There are tons of companies providing cloud backup services, so what makes StoneFly’s service provision unique? What differentiates StoneFly from them and why is StoneFly trusted by clients that include governments? Let’s look at what practices StoneFly employs to efficiently backup, recover, secure and protect your data.
Volume Shadow Copy Service
This is an integral part of the backup architecture that Microsoft designed and is set in place with Hyper-V. It’s not something new; it has been around since 2003; so this is not a new concept. The initial beginning of the Volume Shadow copy Service (VSS), made it possible to go back and recover a file from its previous editions in case a file was deleted. Microsoft paired VSS with other components to evolve it in accordance to cloud backup solutions.
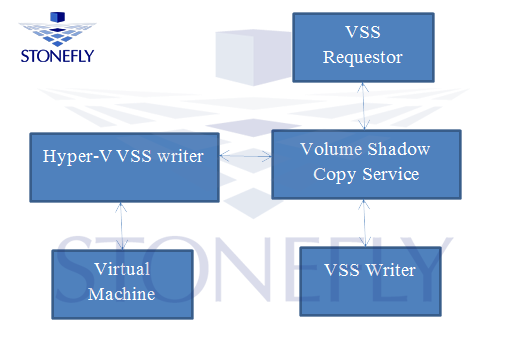
The first component that comes in the line of the components associated with VSS is the VSS requestor. VSS requestor makes a request to the volume shadow copy service to make a backup. The term backup here implies the creation of an image and its storage as a VHD file. This creation of the image is done by one of the VSS writers. In case of a backup and data replication job, the VSS requestor asks the volume shadow copy service that “I need to backup a virtual machine (VM)”.
This VSS is going to talk to the Hyper-V VSS writer. The Hyper-V VSS writer is going to relay that information to the VSS writer and it’s going to access the image of the requested VM or group of VMs and write the content of that file. Finally, the volume shadow copy service is going to wrap that information back to the VSS requestor and the VSS requestor is going to allow us to do some innovative things with the newly created backup. VSS requestors are a piece of software, based on the requestor that you choose; you can have access to multiple type of writers and you can have the ability to write multiple types of disks.
Compared to the traditional agent based backup from a physical environment, this process is worlds apart. It’s less costly, more time efficient, secure and reliable than physical servers. It may act like a physical machine but it has the benefits of a VM.
Compared to the traditional agent based backup from a physical environment, this process is worlds apart. It’s less costly, more time efficient and it’s more secure and reliable than physical servers. It may act like a physical machine but it has the benefits of a VM.
Changed Block Tracking
Changed block tracking (CBT) is a driver that comes along when you install Veeam backup and replication. It’s infused or injected into the Hyper-V host. What it does is that it monitors changes that are made to the VMs that have been backed up. The CBT runs on each virtual host, not on the VMs themselves, but rather on the Hyper-V system. The CBT runs automatically, while running it monitors any changes made to structures in a virtual environment that have been backed up.
Let’s consider an example to better understand this driver and what makes it one of the best practices to ensure secure backup. Let’s say you have done your initial backup on Monday. Any changes that are made are going to be noted by the CBT mechanism. Now, when it comes to take the next backup, instead of going back and pursuing the entire structure of the VM, you are able to look at the file created by the CBT. It will show you the files that have changed and make the incremental backup from here on. This dramatically reduces the time to take a backup.
Synthetic Full Backup
Forward Incremental backup is the best option if you are using tape storage and reverse incremental backup is the best when you consider disc to disc. Synthetic full backup is a combination of both of these backup methods. Using Synthetic full backup methods, you avoid the troubles faced with forward incremental. If your data is completely lost and you recover it, then you have to add the increments taken later. For the Synthetic full backup, you arrange your schedule and include a backup that takes less time and is equal to a full backup. What it does is that it takes the incremental backup and synthetically adds it to the original backup. So you can have restore points throughout the week and you have a full backup updated to the latest change, thanks to the CBT. This reduces the time and enables you to have your backup even faster when making the recovery of the entire VM or group of VMs.
Conclusion
These practices ensure that you have multiple ways of creating backups for your hyper-v environments. VSS can account for all the changes that happen after the backup and you can have the data readily available and the recovery is time efficient. If you’re interested in looking for cloud backup solutions that can provide such services, check out StoneFly. It has everything you need and more.










