and eventually limit their enterprise’s potential… Continue Reading Why StoneFly Is the best Choice for your Enterprise? - Stonefly has a huge range of products and services providing enterprise level on-premises and cloud storage, backup and data recovery (DR) solutions. StoneFly’s innovative solutions facilitate access to cloud based… Continue Reading
Why StoneFly Is the best Choice for your Enterprise? - Stonefly has a huge range of products and services providing enterprise level on-premises and cloud storage, backup and data recovery (DR) solutions. StoneFly’s innovative solutions facilitate access to cloud based… Continue Reading When Big Data is a Big Headache: Addressing the Challenges to Reap Awards - The internet of things is made up of interconnected devices that generate Petabytes of data every day. From surfing the internet to make a purchase to actually making purchases, all… Continue Reading
When Big Data is a Big Headache: Addressing the Challenges to Reap Awards - The internet of things is made up of interconnected devices that generate Petabytes of data every day. From surfing the internet to make a purchase to actually making purchases, all… Continue Reading Virtualization Containers and how they compare to Virtual Machines - In the world of technology, IT pros need to customize technology solutions to meet their physical and virtual infrastructure needs. Various industries and firms are using systematically important workloads. Increased… Continue Reading
Virtualization Containers and how they compare to Virtual Machines - In the world of technology, IT pros need to customize technology solutions to meet their physical and virtual infrastructure needs. Various industries and firms are using systematically important workloads. Increased… Continue Reading Cloud Storage Solutions for Life Sciences Research - Life sciences are making the world a better place by invoking research every day which tackles the up and coming problems. The ability to analyze, explore and share tremendous volumes… Continue Reading
Cloud Storage Solutions for Life Sciences Research - Life sciences are making the world a better place by invoking research every day which tackles the up and coming problems. The ability to analyze, explore and share tremendous volumes… Continue Reading Cloud Cyber Security to Keep a Threat Free Corporate Environment - Increased data generation is resulting in greater problems in the corporate environment of an organization. Authorship attribution for crimes and cyber-attacks is becoming a major problem for all law enforcement… Continue Reading
Cloud Cyber Security to Keep a Threat Free Corporate Environment - Increased data generation is resulting in greater problems in the corporate environment of an organization. Authorship attribution for crimes and cyber-attacks is becoming a major problem for all law enforcement… Continue Reading Overcome Lock-in Limitations with StoneFly’s Multi-cloud Services - Vendor lock-in is a strategy used by major solution providers. If you want your backup and Disaster recovery plan to be comprehensive, you simply cannot make do with the list… Continue Reading
Overcome Lock-in Limitations with StoneFly’s Multi-cloud Services - Vendor lock-in is a strategy used by major solution providers. If you want your backup and Disaster recovery plan to be comprehensive, you simply cannot make do with the list… Continue Reading- How Blockchain Will Change the Financial Services Industry - Secure transactions and transmission of data is becoming a challenge in the continuously evolving IT world. Blockchain as a Service (BaaS) is a cloud computing platform that addresses the trust… Continue Reading
 Natural Disasters in Every Place! Get Data Protection at Rapid Pace - Natural disasters have become a frequent occurrence over the period of time. Large storms are becoming more and more frequent. Rising temperatures are causing a snowball effect which ultimately results… Continue Reading
Natural Disasters in Every Place! Get Data Protection at Rapid Pace - Natural disasters have become a frequent occurrence over the period of time. Large storms are becoming more and more frequent. Rising temperatures are causing a snowball effect which ultimately results… Continue Reading Tools of Protection from Ransomware - Greater data usage has increased the importance of data protection around the globe. Hackers have set their minds on valuable information which can impact the relations of the world in… Continue Reading
Tools of Protection from Ransomware - Greater data usage has increased the importance of data protection around the globe. Hackers have set their minds on valuable information which can impact the relations of the world in… Continue Reading Why Storage Companies Are Partnering with StoneFly for Cloud Storage - Cloud has been developed over the period of time to avoid putting the users in hassle. It is a kind of an Internet-Based-Service offered on demand to users. These users… Continue Reading
Why Storage Companies Are Partnering with StoneFly for Cloud Storage - Cloud has been developed over the period of time to avoid putting the users in hassle. It is a kind of an Internet-Based-Service offered on demand to users. These users… Continue Reading Big Data Storage Challenges and Solutions in Genomics - Big data refers to the vast volumes and types of information that companies can now collect and process using increasingly high-tech systems. Genomics research leads to a huge lakes of… Continue Reading
Big Data Storage Challenges and Solutions in Genomics - Big data refers to the vast volumes and types of information that companies can now collect and process using increasingly high-tech systems. Genomics research leads to a huge lakes of… Continue Reading Comparing Hadoop and SQL - If you have been familiar to working with conventional SQL-databases, hearing someone talk about Hadoop can sound like a crazy mess. In this blog, we are going to try and… Continue Reading
Comparing Hadoop and SQL - If you have been familiar to working with conventional SQL-databases, hearing someone talk about Hadoop can sound like a crazy mess. In this blog, we are going to try and… Continue Reading Petya – How to Protect Yourself from the Global Ransomware Outbreak - Another Ransomware attack, the Petya or Petrwarp, is spreading across the globe hitting a number of high-profile organizations, government agencies, public utilities and transportation networks in the United States and… Continue Reading
Petya – How to Protect Yourself from the Global Ransomware Outbreak - Another Ransomware attack, the Petya or Petrwarp, is spreading across the globe hitting a number of high-profile organizations, government agencies, public utilities and transportation networks in the United States and… Continue Reading After WannaCry. What Businesses Need to Withstand the Ransomware Era - WannaCry, one of many Ransomware variants, has been turned into a deadly virulence with data stolen from the NSA (National Security Agency), spread across 100 countries and counting, bringing down… Continue Reading
After WannaCry. What Businesses Need to Withstand the Ransomware Era - WannaCry, one of many Ransomware variants, has been turned into a deadly virulence with data stolen from the NSA (National Security Agency), spread across 100 countries and counting, bringing down… Continue Reading Why FedRAMP is Important? - The Federal Risk & Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized-approach to continuous monitoring, authorization and security assessment for cloud services and products. This allows… Continue Reading
Why FedRAMP is Important? - The Federal Risk & Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized-approach to continuous monitoring, authorization and security assessment for cloud services and products. This allows… Continue Reading Ransomware is dangerous; but StoneFly has your ‘Back’ - Ransomware has become a serious epidemic affecting businesses of all shapes and sizes. Protecting your business is a serious ‘business’ now, more than ever before. According to a U.S interagency… Continue Reading
Ransomware is dangerous; but StoneFly has your ‘Back’ - Ransomware has become a serious epidemic affecting businesses of all shapes and sizes. Protecting your business is a serious ‘business’ now, more than ever before. According to a U.S interagency… Continue Reading Why Analytics and Cloud Are Essential For the Success of IoT and 5G? - Today, Massive amounts of data are being generated from billions of smart-phones and cellular users. New 5G networks designed for Device-to-Device (D2D) communication and inexpensive sensors in the IoT (Internet… Continue Reading
Why Analytics and Cloud Are Essential For the Success of IoT and 5G? - Today, Massive amounts of data are being generated from billions of smart-phones and cellular users. New 5G networks designed for Device-to-Device (D2D) communication and inexpensive sensors in the IoT (Internet… Continue Reading StoneFly and Big Data Solutions for the Internet of Things - Internet connected devices that make the Internet of Things accumulate petabytes of data. There is more data to store from user smartphones such as images and videos or log file… Continue Reading
StoneFly and Big Data Solutions for the Internet of Things - Internet connected devices that make the Internet of Things accumulate petabytes of data. There is more data to store from user smartphones such as images and videos or log file… Continue Reading Accelerate Scientific Discovery with Microsoft Azure and Stonefly Storage - Today’s cutting-edge researchers move to the cloud leaving behind the limitations of physical data processing facilities and high costs. Cloud computing has changed the way research is done, bringing almost… Continue Reading
Accelerate Scientific Discovery with Microsoft Azure and Stonefly Storage - Today’s cutting-edge researchers move to the cloud leaving behind the limitations of physical data processing facilities and high costs. Cloud computing has changed the way research is done, bringing almost… Continue Reading What is Ransomware and How Can You Protect Yourself from It? - A new threat to your data is ransomware. Ransomware is at a sudden explosion making your data vulnerable to be hostage. Recent years have seen a rise in ransomware attacks.… Continue Reading
What is Ransomware and How Can You Protect Yourself from It? - A new threat to your data is ransomware. Ransomware is at a sudden explosion making your data vulnerable to be hostage. Recent years have seen a rise in ransomware attacks.… Continue Reading What is Recovery Time Objective and Recovery Point Objective? - Backing up your data is not enough alone. Backup and disaster recovery goes hand to hand to provide business continuity. Disaster recovery has the two main concepts. When designing disaster… Continue Reading
What is Recovery Time Objective and Recovery Point Objective? - Backing up your data is not enough alone. Backup and disaster recovery goes hand to hand to provide business continuity. Disaster recovery has the two main concepts. When designing disaster… Continue Reading Life Cycle of The Azure Stack Integrated System - Azure Stack in your data center is not just a software solution but it’s also a set of hardware that’s been tested, configured to align, essentially to the requirements of… Continue Reading
Life Cycle of The Azure Stack Integrated System - Azure Stack in your data center is not just a software solution but it’s also a set of hardware that’s been tested, configured to align, essentially to the requirements of… Continue Reading Internet Networking Problems - Today’s internet is suffering significant problems and growing pains and it’s worth bearing some of these in mind and thinking about them, as many of them give rise to interesting… Continue Reading
Internet Networking Problems - Today’s internet is suffering significant problems and growing pains and it’s worth bearing some of these in mind and thinking about them, as many of them give rise to interesting… Continue Reading Deep Dive in Virtualization - Creation of virtual operating system, server, and storage device or network resources instead of actual is known to be virtualization. You can manage workloads by radically transforming traditional computing to… Continue Reading
Deep Dive in Virtualization - Creation of virtual operating system, server, and storage device or network resources instead of actual is known to be virtualization. You can manage workloads by radically transforming traditional computing to… Continue Reading Five Stages of Security for Incident Response - Threats to your data are on the explosion. You need a strong security system to keep your data safe. Ask yourself how many of you can ensure that your data… Continue Reading
Five Stages of Security for Incident Response - Threats to your data are on the explosion. You need a strong security system to keep your data safe. Ask yourself how many of you can ensure that your data… Continue Reading Key Considerations When Looking for a Cloud Services Provider - In order to ensure the business continuity, you have to make the right choice about the cloud service provider. You need PERFECTION so that, you can ensure your business continuity.… Continue Reading
Key Considerations When Looking for a Cloud Services Provider - In order to ensure the business continuity, you have to make the right choice about the cloud service provider. You need PERFECTION so that, you can ensure your business continuity.… Continue Reading Basics of Microsoft Azure Cloud platform’s latest technology: Blockchain as a Service (BaaS) - Blockchain is a digitalized, decentralized, safe, shared, distributed ledger of all the cryptocurrency transactions. Blockchain is directly linked to the number of organizations or companies that participate in each of… Continue Reading
Basics of Microsoft Azure Cloud platform’s latest technology: Blockchain as a Service (BaaS) - Blockchain is a digitalized, decentralized, safe, shared, distributed ledger of all the cryptocurrency transactions. Blockchain is directly linked to the number of organizations or companies that participate in each of… Continue Reading What is Internet Small Computer System Interface (iSCSI) - iSCSI is the abbreviation for internet Small Computer System Interface. Sending block storage from the storage arrays to client computers through a storage area networking protocol is iSCSI. The storage… Continue Reading
What is Internet Small Computer System Interface (iSCSI) - iSCSI is the abbreviation for internet Small Computer System Interface. Sending block storage from the storage arrays to client computers through a storage area networking protocol is iSCSI. The storage… Continue Reading Things that you should look at when building a container ecosystem - Many enterprises have million budget and they want to build container environments. There are plenty of ecosystem tools which make the things easier for them. But there’s a lot of… Continue Reading
Things that you should look at when building a container ecosystem - Many enterprises have million budget and they want to build container environments. There are plenty of ecosystem tools which make the things easier for them. But there’s a lot of… Continue Reading Containers Made Easy - The world of containers is amazing. Today, Containers are very popular, and due to them being so popular, they have built a large ecosystem around them. They are used by… Continue Reading
Containers Made Easy - The world of containers is amazing. Today, Containers are very popular, and due to them being so popular, they have built a large ecosystem around them. They are used by… Continue Reading
 How to Integrate Azure/AWS Object Storage to On-Premises Appliance - Discover how to integrate Azure Blob, AWS, or other S3-compatible clouds with your on-premises appliance. Seamlessly manage and store data, leverage cloud benefits, and enhance your data management capabilities across… Continue Reading
How to Integrate Azure/AWS Object Storage to On-Premises Appliance - Discover how to integrate Azure Blob, AWS, or other S3-compatible clouds with your on-premises appliance. Seamlessly manage and store data, leverage cloud benefits, and enhance your data management capabilities across… Continue Reading Azure Backup vs AWS Backup: Which Cloud Backup Solution is More Secure - In this blog, we compare and contrast the security and backup features of two major cloud platforms, Azure and AWS. We delve into the key differences between Azure and AWS… Continue Reading
Azure Backup vs AWS Backup: Which Cloud Backup Solution is More Secure - In this blog, we compare and contrast the security and backup features of two major cloud platforms, Azure and AWS. We delve into the key differences between Azure and AWS… Continue Reading Exploring StoneFly Enterprise Cloud Storage in Azure - In order to facilitate businesses and make data storage easier, StoneFly offers Enterprise Cloud Storage in Azure. In this article we briefly explore what makes StoenFly Cloud Storage Solutions different… Continue Reading
Exploring StoneFly Enterprise Cloud Storage in Azure - In order to facilitate businesses and make data storage easier, StoneFly offers Enterprise Cloud Storage in Azure. In this article we briefly explore what makes StoenFly Cloud Storage Solutions different… Continue Reading Microsoft Azure Cloud Security for Enterprise Data and Applications - Microsoft Azure cloud supports businesses around the globe. The Azure cloud processes gigantic chunks of sensitive and confidential data on a daily basis. Data security and privacy is of paramount… Continue Reading
Microsoft Azure Cloud Security for Enterprise Data and Applications - Microsoft Azure cloud supports businesses around the globe. The Azure cloud processes gigantic chunks of sensitive and confidential data on a daily basis. Data security and privacy is of paramount… Continue Reading Ensuring business continuity by Veeam recovery to Microsoft Azure - Business continuity is one of the major considerations of organizations. When it comes to business continuity data backup and data restoration goes hand to hand. This article discusses about how… Continue Reading
Ensuring business continuity by Veeam recovery to Microsoft Azure - Business continuity is one of the major considerations of organizations. When it comes to business continuity data backup and data restoration goes hand to hand. This article discusses about how… Continue Reading Enabling Automation for HIPAA/HITRUST Compliance in Microsoft Azure Cloud - Microsoft introduces automation for HIPAA/HITRUST compliance; facilitating enterprises to deploy industry compliant systems. The new release also includes a blueprint with a test sample, an FAQ and a video to… Continue Reading
Enabling Automation for HIPAA/HITRUST Compliance in Microsoft Azure Cloud - Microsoft introduces automation for HIPAA/HITRUST compliance; facilitating enterprises to deploy industry compliant systems. The new release also includes a blueprint with a test sample, an FAQ and a video to… Continue Reading Integrating Veeam PN for Microsoft Azure with StoneFly’s Enterprise Level Services - StoneFly and Veeam cloud connect services make up an efficient and reliable backup and disaster recovery solution. Integrating Veeam PN into the mix establishes a simple enterprise network that secures… Continue Reading
