In this comprehensive guide, we delve into the intricate workings of DDoS attacks, exploring their tactics, motivations, and impact on targeted entities.
Moreover, we shed light on essential strategies to prepare for and mitigate the risks posed by these relentless digital barrages, with a special emphasis on leveraging air-gapping and immutability to fortify our defenses.
Definition and Impact of Distributed Denial of Service (DDoS) Attacks
What are DDoS attacks?
DDoS (Distributed Denial of Service) attacks are malicious attempts to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of traffic. The goal is to make the targeted system or network resource unavailable to its intended users, causing loss of revenue, reputation damage, and potential legal repercussions.
Attackers typically use a network of compromised devices, often called a botnet, to orchestrate these attacks, making them hard to trace back to a single source.
Impact of DDoS Attacks on Organizations
The repercussions of a DDoS attack on an organization are profound and intricate, with far-reaching consequences:
- Operational Disruption: DDoS attacks disrupt regular operations, causing online services to become unavailable. This outage directly translates into substantial financial losses, significantly impacting businesses heavily reliant on digital platforms.
- Reputation Damage: DDoS attacks tarnish an organization’s reputation, eroding customer trust and confidence. The aftermath of such an attack can be more detrimental in the long run than the immediate financial repercussions. Rebuilding trust and re-establishing the brand can be a long and arduous process.
- Costs and Resource Drain: Managing the aftermath of a DDoS attack is a resource-intensive endeavor. It involves investigation, mitigation, and service restoration. These steps incur significant costs, demanding extensive time and resources from the organization.
The domino effect of a DDoS attack resonates across the entire organizational ecosystem, impacting not just the bottom line, but also the very fabric of trust and operational stability. It underscores the criticality of fortifying defenses against such malicious assaults to ensure the resilience and continuity of business operations.
How DDoS Attacks Work
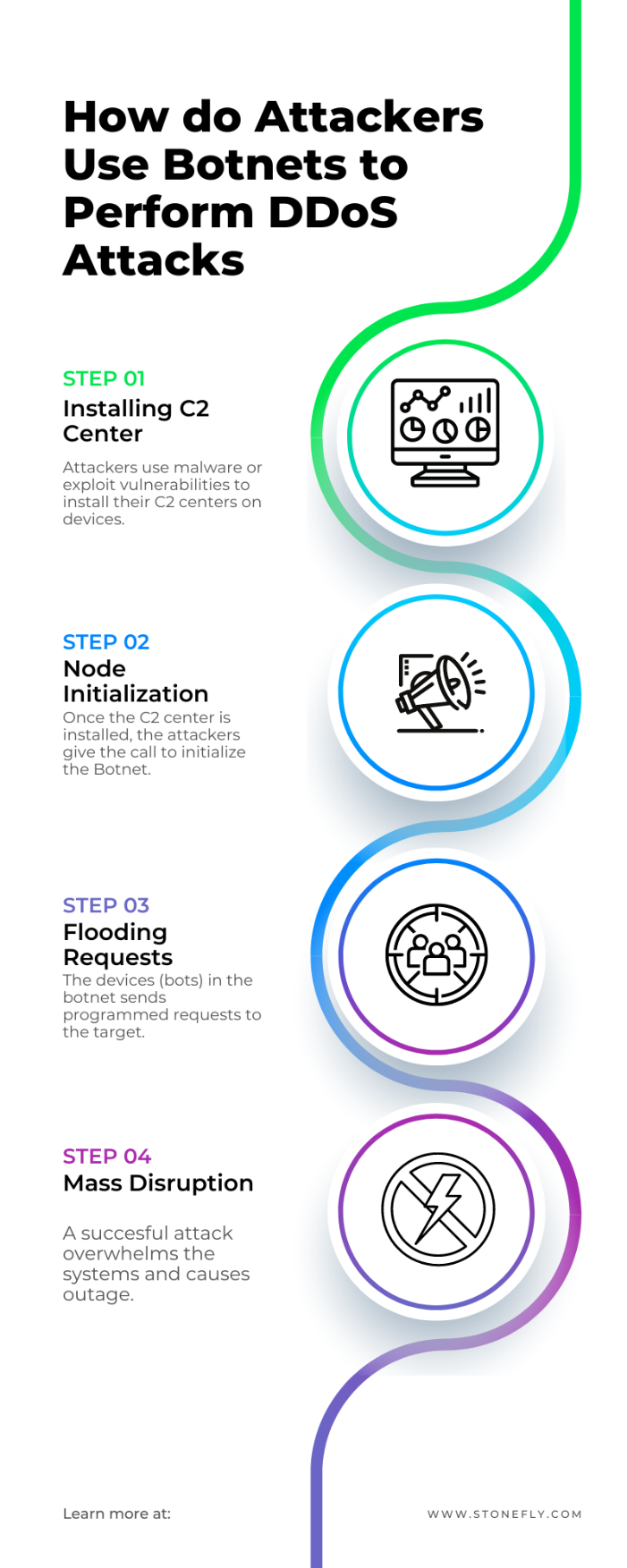
Fundamentals of DDoS Attacks
DDoS (Distributed Denial of Service) attacks are orchestrated attempts to overwhelm a target server, network, or service, rendering it inaccessible to users. Understanding the fundamentals of how DDoS attacks operate is vital in fortifying against them:
- Traffic Overload: DDoS attacks flood the target with an enormous volume of traffic. This influx overwhelms the target’s resources such as bandwidth, processing power, or memory.
