The massive wave of May 2017 Ransomware attacks that hit the world, suddenly turned a relatively-obscure malware threat into a global security concern and a screaming headline news

How Ransomware attacks work
Ransomware is a computer virus that infects a server, PC or a mobile device, usually when an aware user opens an attachment or clicks on an email link. The virus secretly locks the user’s files with an unbreakable encryption and then shows a ransom message: “make a payment [of several 100s dollars, and sometimes 1000s] to this online Bitcoin account, and you’ll receive a key to recover your files. If you don’t send the money, all your files will remain encrypted or be permanently deleted”. Advanced Ransomware variants have capabilities that allow them to spread to other servers and PCs. The infection spreads geometrically as each infected machine launches attacks on many other targets.
WannaCry targets Microsoft’s file sharing protocols
WannaCry, also known as Wanna Decryptor, WanaCrypt0r 2.0 and WannaCrypt exploited a vulnerability in Microsoft’s file sharing protocol that was only lately discovered and hence many enterprises had not patched yet. That vulnerability combined with a weapons grade worm created by the NSA, enabled WannaCry to spread and multiply with incredible speeds, creating destruction around the world in less than 24 hours.

Defending against WannaCry and Ransomware variants
While WannaCry has made the general-public suddenly aware of Ransomware, it’s only the latest in a series of attacks from Ransomware variants that started to plague consumers and businesses years ago. Ransomware criminals forced over 1 billion dollars from victims in the last year alone; about 47% of businesses witnessed at least one Ransomware attack.
While paying the ransom might be tempting; it’s a bad gamble. In fact one out of five victims who pay the ransom never receive their promised files back. Not to mention that paying does not stop future attacks. Instead, it further funds the criminals’ development efforts and inspires more attacks. You can either become a repeat victim or build a defense.
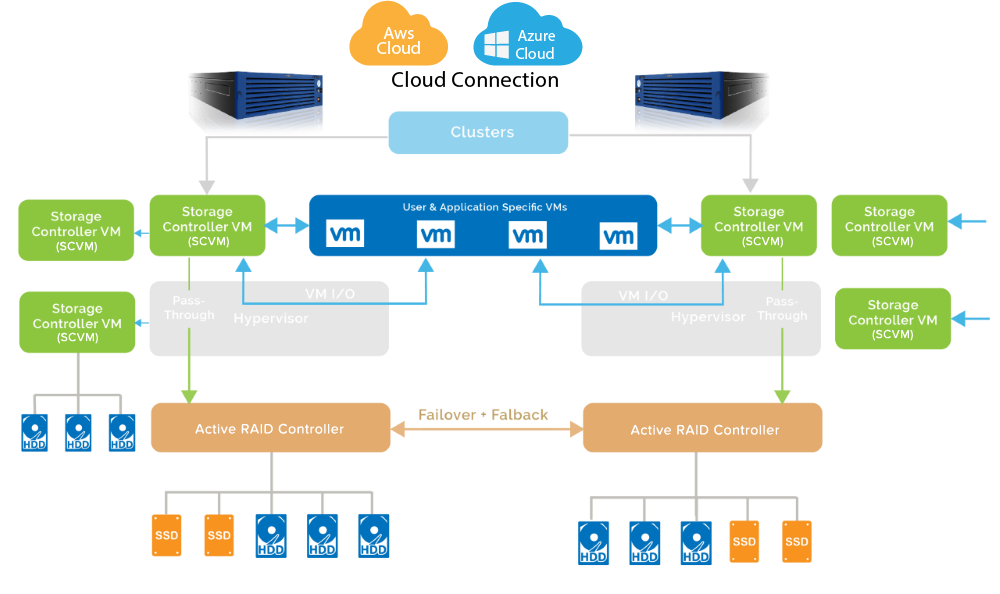
Keeping your file backed-up in diverse locations and storage media, allows you to quickly restore a Ransomware encrypted computer to its last fully functional state. StoneFly also protects its backup copies and storage repositories, which Ransomware targets to sabotage any restoral attempts. This year, StoneFly introduced a feature in its High-Availability SAN and Scale-Out NAS Storage Appliances that allows only the backup to get to the storage media – No Ransomware can get to the user’s data. Also, a feature in the StoneFly Dual Node Stretch Cluster uses machine learning and heuristic analysis to detect any suspicious activities and automatically detach the storage disks from the network which Ransomware uses to get to your files and block Ransomware attacks. Theses appliances come integrated with active protection which detects and overcomes Ransomware attacks that evade the signature based defenses found in antiviruses.
After WannaCry
WannaCry is vividly demonstrating that Ransomware gangsters are constantly upping their game. As much as the legitimate software-as-a-service, the rise of Ransomware-as-a-service in which malware coders are arming masses of unskilled criminals to infect targeted machines – provides a concrete evidence of the rising sophistication and reach of this rapidly expanding threat.
Friday’s malware cataclysm will force many previously unaware or indifferent businesses to finally take the Ransomware threat seriously. IT-security professionals will recommend a multi-layered, in-depth defense approach to: maintain a rigorous backup regime, deploy endpoint security measures like antivirus and keep their signature databases up to date, scrupulously patch known-vulnerabilities in applications and operating systems, segment networks with VLANs and firewalls to prevent malware propagation, and educate users on how to deal with malicious internet ads, virus bearing websites, infected USB drives and suspicious email links and attachments.
Here at StoneFly we recommend that you take all of these steps. But if you truly want to feel that your enterprise data is secure from WannaCry attacks and Ransomware extortionists. And if you are looking for IT products and services with active data protection that stop Ransomware and its other variants in their tracks – then you have come to the right place.
If you recognize the enormous business opportunity in protecting your customers against Ransomware and want to become a reseller of StoneFly services and products, register here.