Integrating Veeam PN for Microsoft Azure with StoneFly’s Enterprise Level Services - StoneFly and Veeam cloud connect services make up an efficient and reliable backup and disaster recovery solution. Integrating Veeam PN into the mix establishes a simple enterprise network that secures… Continue Reading How Microsoft Azure Can Empower Your Company’s Data & Infrastructure in The Cloud - The thing about Microsoft Azure is that it doesn’t force you to buy a plan or an entire package. Most services can be used independently of each other. For instance,… Continue Reading
How Microsoft Azure Can Empower Your Company’s Data & Infrastructure in The Cloud - The thing about Microsoft Azure is that it doesn’t force you to buy a plan or an entire package. Most services can be used independently of each other. For instance,… Continue Reading- CacheCloud Storage Gateway to Microsoft Azure and Amazon AWS Cloud Storage - Big cloud storage companies like Microsoft have been providing customers with well-balanced storage solutions from the time when such solutions seemed distant. Partnerships between the big companies provide enterprises with… Continue Reading
 Cloud Service Map: Facilitating Comparison between AWS & Azure Services - Amazon and Microsoft Azure provide amazing services and at times it becomes difficult to choose between their services. To address this challenge, Microsoft has come with a cloud service provider… Continue Reading
Cloud Service Map: Facilitating Comparison between AWS & Azure Services - Amazon and Microsoft Azure provide amazing services and at times it becomes difficult to choose between their services. To address this challenge, Microsoft has come with a cloud service provider… Continue Reading Azure Confidential Computing: Optimum Data Security from Ransomware. - Ransomware are the prime reasons for data loss. Ransomware attacks are disrupting the flow of operations and damaging the reputation of enterprises globally. A secure means of preventing the damage… Continue Reading
Azure Confidential Computing: Optimum Data Security from Ransomware. - Ransomware are the prime reasons for data loss. Ransomware attacks are disrupting the flow of operations and damaging the reputation of enterprises globally. A secure means of preventing the damage… Continue Reading Ease of Data Protection: Cloud Backup to Microsoft Azure Storage - StoneFly encompasses the needs of the customers to provide only the easiest and effective methods to set up cloud backup and storage. The customers are taken out of distress to… Continue Reading
Ease of Data Protection: Cloud Backup to Microsoft Azure Storage - StoneFly encompasses the needs of the customers to provide only the easiest and effective methods to set up cloud backup and storage. The customers are taken out of distress to… Continue Reading How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading
How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading How to setup Veeam Cloud Connect for the Enterprise Virtual Machine in Microsoft Azure Portal - We have created two parts to facilitate you with step by step explanation of how you can setup Veeam Cloud Connect for an enterprise virtual machine in Microsoft Azure. The… Continue Reading
How to setup Veeam Cloud Connect for the Enterprise Virtual Machine in Microsoft Azure Portal - We have created two parts to facilitate you with step by step explanation of how you can setup Veeam Cloud Connect for an enterprise virtual machine in Microsoft Azure. The… Continue Reading- PACS Storage: Addressing the Healthcare Industry File Growth Challenge - Taking care of loads of populations, providers of medical services offer extensive medical services throughout the world. The services of these facilities are increasing by the second as more and… Continue Reading
- How to add disk drives & scale out NAS storage in Microsoft azure VM? - Azure faciliatets you to scale out your NAS storages. You can add additional drives and you can scale out the virtual machine as well, which enables you to add more… Continue Reading
 How to setup StoneFly Scale out NAS VMs in Microsoft Azure portal? - This article is intended to guide you through the entire process of setting up StoneFly’s scale out network attached storage (NAS) virtual machines (VMs) in Microsoft Azure portal. Make sure… Continue Reading
How to setup StoneFly Scale out NAS VMs in Microsoft Azure portal? - This article is intended to guide you through the entire process of setting up StoneFly’s scale out network attached storage (NAS) virtual machines (VMs) in Microsoft Azure portal. Make sure… Continue Reading A Comparison between AWS S3 Infrequent Access and Azure Cool Blob Storage - Amazon web services (AWS) and Microsoft Azure have introduced their tier of object storage, particularly directed at protecting stored data. AWS S3 Infrequent Access (S3-IA) and Azure Cool Blob Storage… Continue Reading
A Comparison between AWS S3 Infrequent Access and Azure Cool Blob Storage - Amazon web services (AWS) and Microsoft Azure have introduced their tier of object storage, particularly directed at protecting stored data. AWS S3 Infrequent Access (S3-IA) and Azure Cool Blob Storage… Continue Reading Microsoft Azure and its Unique Functionality for A True Hybrid Platform - Amazon has dominated the cloud market for several years, so much so that it had become synonymous with the term “Private Cloud”. However the trend is changing now and organizations… Continue Reading
Microsoft Azure and its Unique Functionality for A True Hybrid Platform - Amazon has dominated the cloud market for several years, so much so that it had become synonymous with the term “Private Cloud”. However the trend is changing now and organizations… Continue Reading Why FedRAMP is Important? - The Federal Risk & Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized-approach to continuous monitoring, authorization and security assessment for cloud services and products. This allows… Continue Reading
Why FedRAMP is Important? - The Federal Risk & Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized-approach to continuous monitoring, authorization and security assessment for cloud services and products. This allows… Continue Reading Why choose Veeam Cloud Connect using StoneFly Cloud Storage in Microsoft Azure? - Veeam and Microsoft have partnered with StoneFly to offer state-of-the-art storage options leveraging StoneFly’s Scale-Out NAS Cloud Storage in Azure and StoneFly Cloud for the ultimate backup and disaster recovery… Continue Reading
Why choose Veeam Cloud Connect using StoneFly Cloud Storage in Microsoft Azure? - Veeam and Microsoft have partnered with StoneFly to offer state-of-the-art storage options leveraging StoneFly’s Scale-Out NAS Cloud Storage in Azure and StoneFly Cloud for the ultimate backup and disaster recovery… Continue Reading Accelerate Scientific Discovery with Microsoft Azure and Stonefly Storage - Today’s cutting-edge researchers move to the cloud leaving behind the limitations of physical data processing facilities and high costs. Cloud computing has changed the way research is done, bringing almost… Continue Reading
Accelerate Scientific Discovery with Microsoft Azure and Stonefly Storage - Today’s cutting-edge researchers move to the cloud leaving behind the limitations of physical data processing facilities and high costs. Cloud computing has changed the way research is done, bringing almost… Continue Reading Microsoft Azure cloud and StoneFly Cloud Storage - While moving to the cloud you have many things to consider about. We need to think about the operating system we’re going to use and how to keep that patched… Continue Reading
Microsoft Azure cloud and StoneFly Cloud Storage - While moving to the cloud you have many things to consider about. We need to think about the operating system we’re going to use and how to keep that patched… Continue Reading A Comprehensive Guide to Microsoft Azure Cloud Storage: Features and Benefits - Microsoft Azure Cloud Storage is Microsoft’s cloud storage solution which is for the modern data storage needs. Azure provides the massively scalable storage for data objects, file systems for the… Continue Reading
A Comprehensive Guide to Microsoft Azure Cloud Storage: Features and Benefits - Microsoft Azure Cloud Storage is Microsoft’s cloud storage solution which is for the modern data storage needs. Azure provides the massively scalable storage for data objects, file systems for the… Continue Reading Set of Attributes that are Associated with the Azure Stack Region - Azure Stack regions is a separation of physical hardware, and so you as a customer can take and essentially apply whatever other attributes are meaningful to you as that customer.… Continue Reading
Set of Attributes that are Associated with the Azure Stack Region - Azure Stack regions is a separation of physical hardware, and so you as a customer can take and essentially apply whatever other attributes are meaningful to you as that customer.… Continue Reading What is an Azure Stack instance or installation? - Azure Stack provides the on-demand, scalable computing resources which you can deploy before virtual machines. We have a single ARM instance that manages, or essentially is that portal for the… Continue Reading
What is an Azure Stack instance or installation? - Azure Stack provides the on-demand, scalable computing resources which you can deploy before virtual machines. We have a single ARM instance that manages, or essentially is that portal for the… Continue Reading Overview of the Azure Cloud Stack Architecture - Azure Stack is a hybrid cloud platform which lets you deliver Azure services in your data center. It comprises of new systems that enables you to have new scenarios for… Continue Reading
Overview of the Azure Cloud Stack Architecture - Azure Stack is a hybrid cloud platform which lets you deliver Azure services in your data center. It comprises of new systems that enables you to have new scenarios for… Continue Reading Life Cycle of The Azure Stack Integrated System - Azure Stack in your data center is not just a software solution but it’s also a set of hardware that’s been tested, configured to align, essentially to the requirements of… Continue Reading
Life Cycle of The Azure Stack Integrated System - Azure Stack in your data center is not just a software solution but it’s also a set of hardware that’s been tested, configured to align, essentially to the requirements of… Continue Reading Basics of Microsoft Azure Cloud platform’s latest technology: Blockchain as a Service (BaaS) - Blockchain is a digitalized, decentralized, safe, shared, distributed ledger of all the cryptocurrency transactions. Blockchain is directly linked to the number of organizations or companies that participate in each of… Continue Reading
Basics of Microsoft Azure Cloud platform’s latest technology: Blockchain as a Service (BaaS) - Blockchain is a digitalized, decentralized, safe, shared, distributed ledger of all the cryptocurrency transactions. Blockchain is directly linked to the number of organizations or companies that participate in each of… Continue Reading
 How to Integrate Azure/AWS Object Storage to On-Premises Appliance - Discover how to integrate Azure Blob, AWS, or other S3-compatible clouds with your on-premises appliance. Seamlessly manage and store data, leverage cloud benefits, and enhance your data management capabilities across… Continue Reading
How to Integrate Azure/AWS Object Storage to On-Premises Appliance - Discover how to integrate Azure Blob, AWS, or other S3-compatible clouds with your on-premises appliance. Seamlessly manage and store data, leverage cloud benefits, and enhance your data management capabilities across… Continue Reading Azure Backup vs AWS Backup: Which Cloud Backup Solution is More Secure - In this blog, we compare and contrast the security and backup features of two major cloud platforms, Azure and AWS. We delve into the key differences between Azure and AWS… Continue Reading
Azure Backup vs AWS Backup: Which Cloud Backup Solution is More Secure - In this blog, we compare and contrast the security and backup features of two major cloud platforms, Azure and AWS. We delve into the key differences between Azure and AWS… Continue Reading Safeguarding Your Data: Best Practices for Secure Cloud Storage - Are you concerned about the security of your data in the cloud? Do you struggle with planning and managing your storage capacity effectively? Are you looking for ways to maximize… Continue Reading
Safeguarding Your Data: Best Practices for Secure Cloud Storage - Are you concerned about the security of your data in the cloud? Do you struggle with planning and managing your storage capacity effectively? Are you looking for ways to maximize… Continue Reading Maximizing Data Protection with Cloud Backup and Recovery - Protecting your enterprise data is crucial, and having a comprehensive cloud backup and recovery solution is vital for your business continuity. StoneFly offers enterprise-grade cloud backup and recovery solutions in… Continue Reading
Maximizing Data Protection with Cloud Backup and Recovery - Protecting your enterprise data is crucial, and having a comprehensive cloud backup and recovery solution is vital for your business continuity. StoneFly offers enterprise-grade cloud backup and recovery solutions in… Continue Reading On-Premise vs Private Cloud: Choosing the Right Infrastructure for Your Business Needs - Learn how to choose the right cloud infrastructure for your business with this comprehensive guide from StoneFly. Explore the pros and cons of on-premise data centers and private clouds, the… Continue Reading
On-Premise vs Private Cloud: Choosing the Right Infrastructure for Your Business Needs - Learn how to choose the right cloud infrastructure for your business with this comprehensive guide from StoneFly. Explore the pros and cons of on-premise data centers and private clouds, the… Continue Reading NAS vs Cloud Storage – Which is Best for Your Hybrid Workforce - NAS vs cloud storage: what’s the difference between the two storage technologies and which one should you use for your hybrid workforce? Continue Reading
NAS vs Cloud Storage – Which is Best for Your Hybrid Workforce - NAS vs cloud storage: what’s the difference between the two storage technologies and which one should you use for your hybrid workforce? Continue Reading Meet Cyber Insurance Requirements with Immutable Backups - Cyber insurance protects your business from liability in the event of a cyber-attack. In order to satisfy cyber insurance requirements, you need to set up regular backups, air-gapping, and immutability… Continue Reading
Meet Cyber Insurance Requirements with Immutable Backups - Cyber insurance protects your business from liability in the event of a cyber-attack. In order to satisfy cyber insurance requirements, you need to set up regular backups, air-gapping, and immutability… Continue Reading On-Prem vs. Cloud Solutions: Which is Best for Your Business? - Learn the difference between on-premises vs. cloud infrastructure so that you can choose the right infrastructure for your business that supports your day-to-day operations within your budget. Continue Reading
On-Prem vs. Cloud Solutions: Which is Best for Your Business? - Learn the difference between on-premises vs. cloud infrastructure so that you can choose the right infrastructure for your business that supports your day-to-day operations within your budget. Continue Reading Keep Your Data Safe: S3 Object Lockdown for Compliance and Security - Learn more about S3 object lockdown, why should you use it, and how you can add it to your existing environment(s) to protect your critical object-level workloads from ransomware attacks. Continue Reading
Keep Your Data Safe: S3 Object Lockdown for Compliance and Security - Learn more about S3 object lockdown, why should you use it, and how you can add it to your existing environment(s) to protect your critical object-level workloads from ransomware attacks. Continue Reading Choosing the Right Data Backup Solution for Educational Sector - Educational institutes aren't safe from ransomware attacks. In this blog post, we explore the different data backup solutions that schools, colleges, and universities can implement to protect their administrative and… Continue Reading
Choosing the Right Data Backup Solution for Educational Sector - Educational institutes aren't safe from ransomware attacks. In this blog post, we explore the different data backup solutions that schools, colleges, and universities can implement to protect their administrative and… Continue Reading A Definitive Guide to Hybrid Cloud Computing - What is hybrid cloud? Why should you use it? How to implement a hybrid cloud architecture? Find the answers and more in this blog post. Continue Reading
A Definitive Guide to Hybrid Cloud Computing - What is hybrid cloud? Why should you use it? How to implement a hybrid cloud architecture? Find the answers and more in this blog post. Continue Reading Cloud Backup – A Comprehensive Overview - What is cloud backup, how can you backup your data to the cloud, and how can you use cloud backups to restore data and restore business operations. Find the answers… Continue Reading
Cloud Backup – A Comprehensive Overview - What is cloud backup, how can you backup your data to the cloud, and how can you use cloud backups to restore data and restore business operations. Find the answers… Continue Reading AWS Hybrid Cloud Storage for Media and Entertainment Industry - AWS hybrid cloud storage technology allows users to share data and work in collaboration from multiple locations. StoneFly cloud storage gateway enables you to build a data life cycle which… Continue Reading
AWS Hybrid Cloud Storage for Media and Entertainment Industry - AWS hybrid cloud storage technology allows users to share data and work in collaboration from multiple locations. StoneFly cloud storage gateway enables you to build a data life cycle which… Continue Reading Enhance Your AWS Cloud Storage Experience with StoneFly - Amazon cloud storage is the single place for whatever data your business needs to store, manage and analyze. And StoneFly cloud storage gateway gives you the tools to fully leverage… Continue Reading
Enhance Your AWS Cloud Storage Experience with StoneFly - Amazon cloud storage is the single place for whatever data your business needs to store, manage and analyze. And StoneFly cloud storage gateway gives you the tools to fully leverage… Continue Reading Medical Record Storage and PACS Archiving: Challenges & StoneFly’s Solutions - This article explores PACS, the challenges with medical record storage and PACS archiving, what kind of data archive solutions can healthcare organizations employ for medical record storage and PACS Archiving;… Continue Reading
Medical Record Storage and PACS Archiving: Challenges & StoneFly’s Solutions - This article explores PACS, the challenges with medical record storage and PACS archiving, what kind of data archive solutions can healthcare organizations employ for medical record storage and PACS Archiving;… Continue Reading Public versus Private: Which Cloud is Best for Enterprise Backups? - Enterprises have to make a decision when it comes to selecting which cloud is the best for their use-case either public or private. It tends to be a difficult decision.… Continue Reading
