Gartner estimates that Disaster Recovery as a service (DRaaS) is now a mainstream service in the market and it will grow 6.5 times by 2021 (over the next three years). With digitalization and virtualization driving the enterprise, data has become an integral part of all organizations. StoneFly provides enterprise level DRaaS to enterprises around the globe.
This article explores the basics of Disaster Recovery (DR). DRaaS can be especially beneficial for service providers who would like to strengthen their portfolios and empower them with highly in-demand services to boost customer loyalty and earnings.
What is Disaster Recovery (DR)?
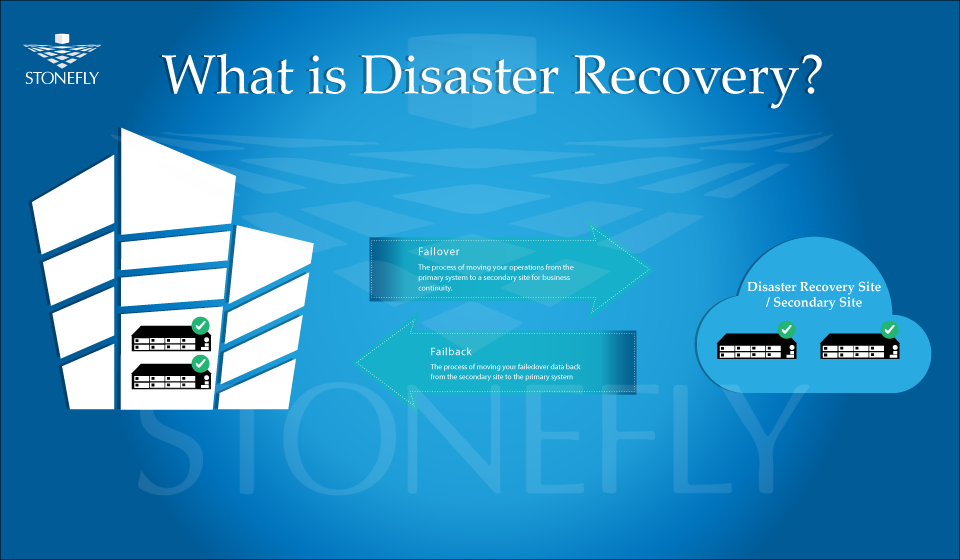
The notion of disaster recovery is based on two concepts: failover and failback. Failover is the process of switching to a redundant or standby physical or virtual machine upon the failure of the previously active physical machine. In turn, fail back is the process of restoring operations to the primary physical machine after they’ve been shifted to a secondary machine during a failover. Disaster recovery includes the replication and hosting of virtual or physical servers to provide failover in the event of a man-made or natural catastrophe. This process is often performed by a third party.
Causes of Outages
There are two popular beliefs about outages:
- They’re caused by just natural disasters such as hurricanes and earthquakes.
- Therefore, it’s unlikely to affect you.
These assumptions aren’t exactly correct, let’s look at the statistics. According to the well-known and reliable sources such as actual tech media, the number of companies that experience at least one outage this year has increased 9% as compared to the previous year and has reached 46 percent overall. Moreover 94% of business outages are related to power loss: hardware failure, software updating and accidental data deletion and not to the natural disasters.

Cost of Outages
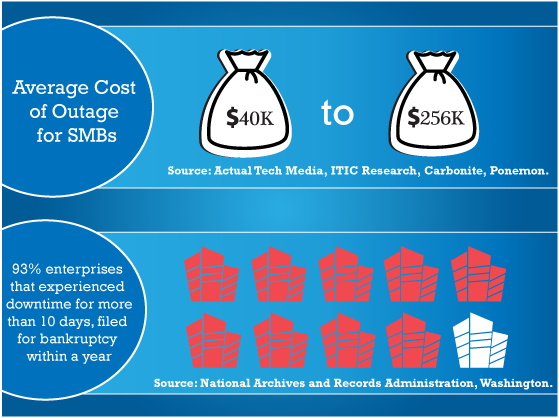
Regardless of its cause even a small outage can be very painful for companies of any size both in terms of direct costs such as decreased earnings and indirect effects such as the company’s image deterioration and increased churn rate. According to the search engine research and actual tech media portals the average outage lasts 2.2 days and can cost a smaller medium-sized business from forty thousand to two hundred fifty six thousand dollars. Moreover, according to recent published reports by the National Archives and Records Administration in Washington, 93% percent of companies who have lost their data center for ten days or more during a disaster filed for bankruptcy within one year after the disaster.
DRaaS Targets
Disaster recovery technologies are targeted at the following types of companies:
- Companies who rely on mission-critical applications and data.
- Companies that are subject to strict compliance requirements.
- Companies acting as partners in rigorous supply chain management.
- Companies located in disaster prone areas.
- Companies that do not have sufficient human resources with strong data protection skills to ensure a high level of business continuity.
- Companies heavily relying on IT for business functions.
- Companies that do not have sufficient disaster recovery experience.
