Ransomware attacks grow sophisticated with each attack. The usual “ enterprise data protection” practices aren’t sufficient enough. So, we recommend backup and DR as a means to effectively ransomware-proof your critical servers. In this blog, we’ll explore why conventional methods aren’t good enough and what makes backup & DR the best way to resist ransomware attacks.
Conventional practices used to make servers ransomware-proof
Ransomware is no longer a buzzword and organizations accept that. Which is why most are already increasing their cyber-security budgets and investing in methods that they think will help them fend off ransomware attacks. Unfortunately, clever marketing leads to bad executive decisions and contributes to the high success rate of ransomware attacks. In other words, most conventional practices aren’t effective enough against ransomware.
If you’re wondering, “why aren’t conventional practices effective?” We’ll answer that question in each of the following sections as we briefly discuss these practices.
Offsite data storage
That’s typically the trail of thought that leads organizations to rely on offsite servers or secondary servers to store copies of critical volumes. However, this isn’t as safe as it may sound like because of how ransomware spreads.
We’ve talked about how ransomware spreads in detail previously read here.

The “catch” with such software is that ransomware attacks grow sophisticated and evolve faster – so much so that the software can’t keep up.
While anti-ransomware software can protect your servers from known threats, it may not be able to protect your server from every new ransomware threat. Which is why relying solely on an anti-ransomware and/or antivirus software is not a good strategy and will not effectively ransomware-proof your servers.
Tape Archives

Ransomware attacks have gotten more effective over the last few years and unless proper backup & disaster recovery (DR) solutions are set up beforehand, there’s the risk of being infected, losing critical data, and downtime.
Now that we’ve established that conventional practices just aren’t enough, let’s look at why backup & DR solutions are the best way to make your servers ransomware-proof.
Why backup & DR solutions are the best way to make your servers ransomware-proof
Before we discuss why backup & DR solutions are the best way to deal with ransomware attacks, we need to clearly define what we mean by backup & DR solutions; it’s not the typical definition that you might think.
How we define “backup & DR solutions”
At StoneFly, Inc. we define backup and DR solutions a bit differently than the traditional concepts. We strongly advocate that a backup and DR solution has to be turnkey, simple-to-use, and should have the following components:
- Continuous data protection (CDP) – shorter RTOs and RPOs
- Ability to recover instantly with features like direct VM spin up, instant and/or full VM recovery, etc.
- Secure target storage repositories (on-premises & in the cloud) – using air-gap, WORM storage for file and S3 object data, & other similar features
In other words, we don’t accept the following as effective backup and DR:
- Snapshot-based “backups” only
- Syncing or mirroring servers
- Offsite data storage
This is one of the reasons why we’ve paired up with Veeam software to develop a Veeam-ready backup & DR solution that embodies our understanding of backup and DR, but that’s a topic for another time. If you’d like to learn more about our hper-integrated Veeam-ready backup & DR appliance, click here.
There are more than one way to set up effective backup and DR, so let’s go over what kind of setups you can have to make your mission-critical servers ransomware-proof.
Different ways to setup backup & DR for your critical servers

To protect your servers from ransomware attacks, you can look into the following ways to setup backup and DR:
On-premises backup & DR appliances
Traditional backup servers don’t come with any storage capabilities, so you have to purchase and configure storage arrays separately.
In other words, because they aren’t turnkey or easy-to-use, we don’t accept traditional backup servers as effective backup and DR. As a solution, we offer complete backup and DR appliances that have integrated file, block, and object storage, and everything preinstalled, tested, and ready for use.
Take our DR365V Veeam-ready backup & DR appliances for example. They come preconfigured with Veeam availability suite v10, user’s choice of hypervisor (VMware, Hyper-V, KVM, Citrix, or StoneFly Persepolis), and advanced data services like snapshots, air-gap, WORM, encryption, and more to secure Veeam backup data & provide the complete experience. (learn more)
Cloud backup & DR
This sort of setup can be seamless or quite complex depending on which backup software you choose and the type of cloud support it has.
For example, you can opt to purchase Veeam software and integrate Azure, AWS, other S3 clouds, or StoneFly private cloud to get a highly secure, compliant, and affordable cloud backup and DR setup. If you purchase it from StoneFly, we make the integration and set up seamless and easy so that you can have it up and running in a few hours. (learn more)
Hybrid backup & DR (on-premises + cloud)
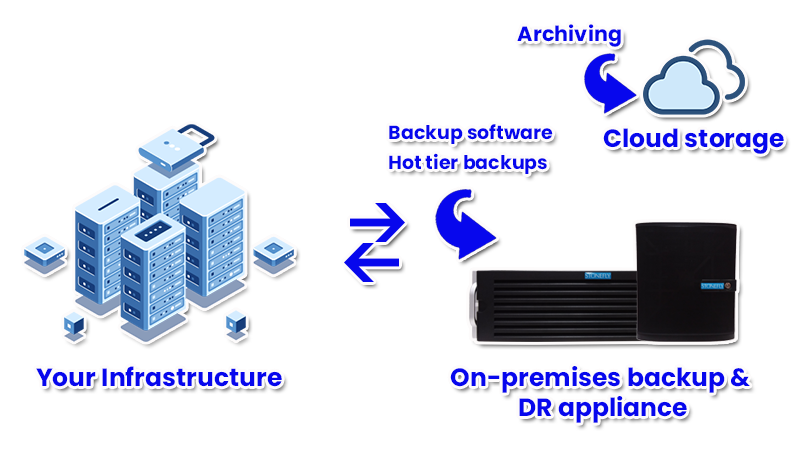
- On-premises backup server with enough storage for hot volumes and cloud storage for cold backup data and archiving
- On-premises backup server with integrated storage and cloud repositories to store redundant copies of hot and cold data with archiving
Hybrid backup and DR is highly secure and fit for all kinds of organizations regardless of the industry (healthcare, finance, corporate, etc.) and size (SMBs, SMEs, & large organizations).
A few examples of hybrid backup & DR solutions include StoneFly DR365V, DR365, DR365Z, and DR365U.
Most effective backup & DR: 3-2-1 rule

The 3-2-1 rule recommends creating three copies of your data, storing your data on two storage media, with at least one copy offsite.
The easiest way to set up the 3-2-1 rule is to use a hybrid backup & DR solution to do it as it has all the necessary components.
Conclusion
Ransomware attacks have gotten clever and sophisticated. Conventional practices such as offsite data storage, anti-ransomware or antivirus software, and tape archiving are not enough to make your servers ransomware-proof.
In order to make your business-critical servers ransomware-proof, you need to use backup and DR; and set it up in accordance to the 3-2-1 rule.
Related Products
On-Premises & hybrid backup & DR appliances
- StoneFly Veeam-ready backup & DR appliance (DR365V)
- StoneFly “DR Site in a box” appliance (DR365)
- StoneFly backup & DR appliance for Zerto (DR365Z)
- StoneFly Universal backup & DR appliance (DR365U)
- StoneFly Backup Server Plus+™
Cloud backup & DR:
- Veeam cloud connect to Azure
- Veeam cloud connect to AWS
- Veeam cloud connect to StoneFly Private Cloud
- CDR365 – server backup software
Connect with us on other social media
To learn more about ransomware and how to protect your infrastructure, connect with us on our social media channels:
Twitter: https://www.twitter.com/stoneflyinc
Facebook: https://www.facebook.com/stoneflyinc
Linkedin: https://www.linkedin.com/company/c/stonefly-networks/
Youtube: https://www.youtube.com/stoneflyinc