Public versus Private: Which Cloud is Best for Enterprise Backups? - Enterprises have to make a decision when it comes to selecting which cloud is the best for their use-case either public or private. It tends to be a difficult decision.… Continue Reading Best Use-Case of Enterprise Cloud Storage Technology - Enterprise cloud is used for storage, running enterprise workloads, archiving data, and backups; but what is the best use-case for it? This article answers that question and provides insight on… Continue Reading
Best Use-Case of Enterprise Cloud Storage Technology - Enterprise cloud is used for storage, running enterprise workloads, archiving data, and backups; but what is the best use-case for it? This article answers that question and provides insight on… Continue Reading Cloud Storage Adoption: Challenges & Solutions - Enterprise cloud storage integration can be challenging since they have to consider costs, bandwidth usage, integration complexities and other similar questions. StoneFly helps meet these challenges and deliver more value… Continue Reading
Cloud Storage Adoption: Challenges & Solutions - Enterprise cloud storage integration can be challenging since they have to consider costs, bandwidth usage, integration complexities and other similar questions. StoneFly helps meet these challenges and deliver more value… Continue Reading Exploring StoneFly Enterprise Cloud Storage in Azure - In order to facilitate businesses and make data storage easier, StoneFly offers Enterprise Cloud Storage in Azure. In this article we briefly explore what makes StoenFly Cloud Storage Solutions different… Continue Reading
Exploring StoneFly Enterprise Cloud Storage in Azure - In order to facilitate businesses and make data storage easier, StoneFly offers Enterprise Cloud Storage in Azure. In this article we briefly explore what makes StoenFly Cloud Storage Solutions different… Continue Reading Secure, Reliable & Simple Email Archiving for the Enterprise - Email archiving reduces cost and enables IT administrators to effectively protect email data. This article explores email archiving and why businesses should set it up. The article also explores how… Continue Reading
Secure, Reliable & Simple Email Archiving for the Enterprise - Email archiving reduces cost and enables IT administrators to effectively protect email data. This article explores email archiving and why businesses should set it up. The article also explores how… Continue Reading Demystifying Cloud Archiving & its Role in Business Environments - What are the challenges that businesses face without cloud archiving? What really is cloud archiving and what are its benefits? This article answers these questions and introduces the idea that… Continue Reading
Demystifying Cloud Archiving & its Role in Business Environments - What are the challenges that businesses face without cloud archiving? What really is cloud archiving and what are its benefits? This article answers these questions and introduces the idea that… Continue Reading Short Story: The Relation between Cloud Storage and Cloud Backup - The term “Cloud” has become mainstream but there’s still quite a bit of confusion on the application of the cloud. In this article, explore the difference between cloud storage and… Continue Reading
Short Story: The Relation between Cloud Storage and Cloud Backup - The term “Cloud” has become mainstream but there’s still quite a bit of confusion on the application of the cloud. In this article, explore the difference between cloud storage and… Continue Reading Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading
Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading Affordable Data Backup in Microsoft Azure and AWS Cloud - In our latest webinar “Affordable Data Backup in Microsoft Azure and AWS Cloud”, we discussed StoneFly CDR365™ - cloud backup and disaster recovery solution. In this blog post, we will… Continue Reading
Affordable Data Backup in Microsoft Azure and AWS Cloud - In our latest webinar “Affordable Data Backup in Microsoft Azure and AWS Cloud”, we discussed StoneFly CDR365™ - cloud backup and disaster recovery solution. In this blog post, we will… Continue Reading Backup your Data to Microsoft Azure and Amazon AWS with CDR365 - CDR365 is StoneFly’s backup solution that is built for the cloud. It allows you to backup your data to major public clouds like Microsoft Azure and Amazon AWS. You can… Continue Reading
Backup your Data to Microsoft Azure and Amazon AWS with CDR365 - CDR365 is StoneFly’s backup solution that is built for the cloud. It allows you to backup your data to major public clouds like Microsoft Azure and Amazon AWS. You can… Continue Reading Affordable Enterprise Cloud Based Server - Cloud has changed the way people do business. Cloud has empowered many people to consume technology. You have to choose a cloud service provider that handles all for you. StoneFly… Continue Reading
Affordable Enterprise Cloud Based Server - Cloud has changed the way people do business. Cloud has empowered many people to consume technology. You have to choose a cloud service provider that handles all for you. StoneFly… Continue Reading Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading
Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading Why is SCVM™ perfect for Microsoft and VMware hypervisors - StoneFly’s SCVM™ delivers an enterprise-level, highly available and feature-rich storage solution that also provides native data protection. It’s a single solution that addresses storage requirements and backup and disaster recovery… Continue Reading
Why is SCVM™ perfect for Microsoft and VMware hypervisors - StoneFly’s SCVM™ delivers an enterprise-level, highly available and feature-rich storage solution that also provides native data protection. It’s a single solution that addresses storage requirements and backup and disaster recovery… Continue Reading Microsoft Azure Cloud Security for Enterprise Data and Applications - Microsoft Azure cloud supports businesses around the globe. The Azure cloud processes gigantic chunks of sensitive and confidential data on a daily basis. Data security and privacy is of paramount… Continue Reading
Microsoft Azure Cloud Security for Enterprise Data and Applications - Microsoft Azure cloud supports businesses around the globe. The Azure cloud processes gigantic chunks of sensitive and confidential data on a daily basis. Data security and privacy is of paramount… Continue Reading Multi-cloud solutions for your data storage needs - With multi-cloud data storage solutions you can acquire not one but more than one cloud hosting environments. Multi-cloud in simple terms means the utilization of more than one cloud. This… Continue Reading
Multi-cloud solutions for your data storage needs - With multi-cloud data storage solutions you can acquire not one but more than one cloud hosting environments. Multi-cloud in simple terms means the utilization of more than one cloud. This… Continue Reading What is Scalability in the Cloud? - Data growth demands storage, backup and disaster recovery at scale. Cloud technology effectively addresses the demands imposed by continuously growing data. Scalability in the cloud facilitates data growth and enables… Continue Reading
What is Scalability in the Cloud? - Data growth demands storage, backup and disaster recovery at scale. Cloud technology effectively addresses the demands imposed by continuously growing data. Scalability in the cloud facilitates data growth and enables… Continue Reading How to add a Failover plan in StoneFly Cloud Connect - Keeping backup of your data is the essential step which you should take for your company. Through backup you can save the copies of your data and by disaster recovery… Continue Reading
How to add a Failover plan in StoneFly Cloud Connect - Keeping backup of your data is the essential step which you should take for your company. Through backup you can save the copies of your data and by disaster recovery… Continue Reading StoneFly StoneWAN: Innovative Bandwidth Accelerator for the Multi-Branch Enterprise - Increasing the bandwidth does not deliver throughput; instead it creates a Long Fat Network (LFN). For the multi-branch enterprise, high bandwidth and high latency networks are a headache. StoneFly’s StoneWAN… Continue Reading
StoneFly StoneWAN: Innovative Bandwidth Accelerator for the Multi-Branch Enterprise - Increasing the bandwidth does not deliver throughput; instead it creates a Long Fat Network (LFN). For the multi-branch enterprise, high bandwidth and high latency networks are a headache. StoneFly’s StoneWAN… Continue Reading How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading
How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading Enabling Automation for HIPAA/HITRUST Compliance in Microsoft Azure Cloud - Microsoft introduces automation for HIPAA/HITRUST compliance; facilitating enterprises to deploy industry compliant systems. The new release also includes a blueprint with a test sample, an FAQ and a video to… Continue Reading
Enabling Automation for HIPAA/HITRUST Compliance in Microsoft Azure Cloud - Microsoft introduces automation for HIPAA/HITRUST compliance; facilitating enterprises to deploy industry compliant systems. The new release also includes a blueprint with a test sample, an FAQ and a video to… Continue Reading Enterprise Data Protection: Cloud Sync versus Cloud Backup - Although cloud sync and cloud backup feel as though they serve the same purpose, they’re not the same processes. This article explores the differences between the two and why both… Continue Reading
Enterprise Data Protection: Cloud Sync versus Cloud Backup - Although cloud sync and cloud backup feel as though they serve the same purpose, they’re not the same processes. This article explores the differences between the two and why both… Continue Reading- Innovative and Technologically Sound Considerations for Disaster Recovery and Cloud Backup - Disaster Recovery plan is a crucial step of any business continuity strategy and it often needs to be updated. In modern days, data backup has moved from traditional tapes to… Continue Reading
- How the cloud fits in an enterprise data protection strategy? - Many of the companies using a data protection solution often find the cloud more secure for the data protection. The cloud presents itself as a native solution for data protection.… Continue Reading
 Combining the Cloud with Disaster Recovery and Business Continuity - Finding a way to store, distribute and manage all your data in today’s dynamic world is a big challenge. Running applications, delivering content to users, hosting high traffic websites or… Continue Reading
Combining the Cloud with Disaster Recovery and Business Continuity - Finding a way to store, distribute and manage all your data in today’s dynamic world is a big challenge. Running applications, delivering content to users, hosting high traffic websites or… Continue Reading Integrating Veeam PN for Microsoft Azure with StoneFly’s Enterprise Level Services - StoneFly and Veeam cloud connect services make up an efficient and reliable backup and disaster recovery solution. Integrating Veeam PN into the mix establishes a simple enterprise network that secures… Continue Reading
Integrating Veeam PN for Microsoft Azure with StoneFly’s Enterprise Level Services - StoneFly and Veeam cloud connect services make up an efficient and reliable backup and disaster recovery solution. Integrating Veeam PN into the mix establishes a simple enterprise network that secures… Continue Reading- The Role of Cloud Computing in the Internet of Things - The Internet of Things (IoT) is a dimension of connectivity in itself which makes the world better through innovations and inventions. The internet of things can be seen as an… Continue Reading
 IT Infrastructure Upgradation with Hybrid Cloud - The hybrid cloud facilitates high IOPS requirements, reduces latency and optimizes processes. This makes flexible enough to accommodate IT environments with diverse workloads with a range of requirements. Continue Reading
IT Infrastructure Upgradation with Hybrid Cloud - The hybrid cloud facilitates high IOPS requirements, reduces latency and optimizes processes. This makes flexible enough to accommodate IT environments with diverse workloads with a range of requirements. Continue Reading Archiving Veeam Backups in Amazon Glacier - The advantage of storing data in Amazon Glacier is its low cost. And although Amazon glacier is designed for cold data with scarce chance of being recovered, the real challenge… Continue Reading
Archiving Veeam Backups in Amazon Glacier - The advantage of storing data in Amazon Glacier is its low cost. And although Amazon glacier is designed for cold data with scarce chance of being recovered, the real challenge… Continue Reading Why utilize more than one solution for cloud backup? - Enterprise may rely heavily on a single cloud but if anything happens to that cloud, they’re basically doomed. This is one of the prime, but not the only, reasons to… Continue Reading
Why utilize more than one solution for cloud backup? - Enterprise may rely heavily on a single cloud but if anything happens to that cloud, they’re basically doomed. This is one of the prime, but not the only, reasons to… Continue Reading Difference between Managed backup and self-service backup - With the growing data being generated every day, a lot of considerations have to be kept in mind when deciding where to store the data. A speedy, reliable and secure… Continue Reading
Difference between Managed backup and self-service backup - With the growing data being generated every day, a lot of considerations have to be kept in mind when deciding where to store the data. A speedy, reliable and secure… Continue Reading Difference Between Disaster Recovery as a Service (DRaaS) and Cloud Backup - Cloud-based backup and recovery have become common these days. If a backup is fast enough and if recovery times hit recovery time and recovery point objectives (RTPOs) service levels you… Continue Reading
Difference Between Disaster Recovery as a Service (DRaaS) and Cloud Backup - Cloud-based backup and recovery have become common these days. If a backup is fast enough and if recovery times hit recovery time and recovery point objectives (RTPOs) service levels you… Continue Reading Cloud Storage Solutions for Life Sciences Research - Life sciences are making the world a better place by invoking research every day which tackles the up and coming problems. The ability to analyze, explore and share tremendous volumes… Continue Reading
Cloud Storage Solutions for Life Sciences Research - Life sciences are making the world a better place by invoking research every day which tackles the up and coming problems. The ability to analyze, explore and share tremendous volumes… Continue Reading How Microsoft Azure Can Empower Your Company’s Data & Infrastructure in The Cloud - The thing about Microsoft Azure is that it doesn’t force you to buy a plan or an entire package. Most services can be used independently of each other. For instance,… Continue Reading
How Microsoft Azure Can Empower Your Company’s Data & Infrastructure in The Cloud - The thing about Microsoft Azure is that it doesn’t force you to buy a plan or an entire package. Most services can be used independently of each other. For instance,… Continue Reading Enterprise Storage Optimization with The StoneFly CacheCloud Storage Appliance - Everyone is exploring cloud for its utilization and benefits. Enterprises can use cloud-based services for multiple purposes and increase their productivity, add value to their data all while protecting and… Continue Reading
Enterprise Storage Optimization with The StoneFly CacheCloud Storage Appliance - Everyone is exploring cloud for its utilization and benefits. Enterprises can use cloud-based services for multiple purposes and increase their productivity, add value to their data all while protecting and… Continue Reading- CacheCloud Storage Gateway to Microsoft Azure and Amazon AWS Cloud Storage - Big cloud storage companies like Microsoft have been providing customers with well-balanced storage solutions from the time when such solutions seemed distant. Partnerships between the big companies provide enterprises with… Continue Reading
 Difference between Backup and Archiving - In the past, protection and retention were handled by copying data to tape, but the improving economics of disk storage and emergence of backup solutions create new options. Both Backup… Continue Reading
Difference between Backup and Archiving - In the past, protection and retention were handled by copying data to tape, but the improving economics of disk storage and emergence of backup solutions create new options. Both Backup… Continue Reading Cloud Storage Security – Iron-Clad Data Defense - In this blog, we discuss what organizations can do to protect their data from cyber-security risks, what challenges they might face with cloud storage security, and how StoneFly can help. Continue Reading
Cloud Storage Security – Iron-Clad Data Defense - In this blog, we discuss what organizations can do to protect their data from cyber-security risks, what challenges they might face with cloud storage security, and how StoneFly can help. Continue Reading Overcome Lock-in Limitations with StoneFly’s Multi-cloud Services - Vendor lock-in is a strategy used by major solution providers. If you want your backup and Disaster recovery plan to be comprehensive, you simply cannot make do with the list… Continue Reading
Overcome Lock-in Limitations with StoneFly’s Multi-cloud Services - Vendor lock-in is a strategy used by major solution providers. If you want your backup and Disaster recovery plan to be comprehensive, you simply cannot make do with the list… Continue Reading Cloud Service Map: Facilitating Comparison between AWS & Azure Services - Amazon and Microsoft Azure provide amazing services and at times it becomes difficult to choose between their services. To address this challenge, Microsoft has come with a cloud service provider… Continue Reading
Cloud Service Map: Facilitating Comparison between AWS & Azure Services - Amazon and Microsoft Azure provide amazing services and at times it becomes difficult to choose between their services. To address this challenge, Microsoft has come with a cloud service provider… Continue Reading Why Move Your Company’s Storage to the Cloud? - The dominance of Amazon in the cloud market for several years has given it unmatchable importance. So much so, it had become synonymous with the term “Private Cloud”. StoneFly Cloud… Continue Reading
Why Move Your Company’s Storage to the Cloud? - The dominance of Amazon in the cloud market for several years has given it unmatchable importance. So much so, it had become synonymous with the term “Private Cloud”. StoneFly Cloud… Continue Reading Business Continuity and Disaster Recovery for Financial Services Providers - Financial services have many different entities. Each and every single entity shares the same common requirement which is availability of services. Providing this successfully is in the hands of IT… Continue Reading