This covers a wide range of industry starting from financial services and healthcare up to construction and transportation and many others
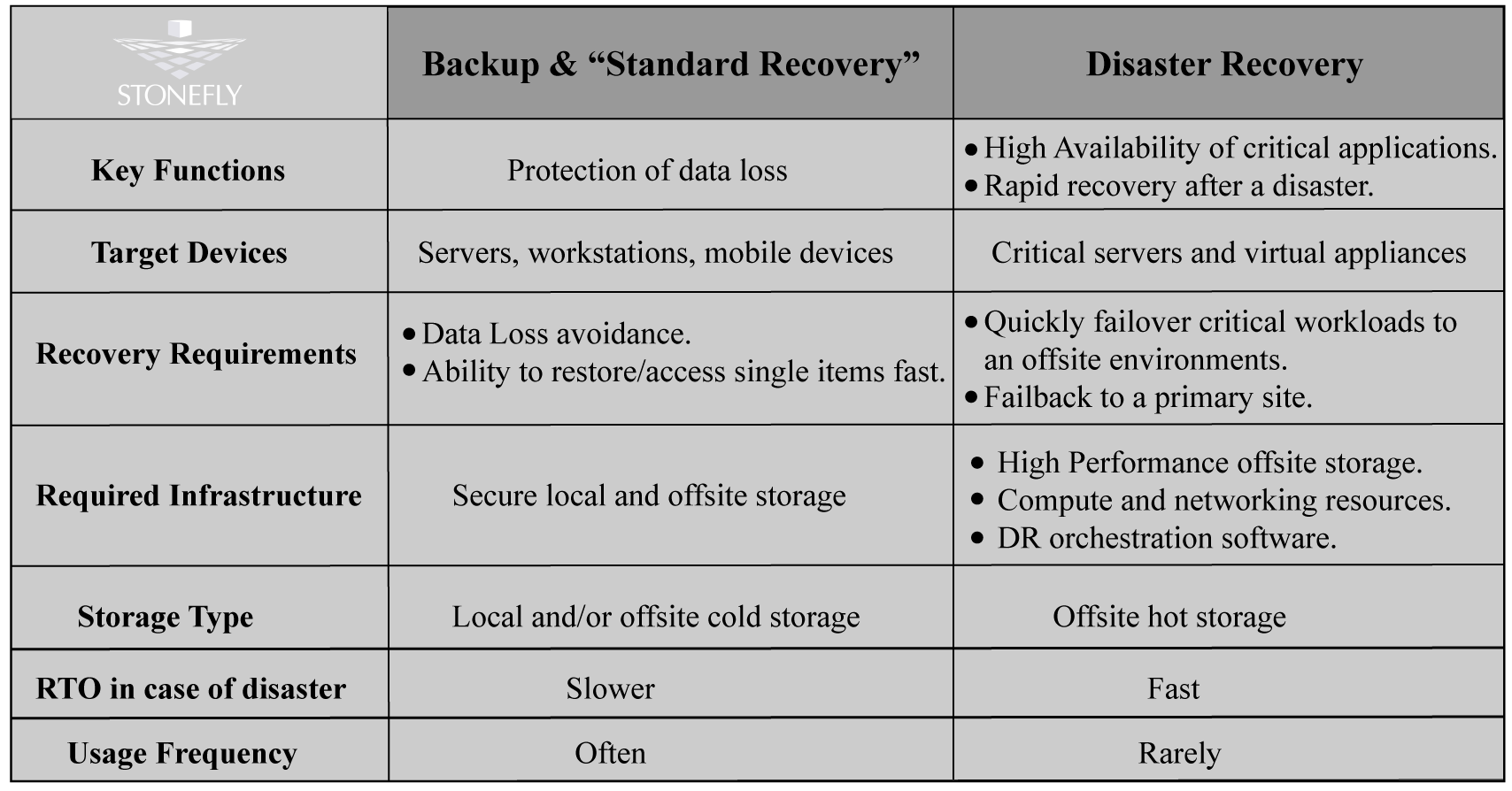
Disaster Recovery vs “Standard” Recovery
The term “Standard” recovery, in this case, refers to data recovery from data backups (this includes on-premises backup and cloud backup).
Standard backup recovery and disaster recovery have different underlying technologies and target audiences. From the viewpoint of technology standard recovery is based on cold storage whereas disaster recovery uses hot storage. Cold storage is information that you don’t need to access very often. It represents inactive data that doesn’t need to be accessed for months or even years. In turn, hot storage is data you need to access right away.
The goal of standard recovery is to protect corporate data from loss. In contrast, the key function of disaster recovery is to perform a fast recovery after a disaster and ensure a high level of availability of business critical application. The targets for standard recovery are servers, workstations and mobile devices whereas disaster recovery is aimed at business critical applications and servers.
To summarize, disaster recovery should not be treated as yet another recovery mode that is more sophisticated and expensive as compared to standard recovery and is only targeted at a privileged network of elite clients. Moreover, it shouldn’t be seen as a substitute for standard recovery. Both recovery types can be officially used within one company. For instance, standard recovery can be used for file level recovery of Windows machines whereas disaster recovery can be used to restore servers and business critical applications such as e-commerce websites.
Summary
Disaster Recovery relies on two concepts: failover and failback. Failover is the process of switching to a redundant or standby physical or virtual machine upon the failure of the previously active physical machine. In turn, fail back is the process of restoring operations to the primary physical machine after they’ve been shifted to a secondary machine during a failover.
DR is now a mainstream service and Gartner estimates that it will continue growing in the coming years. Conventionally, it is assumed that natural disasters are the main cause of data loss. However, the major cause of data loss is hardware failure and software updates.
On average, downtime lasts for 2.2 days and can incur financial losses ranging from 40 thousand to 256 thousand dollars.
Industries like finance industry, health industry, transport etc. need these DR services to ensure that their mission critical data isn’t lost.
DR and backup restore are two different things. Backup is meant to ensure that data isn’t lost while DR ensures that downtime is either prevented or reduced as much as possible. That’s why both recovery modes are integral parts of a backup and disaster recovery plan.