- Botnets and Amplification: Attackers often control a network of compromised devices called botnets. These bots, under the attacker’s command, amplify the attack’s impact by sending requests to the target. This amplification multiplies the volume of traffic directed at the target.
- Goal of Exhaustion: The ultimate aim is to exhaust the target’s resources to a point where legitimate users are denied access. This denies services to genuine users, causing disruption and frustration.
Different Types of DDoS Attacks
DDoS attacks manifest in various forms, each targeting different aspects of a target’s infrastructure. Understanding these types is crucial for effective mitigation:
- Volumetric Attacks: These attacks aim to overwhelm a network’s bandwidth by flooding it with a massive volume of traffic. UDP (User Datagram Protocol) or ICMP (Internet Control Message Protocol) floods are common volumetric attacks.
- Protocol Attacks: Protocol attacks exploit weaknesses in network protocols. For instance, SYN flood attacks exploit the TCP/IP handshake process, causing the target to allocate resources for incomplete connections, eventually exhausting them.
- Application Layer Attacks: These attacks target the application layer of a network, focusing on specific applications or services. For example, HTTP floods overload web servers by generating numerous requests.
Techniques Employed by DDoS Attackers
DDoS attackers employ sophisticated techniques to maximize the impact of their attacks:
- IP Spoofing: Attackers mask their originating IP addresses, making it difficult to trace the attacks back to the source. This helps evade detection and mitigation.
- Botnet Utilization: By controlling a network of compromised devices (botnets), attackers can coordinate a massive volume of traffic to overwhelm the target.
- Amplification Attacks: Attackers use reflection or amplification techniques, exploiting vulnerable servers to amplify their attack traffic, making it more potent.
Targeting Victims: The Anatomy of a DDoS Attack
How Hackers Select Victims for DDoS Attacks
Before launching a DDoS attack, attackers meticulously choose and profile their targets:
- Industry and Sector Relevance: Attackers often target organizations based on their industry. For instance, a financial institution might be targeted to cause financial losses or tarnish its reputation.
- Online Footprint: Assessing the target’s online presence, including websites, applications, and services, helps attackers identify vulnerabilities and potential impact points.
- Resource Evaluation: Understanding the target’s IT infrastructure, network capabilities, and security measures helps attackers plan an attack that can overwhelm their resources effectively.
How DDoS Attacks are Launched
DDoS attacks follow a systematic approach, each step calibrated to maximize disruption:
- Reconnaissance: Attackers gather information about the target, identifying weak points and potential vulnerabilities.
- Botnet Preparation: Building or accessing a network of compromised devices (botnet) to execute the attack is a critical step. This involves infecting devices with malware that allows the attacker to control them.
- Command and Control (C&C): The attacker establishes control over the botnet, usually through a centralized server, to issue commands for the impending attack.
- Attack Execution: Using the compromised devices, the attacker initiates the attack, flooding the target with an overwhelming volume of traffic.
- Monitoring and Adaptation: Throughout the attack, the attacker monitors its effectiveness and adjusts strategies to bypass any mitigation efforts.
Common Motives Behind DDoS Attacks
Understanding the motives behind DDoS attacks is essential in formulating effective mitigation strategies:
- Hacktivism: Activists and hacktivist groups launch DDoS attacks to promote a social, political, or ideological message or to protest against an organization or government.
- Competitive Advantage: Rival companies may target competitors to gain a competitive edge by disrupting their services and tarnishing their reputation.
- Financial Gains: Some attackers aim for financial gains by extorting targeted organizations, demanding a ransom to cease the DDoS attack.
- Distraction for Other Attacks: DDoS attacks are used as a smokescreen to divert attention from other malicious activities, such as data breaches or network infiltrations.
How to Prepare for DDoS Attacks
Understanding Vulnerabilities and Risks
Understanding vulnerabilities that can make an organization susceptible to DDoS attacks is crucial:
- Network Vulnerabilities: Weaknesses in the network infrastructure can be exploited by DDoS attackers to overload and disrupt network services.
- Application Vulnerabilities: Vulnerabilities within applications can be targeted, making applications unresponsive or slowing them down significantly during an attack.