Business Continuity and Disaster Recovery for Financial Services Providers - Financial services have many different entities. Each and every single entity shares the same common requirement which is availability of services. Providing this successfully is in the hands of IT… Continue Reading What You Need to Know About Migrating to a CJIS Compliant Cloud - CJIS is a policy that enables government agencies to evaluate their own Procedures, Networks and Cloud providers. For secure Cloud Storage, Amazon Web Services (AWS) signed the contract to run… Continue Reading
What You Need to Know About Migrating to a CJIS Compliant Cloud - CJIS is a policy that enables government agencies to evaluate their own Procedures, Networks and Cloud providers. For secure Cloud Storage, Amazon Web Services (AWS) signed the contract to run… Continue Reading Natural Disasters in Every Place! Get Data Protection at Rapid Pace - Natural disasters have become a frequent occurrence over the period of time. Large storms are becoming more and more frequent. Rising temperatures are causing a snowball effect which ultimately results… Continue Reading
Natural Disasters in Every Place! Get Data Protection at Rapid Pace - Natural disasters have become a frequent occurrence over the period of time. Large storms are becoming more and more frequent. Rising temperatures are causing a snowball effect which ultimately results… Continue Reading AWS Management Tools & Features for Efficient Cloud Backup and Recovery - Amazon’s innovative management tools and features are designed to ease the process of backup and disaster recovery while retaining their cost efficient nature. Amazon provides a number of tools that… Continue Reading
AWS Management Tools & Features for Efficient Cloud Backup and Recovery - Amazon’s innovative management tools and features are designed to ease the process of backup and disaster recovery while retaining their cost efficient nature. Amazon provides a number of tools that… Continue Reading Cloud Backup and replication for Hyper-V Environments - Backup and disaster recovery are essential for enterprises around the globe because these services ensure data availability and recoverability. However, data security and protection is even more significant and comparison.… Continue Reading
Cloud Backup and replication for Hyper-V Environments - Backup and disaster recovery are essential for enterprises around the globe because these services ensure data availability and recoverability. However, data security and protection is even more significant and comparison.… Continue Reading Azure Confidential Computing: Optimum Data Security from Ransomware. - Ransomware are the prime reasons for data loss. Ransomware attacks are disrupting the flow of operations and damaging the reputation of enterprises globally. A secure means of preventing the damage… Continue Reading
Azure Confidential Computing: Optimum Data Security from Ransomware. - Ransomware are the prime reasons for data loss. Ransomware attacks are disrupting the flow of operations and damaging the reputation of enterprises globally. A secure means of preventing the damage… Continue Reading Amazon Macie: Artificial Intelligence for Efficient Data Security - Recent studies indicated that over 60,000 sensitive files of the government had public access due to incorrect classification and access management control. This revelation prompted the realization that classification and… Continue Reading
Amazon Macie: Artificial Intelligence for Efficient Data Security - Recent studies indicated that over 60,000 sensitive files of the government had public access due to incorrect classification and access management control. This revelation prompted the realization that classification and… Continue Reading Optimal data archival with Glacier: Understanding Archival data and its challenges - There are a lot of benefits when backing up to Amazon Glacier. Amazon Glacier is an extremely low cost storage service that revolutionizes data archiving and backup. Glacier also allows… Continue Reading
Optimal data archival with Glacier: Understanding Archival data and its challenges - There are a lot of benefits when backing up to Amazon Glacier. Amazon Glacier is an extremely low cost storage service that revolutionizes data archiving and backup. Glacier also allows… Continue Reading Increased Natural Disasters: A Dire Need for Data Protection and Disaster Recovery - We live in a truly digital age where records and information of all kinds are no longer kept in labeled boxes and vaults or stuffy basements. Information has become ever… Continue Reading
Increased Natural Disasters: A Dire Need for Data Protection and Disaster Recovery - We live in a truly digital age where records and information of all kinds are no longer kept in labeled boxes and vaults or stuffy basements. Information has become ever… Continue Reading Addressing the Growing Storage Needs for Financial Services - Financial sector is the backbone of any economy. It is dominated by banks which play a vital role in ensuring the growth of the economy. They are always in need… Continue Reading
Addressing the Growing Storage Needs for Financial Services - Financial sector is the backbone of any economy. It is dominated by banks which play a vital role in ensuring the growth of the economy. They are always in need… Continue Reading How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading
How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading What you should know before moving Disaster Recovery to the cloud - Why are enterprises, small businesses and even domestic users employing disaster recovery appliances and services? Cloud disaster recovery (DR) ensures high availability of the data, continuous flow of the process… Continue Reading
What you should know before moving Disaster Recovery to the cloud - Why are enterprises, small businesses and even domestic users employing disaster recovery appliances and services? Cloud disaster recovery (DR) ensures high availability of the data, continuous flow of the process… Continue Reading- How to add disk drives & scale out NAS storage in Microsoft azure VM? - Azure faciliatets you to scale out your NAS storages. You can add additional drives and you can scale out the virtual machine as well, which enables you to add more… Continue Reading
 How to setup StoneFly Scale out NAS VMs in Microsoft Azure portal? - This article is intended to guide you through the entire process of setting up StoneFly’s scale out network attached storage (NAS) virtual machines (VMs) in Microsoft Azure portal. Make sure… Continue Reading
How to setup StoneFly Scale out NAS VMs in Microsoft Azure portal? - This article is intended to guide you through the entire process of setting up StoneFly’s scale out network attached storage (NAS) virtual machines (VMs) in Microsoft Azure portal. Make sure… Continue Reading Scale-Out NAS is The Way IoT and Big Data Storage Can Move Forward - Big data is helping shape the future of the world. Smart cities are appearing on the world map, with amazing innovations automating and regulating a number of things. In order… Continue Reading
Scale-Out NAS is The Way IoT and Big Data Storage Can Move Forward - Big data is helping shape the future of the world. Smart cities are appearing on the world map, with amazing innovations automating and regulating a number of things. In order… Continue Reading Affordable and efficient cloud-based disaster recovery - It wasn’t that long ago when most people were priced out of disaster recovery. Protecting your environment came down to two choices one double up on existing hardware and just… Continue Reading
Affordable and efficient cloud-based disaster recovery - It wasn’t that long ago when most people were priced out of disaster recovery. Protecting your environment came down to two choices one double up on existing hardware and just… Continue Reading Microsoft Azure and its Unique Functionality for A True Hybrid Platform - Amazon has dominated the cloud market for several years, so much so that it had become synonymous with the term “Private Cloud”. However the trend is changing now and organizations… Continue Reading
Microsoft Azure and its Unique Functionality for A True Hybrid Platform - Amazon has dominated the cloud market for several years, so much so that it had become synonymous with the term “Private Cloud”. However the trend is changing now and organizations… Continue Reading Cloud Data Protection for VMware Environments - An organization’s data protection and disaster recovery (DR) strategy often consists of many disparate recovery and backup “solutions,” which may or may not be compatible with each other. As a… Continue Reading
Cloud Data Protection for VMware Environments - An organization’s data protection and disaster recovery (DR) strategy often consists of many disparate recovery and backup “solutions,” which may or may not be compatible with each other. As a… Continue Reading Why FedRAMP is Important? - The Federal Risk & Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized-approach to continuous monitoring, authorization and security assessment for cloud services and products. This allows… Continue Reading
Why FedRAMP is Important? - The Federal Risk & Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized-approach to continuous monitoring, authorization and security assessment for cloud services and products. This allows… Continue Reading Why Analytics and Cloud Are Essential For the Success of IoT and 5G? - Today, Massive amounts of data are being generated from billions of smart-phones and cellular users. New 5G networks designed for Device-to-Device (D2D) communication and inexpensive sensors in the IoT (Internet… Continue Reading
Why Analytics and Cloud Are Essential For the Success of IoT and 5G? - Today, Massive amounts of data are being generated from billions of smart-phones and cellular users. New 5G networks designed for Device-to-Device (D2D) communication and inexpensive sensors in the IoT (Internet… Continue Reading Understanding The StoneFly Cloud Service Models - Cloud service models are essentially a set of IT-related services offered by a cloud Provider to provide IT resource to a consumer. Many cloud Service-Providers offer a wide spectrum of… Continue Reading
Understanding The StoneFly Cloud Service Models - Cloud service models are essentially a set of IT-related services offered by a cloud Provider to provide IT resource to a consumer. Many cloud Service-Providers offer a wide spectrum of… Continue Reading StoneFly and Big Data Solutions for the Internet of Things - Internet connected devices that make the Internet of Things accumulate petabytes of data. There is more data to store from user smartphones such as images and videos or log file… Continue Reading
StoneFly and Big Data Solutions for the Internet of Things - Internet connected devices that make the Internet of Things accumulate petabytes of data. There is more data to store from user smartphones such as images and videos or log file… Continue Reading Accelerate Scientific Discovery with Microsoft Azure and Stonefly Storage - Today’s cutting-edge researchers move to the cloud leaving behind the limitations of physical data processing facilities and high costs. Cloud computing has changed the way research is done, bringing almost… Continue Reading
Accelerate Scientific Discovery with Microsoft Azure and Stonefly Storage - Today’s cutting-edge researchers move to the cloud leaving behind the limitations of physical data processing facilities and high costs. Cloud computing has changed the way research is done, bringing almost… Continue Reading Microsoft Azure cloud and StoneFly Cloud Storage - While moving to the cloud you have many things to consider about. We need to think about the operating system we’re going to use and how to keep that patched… Continue Reading
Microsoft Azure cloud and StoneFly Cloud Storage - While moving to the cloud you have many things to consider about. We need to think about the operating system we’re going to use and how to keep that patched… Continue Reading A Comprehensive Guide to Microsoft Azure Cloud Storage: Features and Benefits - Microsoft Azure Cloud Storage is Microsoft’s cloud storage solution which is for the modern data storage needs. Azure provides the massively scalable storage for data objects, file systems for the… Continue Reading
A Comprehensive Guide to Microsoft Azure Cloud Storage: Features and Benefits - Microsoft Azure Cloud Storage is Microsoft’s cloud storage solution which is for the modern data storage needs. Azure provides the massively scalable storage for data objects, file systems for the… Continue Reading Set of Attributes that are Associated with the Azure Stack Region - Azure Stack regions is a separation of physical hardware, and so you as a customer can take and essentially apply whatever other attributes are meaningful to you as that customer.… Continue Reading
Set of Attributes that are Associated with the Azure Stack Region - Azure Stack regions is a separation of physical hardware, and so you as a customer can take and essentially apply whatever other attributes are meaningful to you as that customer.… Continue Reading What is an Azure Stack instance or installation? - Azure Stack provides the on-demand, scalable computing resources which you can deploy before virtual machines. We have a single ARM instance that manages, or essentially is that portal for the… Continue Reading
What is an Azure Stack instance or installation? - Azure Stack provides the on-demand, scalable computing resources which you can deploy before virtual machines. We have a single ARM instance that manages, or essentially is that portal for the… Continue Reading Overview of the Azure Cloud Stack Architecture - Azure Stack is a hybrid cloud platform which lets you deliver Azure services in your data center. It comprises of new systems that enables you to have new scenarios for… Continue Reading
Overview of the Azure Cloud Stack Architecture - Azure Stack is a hybrid cloud platform which lets you deliver Azure services in your data center. It comprises of new systems that enables you to have new scenarios for… Continue Reading Life Cycle of The Azure Stack Integrated System - Azure Stack in your data center is not just a software solution but it’s also a set of hardware that’s been tested, configured to align, essentially to the requirements of… Continue Reading
Life Cycle of The Azure Stack Integrated System - Azure Stack in your data center is not just a software solution but it’s also a set of hardware that’s been tested, configured to align, essentially to the requirements of… Continue Reading How and What to move to the cloud - Being an IT professional you are under pressure, you have to keep your company’s data up and running with simplicity. Every bite and bit of data, every key element depends… Continue Reading
How and What to move to the cloud - Being an IT professional you are under pressure, you have to keep your company’s data up and running with simplicity. Every bite and bit of data, every key element depends… Continue Reading Key Considerations When Looking for a Cloud Services Provider - In order to ensure the business continuity, you have to make the right choice about the cloud service provider. You need PERFECTION so that, you can ensure your business continuity.… Continue Reading
Key Considerations When Looking for a Cloud Services Provider - In order to ensure the business continuity, you have to make the right choice about the cloud service provider. You need PERFECTION so that, you can ensure your business continuity.… Continue Reading Basics of Microsoft Azure Cloud platform’s latest technology: Blockchain as a Service (BaaS) - Blockchain is a digitalized, decentralized, safe, shared, distributed ledger of all the cryptocurrency transactions. Blockchain is directly linked to the number of organizations or companies that participate in each of… Continue Reading
Basics of Microsoft Azure Cloud platform’s latest technology: Blockchain as a Service (BaaS) - Blockchain is a digitalized, decentralized, safe, shared, distributed ledger of all the cryptocurrency transactions. Blockchain is directly linked to the number of organizations or companies that participate in each of… Continue Reading Backup and Disaster Recovery – On premise and Cloud - DATA is the most vital business assets. Any harm to your data can lead to the downfall of your company. Keeping your data safe is the key to protect your… Continue Reading
Backup and Disaster Recovery – On premise and Cloud - DATA is the most vital business assets. Any harm to your data can lead to the downfall of your company. Keeping your data safe is the key to protect your… Continue Reading
 DDoS Attacks Decoded: Defending Against Modern Cyber Onslaughts - Delve into the disruptive realm of DDoS attacks, understanding their operations and motives. Learn how air-gapping and immutability fortify defenses, ensuring a resilient cybersecurity posture against relentless online assaults. Continue Reading
DDoS Attacks Decoded: Defending Against Modern Cyber Onslaughts - Delve into the disruptive realm of DDoS attacks, understanding their operations and motives. Learn how air-gapping and immutability fortify defenses, ensuring a resilient cybersecurity posture against relentless online assaults. Continue Reading How to Set Up Immutable Snapshots for Ransomware Protection - Discover the significance of immutable snapshots for enhanced data security. Explore their benefits, practical applications, and step-by-step setup guide to bolster your data protection strategy. Continue Reading
How to Set Up Immutable Snapshots for Ransomware Protection - Discover the significance of immutable snapshots for enhanced data security. Explore their benefits, practical applications, and step-by-step setup guide to bolster your data protection strategy. Continue Reading Defending Your Data: The Vital Role of Multi-Factor Authentication - Discover the power of multi-factor authentication (MFA) in modern data security. StoneFly's innovative storage solutions offer a seamless and robust approach to safeguarding your critical data. Enhance your data protection… Continue Reading
Defending Your Data: The Vital Role of Multi-Factor Authentication - Discover the power of multi-factor authentication (MFA) in modern data security. StoneFly's innovative storage solutions offer a seamless and robust approach to safeguarding your critical data. Enhance your data protection… Continue Reading How to add air-gapping and immutability to Veeam backup appliance - Even with a Veeam backup appliance, if your Veeam backups are accessible via the production network, then your backup and DR is vulnerable. Learn how to add air-gapping and immutability… Continue Reading
How to add air-gapping and immutability to Veeam backup appliance - Even with a Veeam backup appliance, if your Veeam backups are accessible via the production network, then your backup and DR is vulnerable. Learn how to add air-gapping and immutability… Continue Reading How to Setup & Use StoneFly’s Free Data Migration Software - Learn how to install, setup, and use StoneFly’s free data migration software and migrate your unstructured data volumes effortlessly. Continue Reading
How to Setup & Use StoneFly’s Free Data Migration Software - Learn how to install, setup, and use StoneFly’s free data migration software and migrate your unstructured data volumes effortlessly. Continue Reading How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading
