This is the first article in the Storage Concentrator Series which is meant to explain the features of StoneFly’s Virtual Storage Appliance SCVM as well as help users to operate it. deploy different segments in the Storage Concentrator. following, to the article which is meant to guide you through the steps, required to deploy different segments of GUI. The last article discussed about home page in GUI and Master storage concentrator menu. This article will discuss about the resources section in GUI, how to discover resources and how to add resources in GUI.
Resources
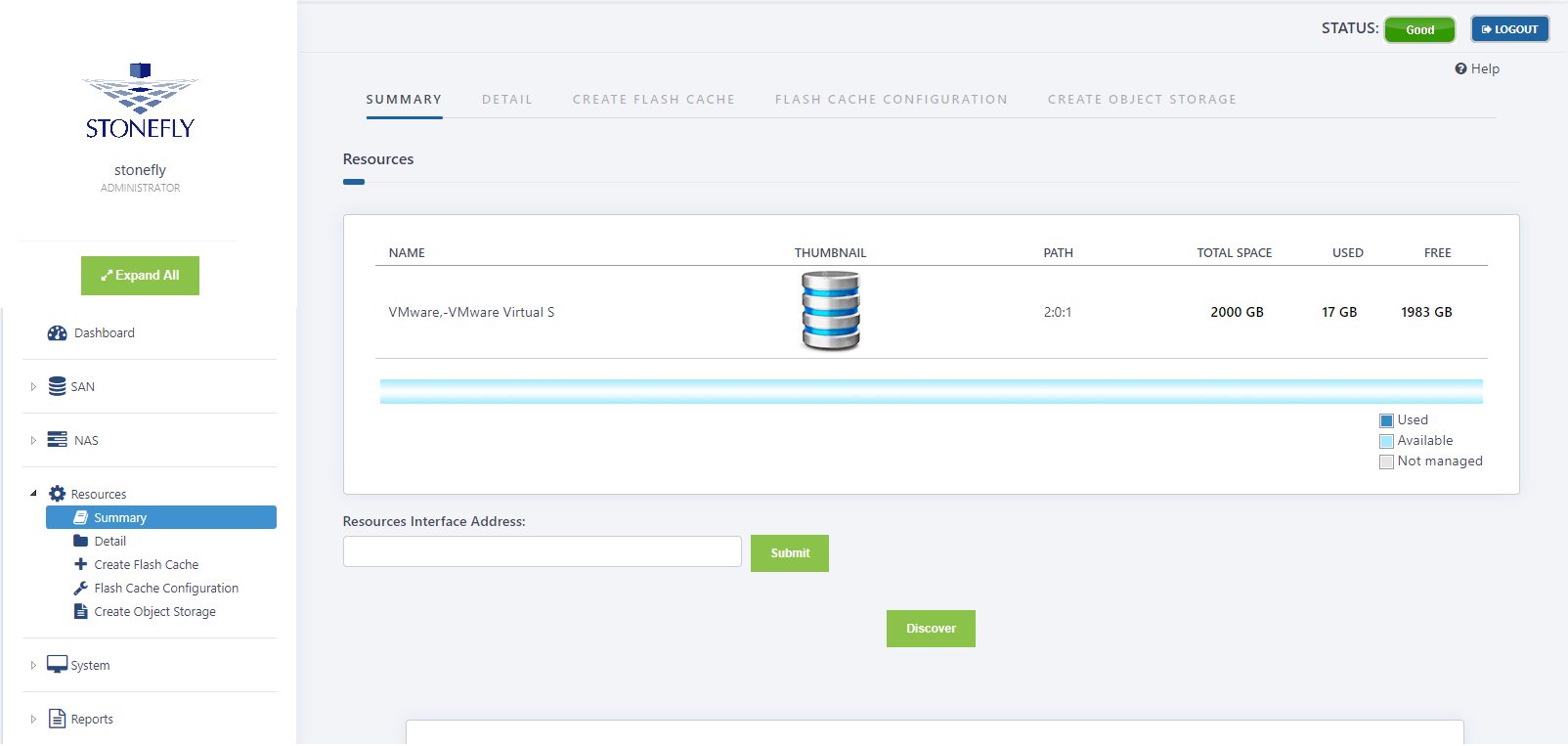
After initial configuration is completed, the next step is to discover resources of the IP Storage. A resource device is a data storage subsystem. Resource devices may include RAID drives and JBODs (simply standing for – just a bunch of disks). A resource device is typically attached directly to the Storage Concentrator.
Discovering Resources
Discovering resources is the process the Storage Concentrator uses to query the resource device for information. At start up, the Storage Concentrator automatically discovers any resources that are attached.
