The days of installing antivirus software on each of your business computers and thinking you’re protected are over. Today’s cyber security threats are constantly evolving and if you’re waiting for that next update of new viruses to be released, it’s like texting and driving. You might get away with it for a while but sooner or later something really bad is going to happen, like ransomware. Imagine having your entire company’s data held hostage and possibly lost forever if you fail to pay the required ransom.
Cybercrime is a global problem that poses a threat to individual security and an even bigger threat to large international companies, banks and governments. Today’s organized cyber-crimes far out shadow loan sharks of the past; now cyber-criminals have large organized crime rings. They are constantly innovating online attacks. Most companies have preventive security systems to stop these type of attacks.
What is Ransomware?
Ransomware is a type of malicious software which restrains access to data until a ransom amount is paid. It is basically a subset of malware, where data accessibility is prevented and an amount is asked to access the data. The data is locked by encryption key and payment is demanded before providing the decryption key. In this case the victim is notified after the attack has successfully occurred. As the payment demanded is paid in accordance to the instructions provided by the attacker. Payment is claimed in cryptocurrencies like Litecoin, Bitcoin, Ethereum (ETH) so that the criminal’s identity remains unknown.
Ransomware attacks have started spreading internationally from around 2012 and the attacks are increasing day by day. Stonefly offers secure way to have a digital life, which is uninterrupted. It offers resilience from ransomware with appropriate recovery plans.
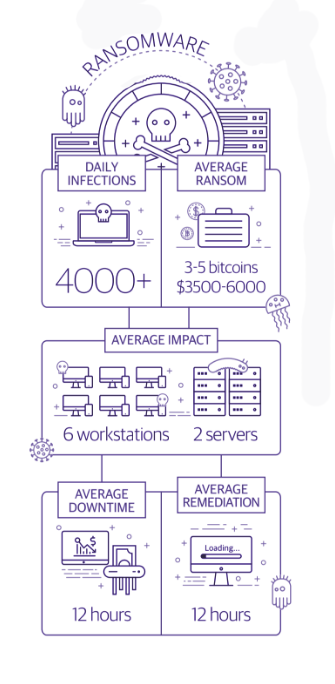
Survey about Ransomware:
The number of cyber-attacks are increasing with time and according to a survey the attacks have been increasing from 14% in 2016 to 27% in 2017, as noted by Accenture in a recent report on cybercrime. It is predicted by Cybersecurity Ventures that the ransomware attacks will increase each 14 seconds by 2019. The damages which ransomware incur include:
- Loss of mission critical data.
- Business downtime
- Productivity loss
- More recovery time
- Post attack disruption
- Bad reputation
- Disruption to regular operations
- Financial losses
Ransomware resilience and data protection strategies:
It is important to have resilience against ransomware. StoneFly offers enterprise level solutions which provide resilience against ransomware and deliver backup and disaster recovery for the enterprise.
Data Transportability:
Data transportability is the process in which you can migrate data between applications, cloud storage tiers and computing environments. In cloud computing data mobility between different cloud service providers or in storage tiers, like migrating data from Amazon S3 to S3-IA, is known as transportability.
In StoneFly data transportability isn’t simply data migration. StoneFly’s application of data transportability makes it a very useful concept for data protection purposes.
Data Transportability with StoneFly’s Appliance:
StoneFly’s innovative Storage Concentrator Virtual Machine (SCVM™) allows you to dedicate disks in which you replicate your data. You can choose that which type of applications or data you want to keep in those disks.
When ransomware attacks happen or in case of a hardware failure the SCVM™ disconnects those disks automatically and thus this prevents the damage, corruption or exploitation of data which you have replicated on that disk. These disks can also be removed from the damaged or dysfunctional appliance and used with another appliance to restore all the data.
Data Transportability is just one of the enterprise level data services provided by StoneFly. StoneFly provides you with customized solution which allows you to have data storage and data recoverability in a secure way.