How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading How to configure volume and copy volumes in SAN? - These series of articles are the step to step guide for the StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software. The articles will be discussing that, how you… Continue Reading
How to configure volume and copy volumes in SAN? - These series of articles are the step to step guide for the StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software. The articles will be discussing that, how you… Continue Reading How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading
How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading How to discover and add Storage resources in Storage Concentrator SCVM™ - This article will discuss the resources section in StoneFly Storage Concentrator, how to discover resources and how to add resources in StoneFly Storage Concentrator (SCVM). Continue Reading
How to discover and add Storage resources in Storage Concentrator SCVM™ - This article will discuss the resources section in StoneFly Storage Concentrator, how to discover resources and how to add resources in StoneFly Storage Concentrator (SCVM). Continue Reading Introduction to storage concentrator GUI - This article, is the second article which is meant to guide you, how to deploy different segments of GUI. The introductory article went through the process of launching the administrative… Continue Reading
Introduction to storage concentrator GUI - This article, is the second article which is meant to guide you, how to deploy different segments of GUI. The introductory article went through the process of launching the administrative… Continue Reading How to launch the administrative interface in your StoneFly Storage Concentrator - This article will guide you about StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software provides the interface through which a system administrator can configure and monitor different parts… Continue Reading
How to launch the administrative interface in your StoneFly Storage Concentrator - This article will guide you about StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software provides the interface through which a system administrator can configure and monitor different parts… Continue Reading How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading
How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading How to deploy software defined Virtual Machine (SCVM) on VMWare ESXi? - These articles will guide you that how can the users deploy software defined SCVM on VMware ESXi. This article is meant to guide you through the process of deploying. The… Continue Reading
How to deploy software defined Virtual Machine (SCVM) on VMWare ESXi? - These articles will guide you that how can the users deploy software defined SCVM on VMware ESXi. This article is meant to guide you through the process of deploying. The… Continue Reading How StoneFly delivers Data Transportability - Data Transportability is the migration of data between applications or cloud services; however, StoneFly adds more to the concept of data transportability. With StoneFly’s application of data transportability, it delivers… Continue Reading
How StoneFly delivers Data Transportability - Data Transportability is the migration of data between applications or cloud services; however, StoneFly adds more to the concept of data transportability. With StoneFly’s application of data transportability, it delivers… Continue Reading How to add a Failover plan in StoneFly Cloud Connect - Keeping backup of your data is the essential step which you should take for your company. Through backup you can save the copies of your data and by disaster recovery… Continue Reading
How to add a Failover plan in StoneFly Cloud Connect - Keeping backup of your data is the essential step which you should take for your company. Through backup you can save the copies of your data and by disaster recovery… Continue Reading How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading
How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading Ease of Data Protection: Cloud Backup to Microsoft Azure Storage - StoneFly encompasses the needs of the customers to provide only the easiest and effective methods to set up cloud backup and storage. The customers are taken out of distress to… Continue Reading
Ease of Data Protection: Cloud Backup to Microsoft Azure Storage - StoneFly encompasses the needs of the customers to provide only the easiest and effective methods to set up cloud backup and storage. The customers are taken out of distress to… Continue Reading How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading
How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading How to setup Veeam Cloud Connect for the Enterprise Virtual Machine in Microsoft Azure Portal - We have created two parts to facilitate you with step by step explanation of how you can setup Veeam Cloud Connect for an enterprise virtual machine in Microsoft Azure. The… Continue Reading
How to setup Veeam Cloud Connect for the Enterprise Virtual Machine in Microsoft Azure Portal - We have created two parts to facilitate you with step by step explanation of how you can setup Veeam Cloud Connect for an enterprise virtual machine in Microsoft Azure. The… Continue Reading- How to add disk drives & scale out NAS storage in Microsoft azure VM? - Azure faciliatets you to scale out your NAS storages. You can add additional drives and you can scale out the virtual machine as well, which enables you to add more… Continue Reading
 How to setup StoneFly Scale out NAS VMs in Microsoft Azure portal? - This article is intended to guide you through the entire process of setting up StoneFly’s scale out network attached storage (NAS) virtual machines (VMs) in Microsoft Azure portal. Make sure… Continue Reading
How to setup StoneFly Scale out NAS VMs in Microsoft Azure portal? - This article is intended to guide you through the entire process of setting up StoneFly’s scale out network attached storage (NAS) virtual machines (VMs) in Microsoft Azure portal. Make sure… Continue Reading
 How to Set Up S3 Object Storage for Veeam Data Platform - Step-by-step guide on configuring AWS S3 object storage or S3-compatible object storage as a Veeam backup and archiving target repository. This blog covers the complete process from mapping storage resources… Continue Reading
How to Set Up S3 Object Storage for Veeam Data Platform - Step-by-step guide on configuring AWS S3 object storage or S3-compatible object storage as a Veeam backup and archiving target repository. This blog covers the complete process from mapping storage resources… Continue Reading Upgrade 3-2-1 Rule with Veeam ONE v12’s Immutability and Monitoring - The 3-2-1 rule is a proven method for safeguarding data with multiple recoverable copies. In today's threat landscape, it's crucial to enhance the rule by incorporating immutability and continuous monitoring… Continue Reading
Upgrade 3-2-1 Rule with Veeam ONE v12’s Immutability and Monitoring - The 3-2-1 rule is a proven method for safeguarding data with multiple recoverable copies. In today's threat landscape, it's crucial to enhance the rule by incorporating immutability and continuous monitoring… Continue Reading How to add air-gapping and immutability to Veeam backup appliance - Even with a Veeam backup appliance, if your Veeam backups are accessible via the production network, then your backup and DR is vulnerable. Learn how to add air-gapping and immutability… Continue Reading
How to add air-gapping and immutability to Veeam backup appliance - Even with a Veeam backup appliance, if your Veeam backups are accessible via the production network, then your backup and DR is vulnerable. Learn how to add air-gapping and immutability… Continue Reading Best Cloud Backup: Veeam Cloud Connect to Azure - It's risky to store all your data at one place because your business becomes vulnerable to ransomware attacks. Cloud backup & DR offers an affordable and reliable solution to that… Continue Reading
Best Cloud Backup: Veeam Cloud Connect to Azure - It's risky to store all your data at one place because your business becomes vulnerable to ransomware attacks. Cloud backup & DR offers an affordable and reliable solution to that… Continue Reading Simplify your Data Center with a Unified Veeam Ready Appliance - Read how you can simplify your IT infrastructure by replacing multiple dedicated servers with our unified Veeam ready appliance (DR365V) - in turn, reducing costs and simplifying management. Continue Reading
Simplify your Data Center with a Unified Veeam Ready Appliance - Read how you can simplify your IT infrastructure by replacing multiple dedicated servers with our unified Veeam ready appliance (DR365V) - in turn, reducing costs and simplifying management. Continue Reading What is virtual SAN (vSAN) and why is it better than traditional SAN? - Learn everything you need to know about virtual SAN (vSAN) from its benefits, uses, features & why it's better than traditional SAN in this blog. Continue Reading
What is virtual SAN (vSAN) and why is it better than traditional SAN? - Learn everything you need to know about virtual SAN (vSAN) from its benefits, uses, features & why it's better than traditional SAN in this blog. Continue Reading Backup versus Replication – What’s the Difference - This article takes a look at data backup and data replication, two solutions that are very similar but have distinct differences. Continue Reading
Backup versus Replication – What’s the Difference - This article takes a look at data backup and data replication, two solutions that are very similar but have distinct differences. Continue Reading Backups aren’t Enough – Here’s Why Air-Gapping and Immutability are Necessary - Most IT professionals think about backups when they're considering data security, but the truth is that this isn't enough. Data can still be breached with a backup. Continue Reading
Backups aren’t Enough – Here’s Why Air-Gapping and Immutability are Necessary - Most IT professionals think about backups when they're considering data security, but the truth is that this isn't enough. Data can still be breached with a backup. Continue Reading Business Continuity with Veeam Replication, Failover & Failback - You can leverage Veeam replication, failover, and failback to ensure business continuity and reduce RTOs and RPOs. Learn more about how the Veeam replication capabilities work and how StoneFly solutions… Continue Reading
Business Continuity with Veeam Replication, Failover & Failback - You can leverage Veeam replication, failover, and failback to ensure business continuity and reduce RTOs and RPOs. Learn more about how the Veeam replication capabilities work and how StoneFly solutions… Continue Reading Remote Office/Branch Office Backup & DR: How to do it right - In this blog post, explore remote office/branch office backup and recovery challenges, how to overcome them, and how StoneFly backup & DR solutions help. Continue Reading
Remote Office/Branch Office Backup & DR: How to do it right - In this blog post, explore remote office/branch office backup and recovery challenges, how to overcome them, and how StoneFly backup & DR solutions help. Continue Reading 5 ways to protect your servers from ransomware attack - In this blog post, we’ll share 5 things that you can do to prevent successful ransomware attacks. Considering how frequent ransomware attacks target a business, if you aren’t prepared, your… Continue Reading
5 ways to protect your servers from ransomware attack - In this blog post, we’ll share 5 things that you can do to prevent successful ransomware attacks. Considering how frequent ransomware attacks target a business, if you aren’t prepared, your… Continue Reading How StoneFly and Veeam offer the best ransomware protection - Find out what makes StoneFly’s Veeam-ready backup and DR solution different than most mainstream solutions – and how it offers the best ransomware protection Continue Reading
How StoneFly and Veeam offer the best ransomware protection - Find out what makes StoneFly’s Veeam-ready backup and DR solution different than most mainstream solutions – and how it offers the best ransomware protection Continue Reading How to setup NAS backup repository for Veeam backup software - Learn how to create NFS or CIFS/SMB NAS volumes using StoneFly storage concentrator (SCVM) and configure them as target backup repositories for Veeam Availability suite version 10. Continue Reading
How to setup NAS backup repository for Veeam backup software - Learn how to create NFS or CIFS/SMB NAS volumes using StoneFly storage concentrator (SCVM) and configure them as target backup repositories for Veeam Availability suite version 10. Continue Reading Veeam-Ready Appliance with Immutable / WORM Storage - StoneFly Veeam-ready appliance enables users to provision WORM storage repositories for secure & compliant backup data storage. Learn more about the feature in this blog post. Continue Reading
Veeam-Ready Appliance with Immutable / WORM Storage - StoneFly Veeam-ready appliance enables users to provision WORM storage repositories for secure & compliant backup data storage. Learn more about the feature in this blog post. Continue Reading Protecting AWS Workloads with Veeam backup & replication to StoneFly Cloud - Veeam backup & replication to StoneFly Cloud provides a backup and disaster recovery for your Amazon EC2 instances. It is gives you the ability to automatically backup and recover data… Continue Reading
Protecting AWS Workloads with Veeam backup & replication to StoneFly Cloud - Veeam backup & replication to StoneFly Cloud provides a backup and disaster recovery for your Amazon EC2 instances. It is gives you the ability to automatically backup and recover data… Continue Reading Microsoft Office 365 Backup – Why is it Important? - Adoption of Office 365 is growing exponentially. Customers need to mitigate the risk of losing access to email and ensure availability for Office 365 users. In this blog we discuss… Continue Reading
Microsoft Office 365 Backup – Why is it Important? - Adoption of Office 365 is growing exponentially. Customers need to mitigate the risk of losing access to email and ensure availability for Office 365 users. In this blog we discuss… Continue Reading The Business Value of using StoneFly and Veeam Backup & Disaster Recovery Solution - Data is increasingly at the core of any business or organization, and is fueling new digital transformation initiatives. Data runs nearly every aspect of a company, from customer and employee… Continue Reading
The Business Value of using StoneFly and Veeam Backup & Disaster Recovery Solution - Data is increasingly at the core of any business or organization, and is fueling new digital transformation initiatives. Data runs nearly every aspect of a company, from customer and employee… Continue Reading Purpose-built Backup and DR appliance for Nutanix - Explore what risks businesses take by not deploying reliable backup and disaster recovery solutions for enterprise-level infrastructures like Nutanix. The article also sheds light on StoneFly’s purpose-built backup and DR… Continue Reading
Purpose-built Backup and DR appliance for Nutanix - Explore what risks businesses take by not deploying reliable backup and disaster recovery solutions for enterprise-level infrastructures like Nutanix. The article also sheds light on StoneFly’s purpose-built backup and DR… Continue Reading Veeam Backup & Replication Best Practices: # 4 – Data reduction techniques - Optimizing the cost or benefit of various backup techniques and storage technologies means we will need to understand business requirements associated with the use of backup data and retention requirements.… Continue Reading
Veeam Backup & Replication Best Practices: # 4 – Data reduction techniques - Optimizing the cost or benefit of various backup techniques and storage technologies means we will need to understand business requirements associated with the use of backup data and retention requirements.… Continue Reading Veeam Backup & Replication Best Practices: #3 – Architecture overview - Veeam Backup & Replication has a scale out architecture, in which multiple components (both for data processing and control) work together in a coordinated fashion. This blog provides a brief… Continue Reading
Veeam Backup & Replication Best Practices: #3 – Architecture overview - Veeam Backup & Replication has a scale out architecture, in which multiple components (both for data processing and control) work together in a coordinated fashion. This blog provides a brief… Continue Reading Veeam Backup & Replication Best Practices: #2 – Hypervisor, Backup Job and Restore - StoneFly and Veeam Offer state of the Art backup and disaster recovery solutions for Commercial, Public Sector and Cloud Service Providers. Veeam is the premier availability software for StoneFly, which… Continue Reading
Veeam Backup & Replication Best Practices: #2 – Hypervisor, Backup Job and Restore - StoneFly and Veeam Offer state of the Art backup and disaster recovery solutions for Commercial, Public Sector and Cloud Service Providers. Veeam is the premier availability software for StoneFly, which… Continue Reading Veeam Backup and Replication Best Practices: #1 – Backup Proxies - This article is the first in the series about the best practices about Veeam backup and replication. The article explores how enterprise IT environments can deploy and use backup proxies.… Continue Reading
Veeam Backup and Replication Best Practices: #1 – Backup Proxies - This article is the first in the series about the best practices about Veeam backup and replication. The article explores how enterprise IT environments can deploy and use backup proxies.… Continue Reading Backup Nutanix Infrastructures in Microsoft Azure with StoneFly and Veeam - This article explores what kind of enterprises can integrate cloud backup and disaster recovery to ensure business continuity and recovery for their enterprise workloads. Also explore the cloud backup and… Continue Reading
Backup Nutanix Infrastructures in Microsoft Azure with StoneFly and Veeam - This article explores what kind of enterprises can integrate cloud backup and disaster recovery to ensure business continuity and recovery for their enterprise workloads. Also explore the cloud backup and… Continue Reading Integrating Veeam PN for Microsoft Azure with StoneFly’s Enterprise Level Services - StoneFly and Veeam cloud connect services make up an efficient and reliable backup and disaster recovery solution. Integrating Veeam PN into the mix establishes a simple enterprise network that secures… Continue Reading
Integrating Veeam PN for Microsoft Azure with StoneFly’s Enterprise Level Services - StoneFly and Veeam cloud connect services make up an efficient and reliable backup and disaster recovery solution. Integrating Veeam PN into the mix establishes a simple enterprise network that secures… Continue Reading How Disaster Recovery as a Service (DRaaS) Works in the Veeam Cloud Connect - One of the challenges that the service provider (SP) needs to solve to offer disaster recovery as a service is mimicking the tenant network as SP cannot control the tenant… Continue Reading