To add resources using the Discover button on the Resource Management Summary Screen, use the steps that follow:
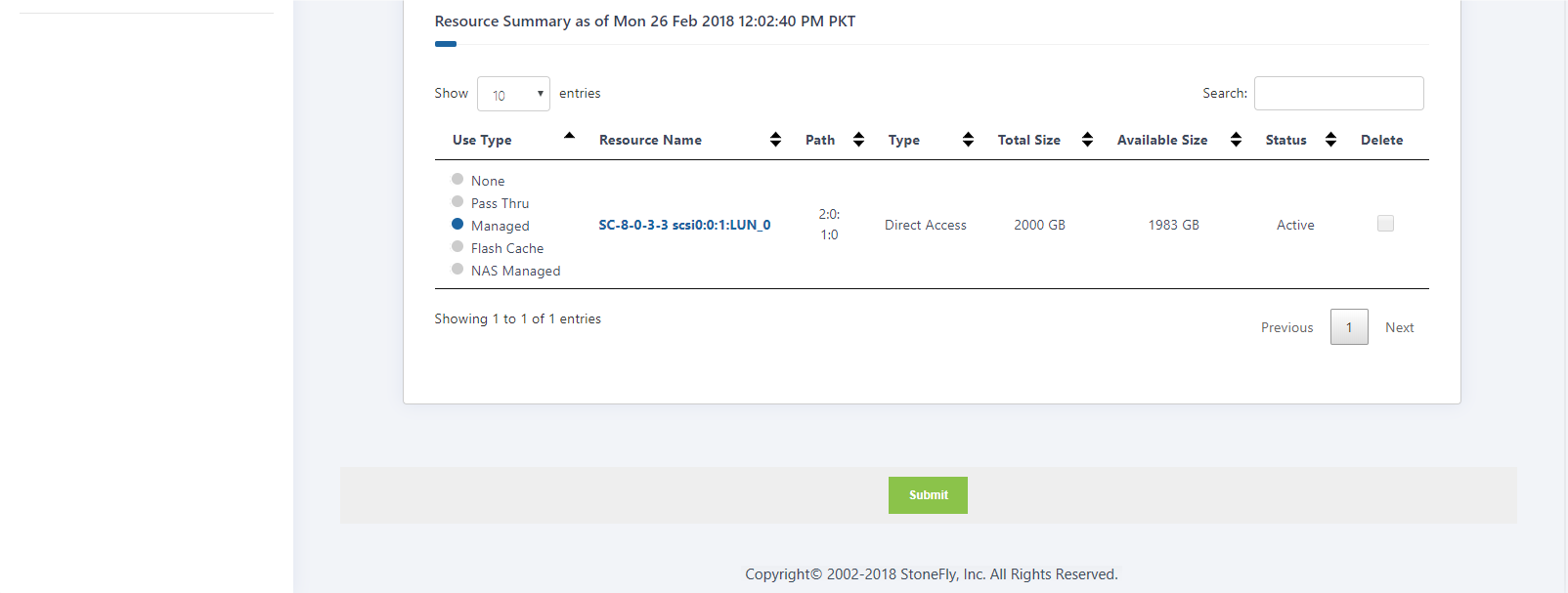
- Navigate to Resources > Summary. Any previously discovered resources display on the Resource Summary screen.
- Select the radio button to discover resources for the Primary unit, Secondary unit, or both (the default):
Primary Unit: Selecting the Primary Unit will only discover resources for the Primary Unit. Since both the Primary Unit and the Secondary Unit are resource aware, this will reduce the time required to discover resources.
Secondary Unit: Selecting the Secondary Unit will only discover resources for the Secondary Unit.
Both: (default) Selecting both will discover resources for the Primary Unit and the Secondary Unit.
Select either the Secondary Unit or the Primary Unit if you have a problem (such as a cable issue) on just one unit. Or select one or the other when there are a lot of resources to discover and you want to prevent the discovery process from timing out by discovering on the Primary Unit first and then the Secondary Unit. Generally, using both will be the preferred discovery method in most cases.
- Click Discover. The following dialog box appears.
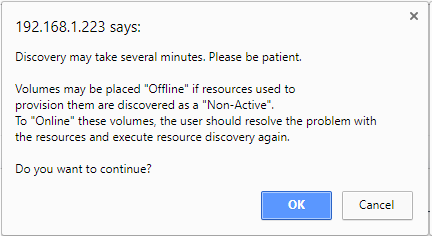
- Click OK.
Adding Resources
As storage needs change and grow, additional storage resources may be added to accommodate your storage requirements. Discovering resources is the process the Storage Concentrator uses to query the resource device for information.
You can use the Discover button on the Resource Management Summary screen to ADD storage resources without rebooting the Storage Concentrator. Existing resources may not be modified.
Storage resources can be added without rebooting the Storage Concentrator when the Storage Concentrator is connected to a disk enclosure that has empty slots available for additional hot–swappable drives, and additional drive(s) are inserted into the enclosure. When the Discover button on the Resource Management summary screen is selected, the disk drives are added as storage resources and are available for use by the Storage Concentrator.
To add resources using the Discover button on the Resource Management Summary Screen, use the steps that follow:
1. Select the radio button to discover resources for the Primary unit, Secondary unit, or both (the default).
2. Click Discover. The following dialog box appears.
- Click OK.
When discovery is complete, all available resources will appear for the Primary Unit regardless of which radio button has been selected.
- Click the Managed button for each resource you want the Storage Concentrator to manage.
- When all resources to be managed by the Storage Concentrator have been selected, click Submit.
These resources are now available and storage volumes can be created.
To add storage that requires rebooting the Storage Concentrator, use the steps that follow:
- Shut down the Storage Concentrator. For more information, see “Shutting Down”. If hosts are currently online, shut them down.
- Configure the storage resource device.
- Power on the Storage Concentrator.
- After the resources are configured on the Storage Concentrator, restart the host computers.
The Storage Concentrator automatically discovers any newly configured resources and rediscovers any existing resources.
This is the conclusion for this article. This article explained that, how you can discover and add resources in GUI. The next article will guide you that how you can edit and remove resources in GUI. If you need any help, we are here for you.