- Bandwidth Limitations: Even organizations with adequate bandwidth can be overwhelmed during a DDoS attack, highlighting the need for effective traffic management strategies.
Importance of Proactive DDoS Preparedness
Preparedness is key to mitigating the impact of a DDoS attack:
- Real-time Monitoring: Implementing real-time monitoring of network traffic helps in early detection of anomalies, allowing for swift response to mitigate potential DDoS attacks.
- Incident Response Plans: Developing detailed incident response plans specific to DDoS attacks ensures a structured and organized approach during an attack, minimizing damage and downtime.
- DDoS Simulations and Drills: Conducting regular DDoS attack simulations and response drills enables the organization to evaluate the effectiveness of its incident response plans.
The Role of a Comprehensive Disaster Recovery Plan
A comprehensive disaster recovery plan is essential for DDoS preparedness and effective recovery:
- Data Backup and Redundancy: Regular and automated backups of critical data, preferably in an air-gapped and immutable storage system, ensure data integrity and availability even during a DDoS attack.
- Failover Mechanisms: Implementing failover mechanisms and redundant network configurations ensures that services can quickly switch to backup systems in the event of an attack.
- Incident Communication Strategy: Having a well-defined communication strategy to inform stakeholders, clients, and users during and after a DDoS attack is vital to maintaining trust and transparency.
How to Mitigate the Risk of DDoS Attacks
Air-Gapping as a Defensive Strategy
Air-gapping is a critical defense strategy against DDoS attacks, creating an isolated environment that is disconnected from any external network, rendering it immune to online attacks:
- Network Isolation: Air-gapped systems are physically or logically isolated from the internet and other networks, making it extremely challenging for DDoS attacks to penetrate or disrupt these systems.
- Secure Data Storage: Storing critical data in air-gapped environments ensures its safety during a DDoS attack. Even if the online infrastructure is compromised, the offline, air-gapped data remains secure and intact.
Immutability: Safeguarding Data from DDoS Attacks
Data immutability is a powerful defense mechanism that protects against unauthorized alterations or deletion of critical data during a DDoS attack:
- Protection from Data Tampering: Immutability ensures that once data is written, it cannot be altered or deleted, guarding against malicious attempts to manipulate or corrupt data during a DDoS attack.
- Ensuring Data Integrity: Immutable data guarantees that the original, unaltered information remains intact, providing a trustworthy source of truth for critical operations and decision-making, even amidst a DDoS attack.
Backup and Disaster Recovery: Ensuring Business Continuity
- Regular Backups: Implementing regular automated backups of critical data is fundamental. These backups should be stored in secure, isolated environments, following the air-gapping principle.
- Redundancy and Failover: Creating redundant systems and failover mechanisms ensures continuous availability of services, even in the face of a DDoS attack. This allows for a seamless transition to backup systems.
- Incident Response Plan: Having a well-structured incident response plan specific to DDoS attacks is crucial. This plan should outline steps for quick detection, containment, eradication, and recovery following a DDoS attack.
DDoS Mitigation Services and Tools
- DDoS Mitigation Services: Acquiring the services of DDoS mitigation providers can be invaluable. These experts employ advanced techniques and technologies to detect, mitigate, and absorb DDoS traffic, ensuring minimal disruption.
- Traffic Scrubbing Centers: Utilizing traffic scrubbing centers allows for real-time monitoring and filtering of incoming traffic. Malicious traffic is identified and separated from legitimate traffic before reaching the organization’s network.
- Content Delivery Networks (CDNs): Leveraging CDNs assists in distributing traffic across various servers, reducing the load on the organization’s infrastructure and mitigating the impact of DDoS attacks.
Network Security Measures to Counter DDoS Attacks
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): Employing IDS and IPS provides real-time monitoring and automated responses to suspicious activities, aiding in early detection and prevention of potential DDoS attacks.
- Firewall Configuration: Ensuring firewalls are optimally configured and updated is essential. Firewalls act as the first line of defense against DDoS attacks, filtering traffic and blocking malicious requests.
- Load Balancing: Implementing load balancing distributes incoming traffic across multiple servers, reducing the risk of overwhelming a single server and enhancing the organization’s ability to withstand DDoS attacks.
- Access Controls and Authentication Mechanisms: Enforcing strict access controls and employing robust authentication mechanisms mitigate unauthorized access, reducing the risk of DDoS attacks initiated through compromised credentials.
Conclusion
DDoS attacks pose a severe threat to organizations, causing disruption, financial loss, and reputational damage. To fortify defenses, embracing strategies like air-gapping and data immutability is crucial. These measures, coupled with a proactive cybersecurity approach and utilization of DDoS mitigation tools, enhance resilience against evolving threats.
By adopting a comprehensive defense strategy, organizations can effectively combat the menace of DDoS attacks and ensure uninterrupted business operations.