How Disaster Recovery as a Service (DRaaS) Works in the Veeam Cloud Connect - One of the challenges that the service provider (SP) needs to solve to offer disaster recovery as a service is mimicking the tenant network as SP cannot control the tenant… Continue Reading Archiving Veeam Backups in Amazon Glacier - The advantage of storing data in Amazon Glacier is its low cost. And although Amazon glacier is designed for cold data with scarce chance of being recovered, the real challenge… Continue Reading
Archiving Veeam Backups in Amazon Glacier - The advantage of storing data in Amazon Glacier is its low cost. And although Amazon glacier is designed for cold data with scarce chance of being recovered, the real challenge… Continue Reading Office 365 Backup & Disaster Recovery: Challenges and Solutions - Communication is a key element of operation for enterprises. Office 365 is a mainstream email service provider. It is necessary to ensure that all elements of office 365 are secure,… Continue Reading
Office 365 Backup & Disaster Recovery: Challenges and Solutions - Communication is a key element of operation for enterprises. Office 365 is a mainstream email service provider. It is necessary to ensure that all elements of office 365 are secure,… Continue Reading Hybrid Cloud DR: On premises Backup and Offsite Replication with StoneFly and Veeam - Modern age is the era of big data. Cloud Backup is one of the solutions for the storage and Disaster Recovery. These Cloud backup files can be used to create… Continue Reading
Hybrid Cloud DR: On premises Backup and Offsite Replication with StoneFly and Veeam - Modern age is the era of big data. Cloud Backup is one of the solutions for the storage and Disaster Recovery. These Cloud backup files can be used to create… Continue Reading Cloud Backup and replication for Hyper-V Environments - Backup and disaster recovery are essential for enterprises around the globe because these services ensure data availability and recoverability. However, data security and protection is even more significant and comparison.… Continue Reading
Cloud Backup and replication for Hyper-V Environments - Backup and disaster recovery are essential for enterprises around the globe because these services ensure data availability and recoverability. However, data security and protection is even more significant and comparison.… Continue Reading Veeam Cloud Connect in Amazon AWS: Services of the Cloud - Veeam Cloud Connect in Amazon AWS provides customers with cloud backup services which resolve the problems customers are faced with. The Veeam cloud connect provides a turnkey-solution to customers who… Continue Reading
Veeam Cloud Connect in Amazon AWS: Services of the Cloud - Veeam Cloud Connect in Amazon AWS provides customers with cloud backup services which resolve the problems customers are faced with. The Veeam cloud connect provides a turnkey-solution to customers who… Continue Reading How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading
How to configure Veeam cloud connect for the Enterprise VM in Azure Portal? - This article is the second part of how to articles, which is meant to guide your through the process of setting up and configuring Veeam cloud connect for the enterprise… Continue Reading How to setup Veeam Cloud Connect for the Enterprise Virtual Machine in Microsoft Azure Portal - We have created two parts to facilitate you with step by step explanation of how you can setup Veeam Cloud Connect for an enterprise virtual machine in Microsoft Azure. The… Continue Reading
How to setup Veeam Cloud Connect for the Enterprise Virtual Machine in Microsoft Azure Portal - We have created two parts to facilitate you with step by step explanation of how you can setup Veeam Cloud Connect for an enterprise virtual machine in Microsoft Azure. The… Continue Reading Veeam and StoneFly the Right Solution for Backup - StoneFly aims to provide only the best storage to its customers. We revolve around the customers to cater to even those cloud backup solutions of the customers where others shut… Continue Reading
Veeam and StoneFly the Right Solution for Backup - StoneFly aims to provide only the best storage to its customers. We revolve around the customers to cater to even those cloud backup solutions of the customers where others shut… Continue Reading Hybrid Cloud Backup and Disaster Recovery with StoneFly and Veeam - StoneFly has partnered with Veeam to provide enterprise level backup and disaster recovery solutions. Veeam specializes in backup and replication solutions for on-premise based VMware and Microsoft Hyper-V environments. These… Continue Reading
Hybrid Cloud Backup and Disaster Recovery with StoneFly and Veeam - StoneFly has partnered with Veeam to provide enterprise level backup and disaster recovery solutions. Veeam specializes in backup and replication solutions for on-premise based VMware and Microsoft Hyper-V environments. These… Continue Reading StoneFly and Veeam Backup Solution for Office 365 in Cloud or on-premises - Veeam backup for Microsoft Office 365 provides organizations that are using it the ability to pull back down Office 365 email and data and back it up on premises or… Continue Reading
StoneFly and Veeam Backup Solution for Office 365 in Cloud or on-premises - Veeam backup for Microsoft Office 365 provides organizations that are using it the ability to pull back down Office 365 email and data and back it up on premises or… Continue Reading Why choose Veeam Cloud Connect using StoneFly Cloud Storage in Microsoft Azure? - Veeam and Microsoft have partnered with StoneFly to offer state-of-the-art storage options leveraging StoneFly’s Scale-Out NAS Cloud Storage in Azure and StoneFly Cloud for the ultimate backup and disaster recovery… Continue Reading
Why choose Veeam Cloud Connect using StoneFly Cloud Storage in Microsoft Azure? - Veeam and Microsoft have partnered with StoneFly to offer state-of-the-art storage options leveraging StoneFly’s Scale-Out NAS Cloud Storage in Azure and StoneFly Cloud for the ultimate backup and disaster recovery… Continue Reading StoneFly partners with Microsoft and Veeam for state of the art Cloud Services - StoneFly, Veeam and Microsoft: better together. On-premises data solutions require a lot of money and highly paid staff to manage data. StoneFly has partnered with Microsoft and Veeam to offer… Continue Reading
StoneFly partners with Microsoft and Veeam for state of the art Cloud Services - StoneFly, Veeam and Microsoft: better together. On-premises data solutions require a lot of money and highly paid staff to manage data. StoneFly has partnered with Microsoft and Veeam to offer… Continue Reading
 What Is A Software Storage Solution (SDS)? Introduction & Benefits - Software defined storage is a term that has been making the rounds in recent years. It’s not entirely new, but it’s an evolving concept and as such, there are still… Continue Reading
What Is A Software Storage Solution (SDS)? Introduction & Benefits - Software defined storage is a term that has been making the rounds in recent years. It’s not entirely new, but it’s an evolving concept and as such, there are still… Continue Reading How to update your StoneFusion & SCVM to the latest version - This blog shares the process of updating StoneFly’s patented storage OS (StoneFusion & SCVM) to the latest version. Each new update brings new features, bug fixes (if any), and patches… Continue Reading
How to update your StoneFusion & SCVM to the latest version - This blog shares the process of updating StoneFly’s patented storage OS (StoneFusion & SCVM) to the latest version. Each new update brings new features, bug fixes (if any), and patches… Continue Reading What makes converged storage the best data storage infrastructure - In this blog post, we take a look at converged storage infrastructure, what is it, how it works, how can you use it effectively, and what makes StoneFly USO the… Continue Reading
What makes converged storage the best data storage infrastructure - In this blog post, we take a look at converged storage infrastructure, what is it, how it works, how can you use it effectively, and what makes StoneFly USO the… Continue Reading Another Review – Another Award for Our Storage Operating System - FinancesOnline, a leading business software review platform awarded our enterprise storage operating system the 2019 Rising Star and Premium Usability awards in their recent review. Their survey concluded our user… Continue Reading
Another Review – Another Award for Our Storage Operating System - FinancesOnline, a leading business software review platform awarded our enterprise storage operating system the 2019 Rising Star and Premium Usability awards in their recent review. Their survey concluded our user… Continue Reading Data Center Hardware Overview: Disaggregated HA Appliances - This blog is the fourth in the series of blogs that explain StoneFly’s innovative data storage appliance hardware architecture. In this blog, explore the appliance architecture and key components of… Continue Reading
Data Center Hardware Overview: Disaggregated HA Appliances - This blog is the fourth in the series of blogs that explain StoneFly’s innovative data storage appliance hardware architecture. In this blog, explore the appliance architecture and key components of… Continue Reading iSCSI, NAS, Hyperconverged: Manage All with Award-Winning Software - StoneFusion is the ultimate software defined storage solution capable of facilitating NAS, iSCSI, converged, and hyperconverged enterprise workloads. StoneFusion enables data service integration and cloud storage integration making data storage… Continue Reading
iSCSI, NAS, Hyperconverged: Manage All with Award-Winning Software - StoneFusion is the ultimate software defined storage solution capable of facilitating NAS, iSCSI, converged, and hyperconverged enterprise workloads. StoneFusion enables data service integration and cloud storage integration making data storage… Continue Reading Transforming Traditional Data centers with the StoneFly USS Hyper-converged Appliance - The StoneFly USS Hyperconverged appliance combines server, networking and storage in as little as 3U of Rackspace and presents a solution for traditional datacenters to run any application or consolidate… Continue Reading
Transforming Traditional Data centers with the StoneFly USS Hyper-converged Appliance - The StoneFly USS Hyperconverged appliance combines server, networking and storage in as little as 3U of Rackspace and presents a solution for traditional datacenters to run any application or consolidate… Continue Reading Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading
Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading
How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading Deploy a Complete Business Model in the Cloud with the StoneFly SCVM™ - Data is essential for delivering value to your customers and outpacing your competitors. But as data growth accelerates and with 80% of new data being unstructured, finding a way to… Continue Reading
Deploy a Complete Business Model in the Cloud with the StoneFly SCVM™ - Data is essential for delivering value to your customers and outpacing your competitors. But as data growth accelerates and with 80% of new data being unstructured, finding a way to… Continue Reading Affordable Enterprise Cloud Based Server - Cloud has changed the way people do business. Cloud has empowered many people to consume technology. You have to choose a cloud service provider that handles all for you. StoneFly… Continue Reading
Affordable Enterprise Cloud Based Server - Cloud has changed the way people do business. Cloud has empowered many people to consume technology. You have to choose a cloud service provider that handles all for you. StoneFly… Continue Reading Eradicating storage and disaster recovery challenges with StoneFly SCVM - There is an increase in data day by day. With this increase in data, the traditional ways of data storage have failed to answer the data storage requirements of the… Continue Reading
Eradicating storage and disaster recovery challenges with StoneFly SCVM - There is an increase in data day by day. With this increase in data, the traditional ways of data storage have failed to answer the data storage requirements of the… Continue Reading Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading
Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading Why is SCVM™ perfect for Microsoft and VMware hypervisors - StoneFly’s SCVM™ delivers an enterprise-level, highly available and feature-rich storage solution that also provides native data protection. It’s a single solution that addresses storage requirements and backup and disaster recovery… Continue Reading
Why is SCVM™ perfect for Microsoft and VMware hypervisors - StoneFly’s SCVM™ delivers an enterprise-level, highly available and feature-rich storage solution that also provides native data protection. It’s a single solution that addresses storage requirements and backup and disaster recovery… Continue Reading How to configure volume and copy volumes in SAN? - These series of articles are the step to step guide for the StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software. The articles will be discussing that, how you… Continue Reading
How to configure volume and copy volumes in SAN? - These series of articles are the step to step guide for the StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software. The articles will be discussing that, how you… Continue Reading How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading
How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading How to discover and add Storage resources in Storage Concentrator SCVM™ - This article will discuss the resources section in StoneFly Storage Concentrator, how to discover resources and how to add resources in StoneFly Storage Concentrator (SCVM). Continue Reading
How to discover and add Storage resources in Storage Concentrator SCVM™ - This article will discuss the resources section in StoneFly Storage Concentrator, how to discover resources and how to add resources in StoneFly Storage Concentrator (SCVM). Continue Reading Introduction to storage concentrator GUI - This article, is the second article which is meant to guide you, how to deploy different segments of GUI. The introductory article went through the process of launching the administrative… Continue Reading
Introduction to storage concentrator GUI - This article, is the second article which is meant to guide you, how to deploy different segments of GUI. The introductory article went through the process of launching the administrative… Continue Reading How to launch the administrative interface in your StoneFly Storage Concentrator - This article will guide you about StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software provides the interface through which a system administrator can configure and monitor different parts… Continue Reading
How to launch the administrative interface in your StoneFly Storage Concentrator - This article will guide you about StoneFly storage concentrator GUI. The StoneFly Storage Concentrator™ appliance software provides the interface through which a system administrator can configure and monitor different parts… Continue Reading How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading
How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading How to deploy software defined Virtual Machine (SCVM) on VMWare ESXi? - These articles will guide you that how can the users deploy software defined SCVM on VMware ESXi. This article is meant to guide you through the process of deploying. The… Continue Reading
How to deploy software defined Virtual Machine (SCVM) on VMWare ESXi? - These articles will guide you that how can the users deploy software defined SCVM on VMware ESXi. This article is meant to guide you through the process of deploying. The… Continue Reading Resilience from ransomware with StoneFly SCVM - Today's cyber security threats are constantly evolving. Most companies have preventive security software to stop these types of attacks but no matter how secure we are vulnerable to cyber-crimes. Ransomware… Continue Reading
Resilience from ransomware with StoneFly SCVM - Today's cyber security threats are constantly evolving. Most companies have preventive security software to stop these types of attacks but no matter how secure we are vulnerable to cyber-crimes. Ransomware… Continue Reading What is Hyperconverged Infrastructure (HCI)? - Hyperconvergence is required to provide easy scaling and management. It is a single system that reduces data center complexity and increases scalability. Multiple nodes of the appliance can be clustered… Continue Reading
What is Hyperconverged Infrastructure (HCI)? - Hyperconvergence is required to provide easy scaling and management. It is a single system that reduces data center complexity and increases scalability. Multiple nodes of the appliance can be clustered… Continue Reading Closer look: StoneFly’s Innovative Storage Concentrator Virtual Machine (SCVM) - Software-defined storage (SDS), as purists argue, is any storage product that requires software to manage underlying hardware and control. The marketing term, software-defined storage is however, commonly associated with software… Continue Reading
Closer look: StoneFly’s Innovative Storage Concentrator Virtual Machine (SCVM) - Software-defined storage (SDS), as purists argue, is any storage product that requires software to manage underlying hardware and control. The marketing term, software-defined storage is however, commonly associated with software… Continue Reading Virtualization Containers and how they compare to Virtual Machines - In the world of technology, IT pros need to customize technology solutions to meet their physical and virtual infrastructure needs. Various industries and firms are using systematically important workloads. Increased… Continue Reading
Virtualization Containers and how they compare to Virtual Machines - In the world of technology, IT pros need to customize technology solutions to meet their physical and virtual infrastructure needs. Various industries and firms are using systematically important workloads. Increased… Continue Reading Things that you should look at when building a container ecosystem - Many enterprises have million budget and they want to build container environments. There are plenty of ecosystem tools which make the things easier for them. But there’s a lot of… Continue Reading
Things that you should look at when building a container ecosystem - Many enterprises have million budget and they want to build container environments. There are plenty of ecosystem tools which make the things easier for them. But there’s a lot of… Continue Reading Elastic Storage for Physical, Virtual and container environments - In the growing data world your storage should grow along with your business growth. Data is on the explosion and structured unstructured data is produced anywhere, anytime. The traditional storage… Continue Reading
Elastic Storage for Physical, Virtual and container environments - In the growing data world your storage should grow along with your business growth. Data is on the explosion and structured unstructured data is produced anywhere, anytime. The traditional storage… Continue Reading
 5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing…
5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing…  Botnets Unveiled: Navigating the Underworld of Cyber Threats - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security.
