This is the introductory article in the StoneFly Storage Concentrator™ Series. The series is meant to help users understand the process of deploying different features of StoneFly’s virtual storage solution SCVM™ (Storage Concentrator Virtual Machine).
This article intends to help users launch the StoneFly Storage Concentrator™’s administrative interface .
The StoneFly Storage Concentrator™ appliance software provides the interface through which a system administrator can configure and monitor different parts of their system operation like:
- Logical volume management of all connected storage
- iSCSI interfaces that interconnect the host systems with the disk subsystems
- Upper level applications that provide an extensive suite of storage management functionality
- System operation and status
- FailOver protection
- Synchronous mirroring
- Storage Snapshots
- Asynchronous data replication
- Data volume encryption
- Storage thin provisioning
- Data deduplication
- Creating and managing NAS volumes that can be exported to NFS and CIFS clients
The subsequent articles in the Stonefly Storage Concentrator Series will discuss each part or segment of GUI step by step. This introductory article will cover how users can launch the administrative interface in their StoneFly Storage Concentrator.
To begin, it is important to notice that the administrative interface resides on the Storage Concentrator. It is run from a network computer via a browser that can access the network where the Storage Concentrator is located.
Supported browsers include:
- Netscape 4.7 or later (Windows PC and Linux)
- Internet Explorer 5.0 or later (Windows PC only)
- Mozilla Firefox
To access the administrative interface, follow the steps below:
- Launch your web browser.
- Type the IP address for the Management Port of the Storage Concentrator in the address field of the browser. For more information, refer to the Setup Guide, “Configuring the Network Settings.”
Note : The address field in the browser must include https:// to access the administrative interface.
The following login screen should appear :
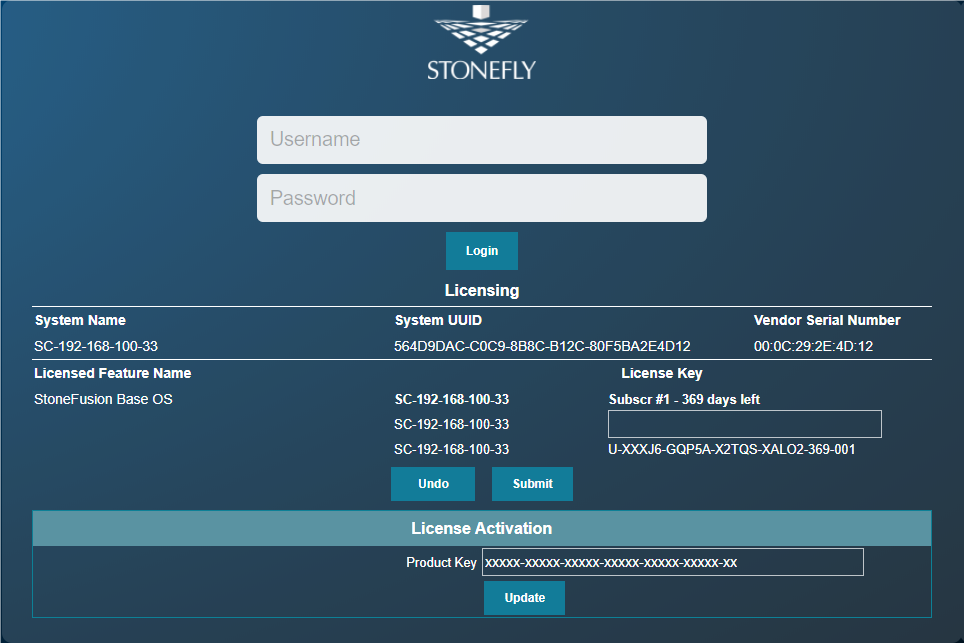
Accessing System Management Functions
To perform system management functions, you must log in with a user ID and password that is configured with administrative privileges.
Passwords must be between 6 to 15 alphanumeric characters long and contain at least one number. Passwords cannot be the same as the corresponding username. StoneFly only validates the first eight characters during login. Characters after 8 are ignored, but supported for user convenience. For more information on creating users, please refer to: “Adding Users”
When logging in for the first time, the administrator can use the following: User ID: stonefly. Password: stonefly. It is strongly recommended that the stonefly password be changed at the initial configuration. It is also recommended that each system administrator have an individual user ID and password. For more information on designing user logins, please refer to “Adding Users”.
1 Enter your User ID
2 Enter your Password
3 Press Enter or click Submit. The Storage Concentrator home screen should appear.
If you attempt to log in with an administrator user ID and password that are already in use, a warning message dialog box will appear.
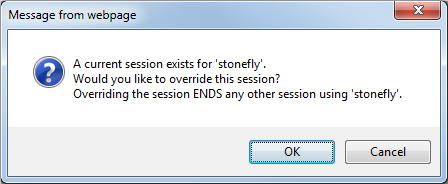
If this screen appears, choose one of the following options:
1. Click OK – This logs you in and logs off the user who is logged in with the same user ID and password you entered.
2. Click Cancel – The initial login screen appears. Repeat steps 1-3 using a different user ID and password.
And with that you have successfully launched the administrative interface for the Stonefly Storage Concentrator. The next article will cover the GUI’s home page and images as well as the Master Storage Concentrator’s menu.
If you have any lingering questions, don’t hesitate to our storage experts and request for their assistance.
![HowtolaunchtheadministrativeinterfaceinyourStoneFlyStorageConcentrator[1]](https://stonefly.com/wp-content/uploads/2018/06/How20to20launch20the20administrative20interface20in20your20StoneFly20Storage20Concentrator1.jpg)









