At StoneFly we build backup and disaster recovery solutions and we build them for IT service providers, businesses that need to backup their business data and consumers as well. We have broad coverage of the backup and a disaster recovery market in terms of the personas that we are looking to help. One of the many backup and disaster recovery software of StoneFly is CDR365. CDR365 is StoneFly’s backup solution that is built for the cloud. It allows you to backup your data to major public clouds like Microsoft Azure and Amazon AWS.

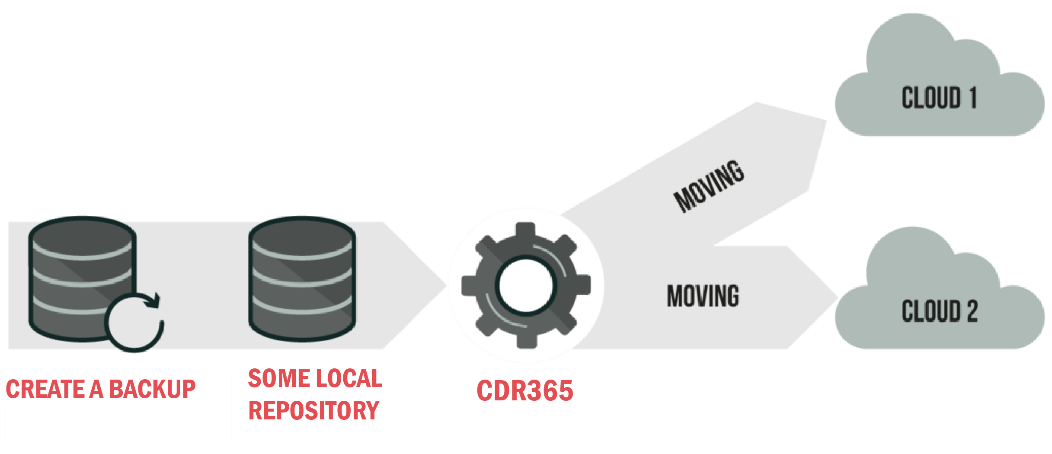
The attractive thing about CDR365 is you can leverage more than one cloud platform and store your backup data in multi-clouds, and even do local backups as well. CDR365 supports windows both the desktop and server variants as well as a variety of Linux distros and MAC. For business applications, CDR365 supports Microsoft sequel server and Microsoft Exchange. It can back those up using the native backup facilities but also move those backups directly to the cloud for disaster recovery. It supports Vmware, hyper-V as well as Amazon EC2 snapshots and provides full support for backing up your Google G Suite data. If you are using G suite hosted solutions for your email, calendar and Drive, CDR365 can back that up as well.
How CDR365 protects your data
CDR365 protects your backups and one way it does that is by allowing you to use your own backup storage from Microsoft Azure, Amazon AWS, etc. .The other way it does that is through the end-to-end data encryption. Everything is encrypted at the source, everything sent over the internet is encrypted and data is stored encrypted in the storage. This protects you and your backups from anybody being able to do anything with them should they ever get their hands on them.
The other attractive thing about CDR365 cloud backup solution is that for businesses there is no middleware required. You don’t need a backup server running, everything is agent based and communicates directly with cloud storage. It makes it much easier to implement at the business level by not requiring any servers.
Backup and restore features of CR365
CDR365 performs image-based backups for servers and desktops. Images of entire volumes is taken and if you need to protect your operating system along with all the files and be able to restore that server to a new piece of hardware or up into the cloud, CDR365 can support that. If you have need to backup your endpoints as an example your MACs, Linux and Windows desktops where you care more about the important user documents, CDR365 supports file and folder backup. For businesses, you can back them up with NTFS permissions. This means when you do your restores CDR365 can restore with the original permissions that way administrators don’t have to reapply permissions to files that are restored which can be a big convenience and time saver.
To facilitate being able to do the 3-2-1 backup rule with your backups, CDR365 supports hybrid backup. Hybrid backup technology allows you to do simultaneous backup to the cloud and to local storage in a single pass. You have your backups local in case you ever need to do a really fast restore but your backups are also protected up in the cloud in case there is some type of disaster.
With the CDR365 you get to decide how much data you want to keep and for how long. For instance, you can keep all of your backups for 90 days and up to 14 different versions of every file that is backed up. You can also decide how you want to handle deleted files (files that are deleted locally), whether or not you ever want them removed from the backup storage. You can keep them forever or you can decide to delay the deletes for a few days or a week. This way if somebody deletes something locally or you accidentally delete an important file, you have a full week before it actually would get removed from your backup storage.
CDR365 also supports data tearing enabling you to set up your object lifecycle policies. Depending on type, you can move the data say from the hot storage tier to cold storage tier at any point of time or setup retention policies to move the data from one storage tier to the other after certain period of time. You can save a lot of money by moving your older data that you are less likely to need for restore purposes to cold storage tier.
Complete protection against Ransomware
It seems like not a week or two goes by before there is a report of another ransomware product or attack. One of the difficulties about ransomware is that if it does encrypt your existing files and you are running backup software, that backup software will end up backing up the encrypted files. That is fine if you are keeping many versions of your files. But, if you are only keeping one version or only the most recent version, the risk is that you will overwrite good backups with ransomware encrypted ones.
Ransomware protection mechanism that is built into the CDR365 examines the files as is backing them up. CDR365 will go ahead and do the backup anyway, but it will also make sure that the existing backups that are in your backup storage are not removed until you have approved whether or not you know these are truly a ransomware issue or they are fine. If it happens to be a false positive that causes the detection you just approve it and then everything will go back to normal. However, if you are suffering from ransomware infection you can be assured that your backups are in good shape.
CDR365 restore options
CDR365 gives a lot of options for restore. It doesn’t matter how you have gone ahead and done your backups, whether they are file, image or Virtual Machine backups, CDR365 has the ability to restore those backups. If you are doing just image-based backups of your entire system volume, you can still restore files and folders from that backup without having to restore the entire volume. The integrated catalog in CDR365 allows you to search for files, and you can see all the versions of every file that has been backed up, and then on the restore side you can go ahead and select which versions you need restored.
Don’t back up for backup sake, back up so you can someday restore those files. Try out the CDR365 for free today. Contact us at (510) 265 1616 or email us at [email protected].