Botnets Unveiled: Navigating the Underworld of Cyber Threats - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security.  Demystifying SQL Injection: How It Works and How to Defend Against It - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security.
Demystifying SQL Injection: How It Works and How to Defend Against It - Discover in-depth insights on protecting your databases from SQL injection attacks with our comprehensive guide. Dive into detection, prevention, and best practices to fortify your security.  Remote Access Trojans (RATs): The Silent Invaders of Cybersecurity - Delve into the realm of Remote Access Trojans (RATs) – their tactics, impact, and defense strategies. Explore the evolving landscape of cyber threats.
Remote Access Trojans (RATs): The Silent Invaders of Cybersecurity - Delve into the realm of Remote Access Trojans (RATs) – their tactics, impact, and defense strategies. Explore the evolving landscape of cyber threats.  Finance Industry at Risk: Navigating the Ransomware Threat Landscape - As cyber threats loom large over the finance industry, understanding the gravity of ransomware's impact is paramount. Explore the repercussions, regulatory concerns, and proven strategies to safeguard your financial systems.
Finance Industry at Risk: Navigating the Ransomware Threat Landscape - As cyber threats loom large over the finance industry, understanding the gravity of ransomware's impact is paramount. Explore the repercussions, regulatory concerns, and proven strategies to safeguard your financial systems.  Immutable File-Level WORM: Setup Guide and Best Practices - Unleash the strength of Immutable File-Level WORM (FileLock) to secure your critical data. Safeguard against unauthorized changes and ransomware threats. Explore our step-by-step guide to implement this advanced data protection…
Immutable File-Level WORM: Setup Guide and Best Practices - Unleash the strength of Immutable File-Level WORM (FileLock) to secure your critical data. Safeguard against unauthorized changes and ransomware threats. Explore our step-by-step guide to implement this advanced data protection…  Preventing Data Loss: Importance of Volume Deletion Protection - Volume deletion protection provides the necessary safeguard to ensure data integrity and availability. Learn the importance of this feature and how it enhances data security and business continuity in this…
Preventing Data Loss: Importance of Volume Deletion Protection - Volume deletion protection provides the necessary safeguard to ensure data integrity and availability. Learn the importance of this feature and how it enhances data security and business continuity in this…  How to Stop Ransomware Attacks from Deleting Backup Data - Ransomware attacks pose a significant threat to backup data, leaving organizations vulnerable and with limited options. Discover effective strategies to protect your valuable backups and thwart ransomware's hold. Learn about…
How to Stop Ransomware Attacks from Deleting Backup Data - Ransomware attacks pose a significant threat to backup data, leaving organizations vulnerable and with limited options. Discover effective strategies to protect your valuable backups and thwart ransomware's hold. Learn about…  From Production to Protection: Securing Manufacturing Against Ransomware - Discover why the manufacturing industry is a prime target for ransomware attacks and learn crucial steps to protect your operations, data, and reputation from evolving cyber threats.
From Production to Protection: Securing Manufacturing Against Ransomware - Discover why the manufacturing industry is a prime target for ransomware attacks and learn crucial steps to protect your operations, data, and reputation from evolving cyber threats.  Compare Array vs Host vs Hypervisor vs Network-Based Replication - Explore the array, host, hypervisor, and network-based replication techniques. This blog provides a detailed comparison, covering use cases, advantages, and disadvantages. Make informed decisions for your data protection and disaster…
Compare Array vs Host vs Hypervisor vs Network-Based Replication - Explore the array, host, hypervisor, and network-based replication techniques. This blog provides a detailed comparison, covering use cases, advantages, and disadvantages. Make informed decisions for your data protection and disaster…
 Conti Ransomware: In-Depth Technical Breakdown - Explore the intricate workings of Conti ransomware, from its origins to notable attacks. Uncover mitigation strategies to fortify your defenses against this pervasive cyber threat. Continue Reading
Conti Ransomware: In-Depth Technical Breakdown - Explore the intricate workings of Conti ransomware, from its origins to notable attacks. Uncover mitigation strategies to fortify your defenses against this pervasive cyber threat. Continue Reading Supply Chain Attack: The Achilles’ Heel of Enterprise Security - Delve into the technical nuances of supply chain ransomware attacks and learn actionable strategies to improve your data security. Protect your critical data and mitigate risks effectively. Continue Reading
Supply Chain Attack: The Achilles’ Heel of Enterprise Security - Delve into the technical nuances of supply chain ransomware attacks and learn actionable strategies to improve your data security. Protect your critical data and mitigate risks effectively. Continue Reading How to Set Up S3 Object Storage for Veeam Data Platform - Step-by-step guide on configuring AWS S3 object storage or S3-compatible object storage as a Veeam backup and archiving target repository. This blog covers the complete process from mapping storage resources… Continue Reading
How to Set Up S3 Object Storage for Veeam Data Platform - Step-by-step guide on configuring AWS S3 object storage or S3-compatible object storage as a Veeam backup and archiving target repository. This blog covers the complete process from mapping storage resources… Continue Reading Watering Hole Attacks Unveiled: A Comprehensive Cyberthreat Overview - Dive into the intricate realm of watering hole cyberattacks and fortify your enterprise defenses. Uncover nuanced tactics, countermeasures, and emerging trends to stay one step ahead of cyberthreats. Continue Reading
Watering Hole Attacks Unveiled: A Comprehensive Cyberthreat Overview - Dive into the intricate realm of watering hole cyberattacks and fortify your enterprise defenses. Uncover nuanced tactics, countermeasures, and emerging trends to stay one step ahead of cyberthreats. Continue Reading Man-in-the-Middle Attack: Cyberthreat Amidst Data Streams - Discover proactive strategies against Man-in-the-Middle attacks. Stay ahead of evolving cyber threats with insights on prevention and emerging trends. Continue Reading
Man-in-the-Middle Attack: Cyberthreat Amidst Data Streams - Discover proactive strategies against Man-in-the-Middle attacks. Stay ahead of evolving cyber threats with insights on prevention and emerging trends. Continue Reading Innovate, Test, Patch, and Update: The Role of On-Demand Sandbox - Embark on a transformative journey in data management as we delve into the revolutionary realm of On-Demand Sandboxes. Explore seamless integration, purpose-built solutions, and cloud flexibility, unlocking the true potential… Continue Reading
Innovate, Test, Patch, and Update: The Role of On-Demand Sandbox - Embark on a transformative journey in data management as we delve into the revolutionary realm of On-Demand Sandboxes. Explore seamless integration, purpose-built solutions, and cloud flexibility, unlocking the true potential… Continue Reading 5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing… Continue Reading
5 Backup Strategy Options To Protect Sensitive Data In 2024 - In this blog, we delve into the essential components of a robust backup strategy. These five key options are imperative for any enterprise seeking to fortify its backup infrastructure, providing… Continue Reading Defending Your Data: The Vital Role of Multi-Factor Authentication - Discover the power of multi-factor authentication (MFA) in modern data security. StoneFly's innovative storage solutions offer a seamless and robust approach to safeguarding your critical data. Enhance your data protection… Continue Reading
Defending Your Data: The Vital Role of Multi-Factor Authentication - Discover the power of multi-factor authentication (MFA) in modern data security. StoneFly's innovative storage solutions offer a seamless and robust approach to safeguarding your critical data. Enhance your data protection… Continue Reading From Backup to Video Editing: 5 Use-Cases for NAS Storage - This blog explores the primary use-cases for Network-Attached Storage (NAS) and emphasizes the importance of choosing the right NAS solution for specific business needs. Readers will gain insights into how… Continue Reading
From Backup to Video Editing: 5 Use-Cases for NAS Storage - This blog explores the primary use-cases for Network-Attached Storage (NAS) and emphasizes the importance of choosing the right NAS solution for specific business needs. Readers will gain insights into how… Continue Reading Guide to Sizing Your Enterprise SAN Appliance for Optimal Storage - This blog provides IT managers with practical tips on sizing an enterprise SAN storage appliance, including storage capacity, CPU, and system memory. It also covers data protection, disaster recovery, and… Continue Reading
Guide to Sizing Your Enterprise SAN Appliance for Optimal Storage - This blog provides IT managers with practical tips on sizing an enterprise SAN storage appliance, including storage capacity, CPU, and system memory. It also covers data protection, disaster recovery, and… Continue Reading FC SAN vs iSCSI SAN: What’s the Difference? - Differentiate between Fibre Channel (FC) SAN vs iSCSI SAN: which is suitable for which use-case, and what are the pros and cons of each. Continue Reading
FC SAN vs iSCSI SAN: What’s the Difference? - Differentiate between Fibre Channel (FC) SAN vs iSCSI SAN: which is suitable for which use-case, and what are the pros and cons of each. Continue Reading NAS Security: What to Expect and How to Secure your NAS - Qlocker, Deadbolt, and other ransomware target NAS appliances. Learn what to expect and how to protect your file-level unstructured data from cyberthreats. Continue Reading
NAS Security: What to Expect and How to Secure your NAS - Qlocker, Deadbolt, and other ransomware target NAS appliances. Learn what to expect and how to protect your file-level unstructured data from cyberthreats. Continue Reading Log Archiving: What Challenges to Expect and How to Overcome Them - Challenges with log archiving, how to overcome them, and how to build a secure, low power, low carbon, zero ransomware log archiving system. Continue Reading
Log Archiving: What Challenges to Expect and How to Overcome Them - Challenges with log archiving, how to overcome them, and how to build a secure, low power, low carbon, zero ransomware log archiving system. Continue Reading SAN vs NAS vs DAS – A Closer Look - What's the difference between SAN vs NAS vs DAS? What are the advantages of each? When should you use them? And which data storage platform should you choose for your… Continue Reading
SAN vs NAS vs DAS – A Closer Look - What's the difference between SAN vs NAS vs DAS? What are the advantages of each? When should you use them? And which data storage platform should you choose for your… Continue Reading Protecting Video Surveillance Storage: How To Keep Video Data Safe - Learn why do you need to protect your video surveillance storage systems and how to do so using backup and disaster recovery solutions with air-gapping, immutability, and snapshots. Continue Reading
Protecting Video Surveillance Storage: How To Keep Video Data Safe - Learn why do you need to protect your video surveillance storage systems and how to do so using backup and disaster recovery solutions with air-gapping, immutability, and snapshots. Continue Reading How to setup NAS backup repository for Veeam backup software - Learn how to create NFS or CIFS/SMB NAS volumes using StoneFly storage concentrator (SCVM) and configure them as target backup repositories for Veeam Availability suite version 10. Continue Reading
How to setup NAS backup repository for Veeam backup software - Learn how to create NFS or CIFS/SMB NAS volumes using StoneFly storage concentrator (SCVM) and configure them as target backup repositories for Veeam Availability suite version 10. Continue Reading How Clustered HCI Appliances Ensure Hyper-Availability - What makes StoneFly TwinHCI systems the best high availability clustered HCI appliance solution in the market? Find the answer to this question and more in this blog post. Continue Reading
How Clustered HCI Appliances Ensure Hyper-Availability - What makes StoneFly TwinHCI systems the best high availability clustered HCI appliance solution in the market? Find the answer to this question and more in this blog post. Continue Reading Best VMware Live VM Migration Solution in the Market - VM migration is typically a disruptive process. Many businesses need an alternative to this disruptive migration process. To help with that, we’ve introduced live VM migration solutions that include a… Continue Reading
Best VMware Live VM Migration Solution in the Market - VM migration is typically a disruptive process. Many businesses need an alternative to this disruptive migration process. To help with that, we’ve introduced live VM migration solutions that include a… Continue Reading Considerations to Make While Planning NAS in AWS Cloud - This blog includes an overview of key deployment considerations including NAS in AWS cloud instance size, networking requirements and memory. Continue Reading
Considerations to Make While Planning NAS in AWS Cloud - This blog includes an overview of key deployment considerations including NAS in AWS cloud instance size, networking requirements and memory. Continue Reading Taking a Closer Look at Cloud Storage Gateways - What are cloud storage gateways? When should you use them? And what makes StoneFly Smart cloud storage gateway the best in the market? Find answers to these questions and more… Continue Reading
Taking a Closer Look at Cloud Storage Gateways - What are cloud storage gateways? When should you use them? And what makes StoneFly Smart cloud storage gateway the best in the market? Find answers to these questions and more… Continue Reading Data Center Hardware Overview: Scale Out Appliances - This blog is the third in the series of blogs that explore StoneFly’s innovative storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and the… Continue Reading
Data Center Hardware Overview: Scale Out Appliances - This blog is the third in the series of blogs that explore StoneFly’s innovative storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and the… Continue Reading Data Center Hardware Overview: Dual Node Shared Nothing - This blog is the second in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading
Data Center Hardware Overview: Dual Node Shared Nothing - This blog is the second in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading Data Center Hardware Overview: Integrated Appliance - This blog is the first in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading
Data Center Hardware Overview: Integrated Appliance - This blog is the first in the series of blogs that explore StoneFly’s innovative data storage appliance hardware. In this blog post, explore the architecture, key components, storage capacities, and… Continue Reading What makes StoneFly SSO NAS Appliances Ransomware-Proof? - This article explores the vulnerabilities of traditional NAS systems and what makes them prone to data loss. The article also provides insight on what makes StoneFly SSO NAS appliances the… Continue Reading
What makes StoneFly SSO NAS Appliances Ransomware-Proof? - This article explores the vulnerabilities of traditional NAS systems and what makes them prone to data loss. The article also provides insight on what makes StoneFly SSO NAS appliances the… Continue Reading Public versus Private: Which Cloud is Best for Enterprise Backups? - Enterprises have to make a decision when it comes to selecting which cloud is the best for their use-case either public or private. It tends to be a difficult decision.… Continue Reading
Public versus Private: Which Cloud is Best for Enterprise Backups? - Enterprises have to make a decision when it comes to selecting which cloud is the best for their use-case either public or private. It tends to be a difficult decision.… Continue Reading Best Way to Remove Single Point of Failure from Your Storage Infrastructure - Business continuity is important for every industry. Single point of failure in data storage systems risk disruption and disruption is very costly. In this blog learn what’s single point of… Continue Reading
Best Way to Remove Single Point of Failure from Your Storage Infrastructure - Business continuity is important for every industry. Single point of failure in data storage systems risk disruption and disruption is very costly. In this blog learn what’s single point of… Continue Reading Cloud Storage Adoption: Challenges & Solutions - Enterprise cloud storage integration can be challenging since they have to consider costs, bandwidth usage, integration complexities and other similar questions. StoneFly helps meet these challenges and deliver more value… Continue Reading
Cloud Storage Adoption: Challenges & Solutions - Enterprise cloud storage integration can be challenging since they have to consider costs, bandwidth usage, integration complexities and other similar questions. StoneFly helps meet these challenges and deliver more value… Continue ReadingDo you want scalable architecture? - Ask yourself, will it not be amazing if you get automated scalable solution? If you don’t have to waste your money on extra racks of storage. Well, Of course for… Continue Reading
 Demystifying Cloud Archiving & its Role in Business Environments - What are the challenges that businesses face without cloud archiving? What really is cloud archiving and what are its benefits? This article answers these questions and introduces the idea that… Continue Reading
Demystifying Cloud Archiving & its Role in Business Environments - What are the challenges that businesses face without cloud archiving? What really is cloud archiving and what are its benefits? This article answers these questions and introduces the idea that… Continue Reading Benefits of Using the StoneFly Cloud Archiving Solution - The StoneFly Cloud Archiving solution provides a low-cost storage service built for data archival. One of the benefits of the Cloud Archiving solution is you can start archiving your storage… Continue Reading
Benefits of Using the StoneFly Cloud Archiving Solution - The StoneFly Cloud Archiving solution provides a low-cost storage service built for data archival. One of the benefits of the Cloud Archiving solution is you can start archiving your storage… Continue Reading Transforming Traditional Data centers with the StoneFly USS Hyper-converged Appliance - The StoneFly USS Hyperconverged appliance combines server, networking and storage in as little as 3U of Rackspace and presents a solution for traditional datacenters to run any application or consolidate… Continue Reading
Transforming Traditional Data centers with the StoneFly USS Hyper-converged Appliance - The StoneFly USS Hyperconverged appliance combines server, networking and storage in as little as 3U of Rackspace and presents a solution for traditional datacenters to run any application or consolidate… Continue Reading Short Story: The Relation between Cloud Storage and Cloud Backup - The term “Cloud” has become mainstream but there’s still quite a bit of confusion on the application of the cloud. In this article, explore the difference between cloud storage and… Continue Reading
Short Story: The Relation between Cloud Storage and Cloud Backup - The term “Cloud” has become mainstream but there’s still quite a bit of confusion on the application of the cloud. In this article, explore the difference between cloud storage and… Continue Reading Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading
Reduce Costs and Move Data to Azure, AWS or any S3 Compatible Cloud - In our webinar: “Reduce costs and Move data to Azure, AWS or any S3 compatible Cloud” we discussed StoneFly Smart Cloud Gateway product. The enterprise-level cloud gateway solution enables businesses… Continue Reading VSO™ Appliance: Affordable Data Storage, Backup & Disaster Recovery - Data storage, backup and disaster recovery are costly but important for IT driven businesses. In order to facilitate budget conscious businesses, StoneFly offers the VSO™ appliance series comprising of affordable… Continue Reading
VSO™ Appliance: Affordable Data Storage, Backup & Disaster Recovery - Data storage, backup and disaster recovery are costly but important for IT driven businesses. In order to facilitate budget conscious businesses, StoneFly offers the VSO™ appliance series comprising of affordable… Continue ReadingBuild a Scalable & Future-proof Data center - StoneFly offers a number of enterprise-grade solutions that can be used to build a scalable and future proof data center. This article explores some of StoneFly’s enterprise-grade storage technology that… Continue Reading
 How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading
How to setup a SAN cluster by configuring target portals? - SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s… Continue Reading Network Attached Storage (NAS) for Unstructured Big Data - Unstructured big data is growing exponentially. Analyzing and managing this data enables IT driven businesses to add value to their core operations. With StoneFly’s Network Attached Storage appliances businesses can… Continue Reading
Network Attached Storage (NAS) for Unstructured Big Data - Unstructured big data is growing exponentially. Analyzing and managing this data enables IT driven businesses to add value to their core operations. With StoneFly’s Network Attached Storage appliances businesses can… Continue Reading Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading
Simplified Storage, Backup & DR with StoneFly SCVM™ - Dedicated solutions are complex, expensive and inefficient. As the workload volumes increase the complexity and costs increase. Instead of deploying dedicated solutions, IT environments can leverage their existing storage resources… Continue Reading How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading
How can you restore encryption USB device in SAN - This is the fourth article in the StoneFly Storage Concentrator Series. The series was created to help users understand how to use the StoneFly Storage Concentrator™ (SSC). This post guides… Continue Reading How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading
How to expand volumes in SAN? - The series of articles are meant to guide you how to deploy different segments of GUI. The previous article was meant to guide you how to configure and copy volumes… Continue Reading Things to know before considering SAN - SAN appliances can store files and can work as storage for specific applications like databases and Virtual machine file systems. In SAN data transportation is much efficient and reliable. Each… Continue Reading
Things to know before considering SAN - SAN appliances can store files and can work as storage for specific applications like databases and Virtual machine file systems. In SAN data transportation is much efficient and reliable. Each… Continue Reading Understanding Erasure Coding - Erasure Coding is the data protection method through which data is broken into sectors. Then data is encoded with redundant data pieces and stored across different storage media. This article… Continue Reading
Understanding Erasure Coding - Erasure Coding is the data protection method through which data is broken into sectors. Then data is encoded with redundant data pieces and stored across different storage media. This article… Continue Reading Storage Snapshot technology: techniques and details - When selecting a snapshot technology from a vendor one must carefully consider the requirements and the environment of the enterprise, which is about to deploy the technology. The main aim… Continue Reading
Storage Snapshot technology: techniques and details - When selecting a snapshot technology from a vendor one must carefully consider the requirements and the environment of the enterprise, which is about to deploy the technology. The main aim… Continue Reading Understanding Scalability in Data Storage - The demands of storage are increasing, scalability is the feature which will address the data growth and enable businesses to effectively leverage their data. This article explores the concept, working… Continue Reading
Understanding Scalability in Data Storage - The demands of storage are increasing, scalability is the feature which will address the data growth and enable businesses to effectively leverage their data. This article explores the concept, working… Continue Reading Network Attached Storage (NAS) Appliance: Practicality and Usage - NAS storage appliances can effectively address the storage requirements of businesses while reducing latency and facilitating remote accessibility to data. This makes NAS storage appliances the prime choice for unstructured… Continue Reading
Network Attached Storage (NAS) Appliance: Practicality and Usage - NAS storage appliances can effectively address the storage requirements of businesses while reducing latency and facilitating remote accessibility to data. This makes NAS storage appliances the prime choice for unstructured… Continue Reading- SAN: Construction, Usage and its role in Business Continuity Management - For business continuity management you require SAN. SAN is a high speed network which provides shared pool of storage devices to several servers. Business continuity management is a framework that… Continue Reading
 Closer look: StoneFly’s Innovative Storage Concentrator Virtual Machine (SCVM) - Software-defined storage (SDS), as purists argue, is any storage product that requires software to manage underlying hardware and control. The marketing term, software-defined storage is however, commonly associated with software… Continue Reading
Closer look: StoneFly’s Innovative Storage Concentrator Virtual Machine (SCVM) - Software-defined storage (SDS), as purists argue, is any storage product that requires software to manage underlying hardware and control. The marketing term, software-defined storage is however, commonly associated with software… Continue Reading How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading
How The Cloud Solves Data Storage Challenges - Having loads of data from reliable sources is just not enough. What to do with that data is the most important part as organizations use the data in effective ways… Continue Reading Storage System Technologies and their Configurations - An enterprise can devise their perfect storage solution using a specific storage architecture in a specific configuration. In order to do that, enterprises need to identify their data requirements. Only… Continue Reading
Storage System Technologies and their Configurations - An enterprise can devise their perfect storage solution using a specific storage architecture in a specific configuration. In order to do that, enterprises need to identify their data requirements. Only… Continue Reading Enterprise NAS Storage Solution for Big Data Storage Challenges - Big data storage requires reduced latency, manageability, ability to support high IOPS and data security and protection. These challenges can be overcome using traditional storage; however, the cost implications and… Continue Reading
Enterprise NAS Storage Solution for Big Data Storage Challenges - Big data storage requires reduced latency, manageability, ability to support high IOPS and data security and protection. These challenges can be overcome using traditional storage; however, the cost implications and… Continue Reading Enterprise Storage Optimization with The StoneFly CacheCloud Storage Appliance - Everyone is exploring cloud for its utilization and benefits. Enterprises can use cloud-based services for multiple purposes and increase their productivity, add value to their data all while protecting and… Continue Reading
Enterprise Storage Optimization with The StoneFly CacheCloud Storage Appliance - Everyone is exploring cloud for its utilization and benefits. Enterprises can use cloud-based services for multiple purposes and increase their productivity, add value to their data all while protecting and… Continue Reading Internet of Things, Big Data and Scale-Out NAS - In today’s world the use of data has become ever important with greater and greater technology being used to bring meaning to every industry. Massive amounts of data are being… Continue Reading
Internet of Things, Big Data and Scale-Out NAS - In today’s world the use of data has become ever important with greater and greater technology being used to bring meaning to every industry. Massive amounts of data are being… Continue Reading Scale-Out NAS Storage: An Intact Solution to Your Storage Needs - Rapid increases in data usage around the world have created greater demands for data storage. Businesses are now looking for backup solutions which are highly specialized in meeting their storage… Continue Reading
Scale-Out NAS Storage: An Intact Solution to Your Storage Needs - Rapid increases in data usage around the world have created greater demands for data storage. Businesses are now looking for backup solutions which are highly specialized in meeting their storage… Continue Reading Why Storage Companies Are Partnering with StoneFly for Cloud Storage - Cloud has been developed over the period of time to avoid putting the users in hassle. It is a kind of an Internet-Based-Service offered on demand to users. These users… Continue Reading
Why Storage Companies Are Partnering with StoneFly for Cloud Storage - Cloud has been developed over the period of time to avoid putting the users in hassle. It is a kind of an Internet-Based-Service offered on demand to users. These users… Continue Reading Big Data Storage Challenges and Solutions in Genomics - Big data refers to the vast volumes and types of information that companies can now collect and process using increasingly high-tech systems. Genomics research leads to a huge lakes of… Continue Reading
Big Data Storage Challenges and Solutions in Genomics - Big data refers to the vast volumes and types of information that companies can now collect and process using increasingly high-tech systems. Genomics research leads to a huge lakes of… Continue Reading- PACS Storage: Addressing the Healthcare Industry File Growth Challenge - Taking care of loads of populations, providers of medical services offer extensive medical services throughout the world. The services of these facilities are increasing by the second as more and… Continue Reading
 Cloud Backup and Storage Providing a Solution to all Your Storage Needs - StoneFly’s Scale-Out NAS cloud storage in Microsoft Azure partnered with Veeam has provided the most intact and applicable solution to all your storage needs. Continue Reading
Cloud Backup and Storage Providing a Solution to all Your Storage Needs - StoneFly’s Scale-Out NAS cloud storage in Microsoft Azure partnered with Veeam has provided the most intact and applicable solution to all your storage needs. Continue Reading Introduction to The StoneFly Scale-Out NAS Storage - The quantity of computer data generated on planet earth is growing exponentially for many reasons. Are you ready to handle the explosive growth of unstructured data? Chances are you are… Continue Reading
Introduction to The StoneFly Scale-Out NAS Storage - The quantity of computer data generated on planet earth is growing exponentially for many reasons. Are you ready to handle the explosive growth of unstructured data? Chances are you are… Continue Reading Ceph Storage for Object Storage Workloads - There is one thing constant in data, that it is growing every day. Enterprises are trying too hard to meet the growing demands without sacrificing the performance and reliability. So… Continue Reading
Ceph Storage for Object Storage Workloads - There is one thing constant in data, that it is growing every day. Enterprises are trying too hard to meet the growing demands without sacrificing the performance and reliability. So… Continue Reading StoneFly’s Scale-Out NAS Storage plug-in for Hadoop - Hadoop is an open source framework that manages, data processing and storage for big data applications which are running in clustered systems. Various forms of structured, unstructured data can be… Continue Reading
StoneFly’s Scale-Out NAS Storage plug-in for Hadoop - Hadoop is an open source framework that manages, data processing and storage for big data applications which are running in clustered systems. Various forms of structured, unstructured data can be… Continue Reading What is a Storage Area Network (SAN) – Advantages, Use Cases and How it Differs from NAS - Continue Reading
What is a Storage Area Network (SAN) – Advantages, Use Cases and How it Differs from NAS - Continue Reading