Considering the fact that ransomware is expected to attack a business every 11 seconds by the end of 2021, it’s crucial for data owners to make sure their data is safe. In this blog post, we’ll share 5 things you can do to make sure your critical systems are ransomware-proof.
Causes of successful ransomware infection
Before we share how to prevent successful ransomware attacks, let’s look at what causes them. According to Statista, the leading causes of successful ransomware infection are:
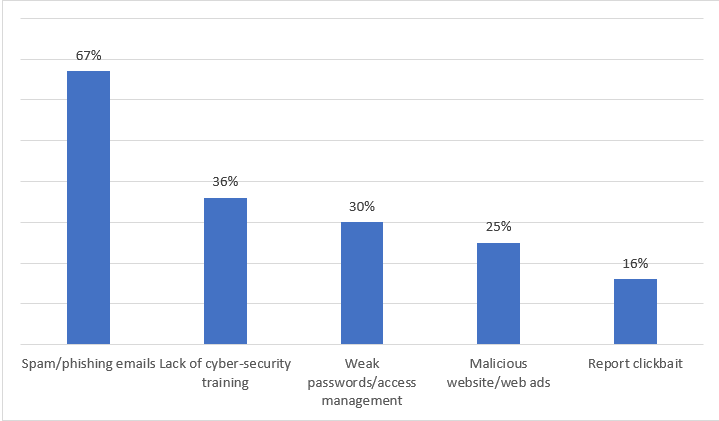
- Spam/phishing emails (67%)
- Lack of cyber-security training (36%)
- Weak passwords/access management (30%)
- Malicious website/web ads (25%)
- Report clickbait (16%)
By taking proactive measures in anticipation of the abovementioned causes, you can make sure that your data remains safe and your infrastructure is ransomware-proof.
How to Prevent Successful Ransomware Attacks
Ransomware attacks are costly. Experts expect the global damage cost of ransomware to be around $20B in 2021. This makes ransomware protection necessary for every organization that relies on virtual, physical or cloud servers for their day-to-day operations.
By following the underlying tips, you can make sure that your critical systems are safe from ransomware attacks:
1. Educate & train your users
According to the “Cost of Data Breach Report 2020” by IBM, human error accounts for 23% of cyber-security data breaches globally. In order to effectively counter ransomware attacks, it’s important to educate and train your users about cyber-security, malicious attacks, and ransomware.
Some common human errors that lead to successful ransomware attacks, include:
- Clicking on unverified links
- Opening spam emails or downloading untrusted attachments
- Downloading resources from shady websites
- Giving out personal information without verifying information
- Using weak or common passwords
2. Update & patch your OS and software
In May 2017, WannaCry ransomware wreaked havoc worldwide – leading to an estimated $4B in losses. The infamous ransomware exploited a vulnerability in how Windows implemented SMB protocol. However, the vulnerability had already been patched by Microsoft in March 2017. The systems that were affected did not update their Windows OS in time, and ended up becoming victims to WannaCry.
In other words, if they had updated their Windows OS, WannaCry would not have been able to infect and encrypt the data.
The WannaCry ransomware attack is the perfect example of why you need to update your OS and applications in time; and how not doing that makes your business-critical systems vulnerable to ransomware attacks.
3. Set up anti-virus and anti-ransomware software
Anti-virus and anti-ransomware function as the first line of defense against cyber-attacks and ransomware. Depending on the chosen software, your system automatically detects, quarantines, and removes malicious software before it encrypts your data. This makes these data protection software an essential part of every business-critical storage system.
However, it goes without saying, that relying solely on anti-virus and anti-ransomware is not a good idea. That’s because ransomware is evolving and getting complicated by the day; and data protection software cannot keep up.
4. Use highly secure target storage
In addition to anti-ransomware software, you have to make sure that your target storage repositories are ransomware-proof.
Features that make your target storage ransomware-proof include:
Air-gapped repositories
Air-gapped repositories are isolated from the production environment. This makes them a secure target storage to store backup files, snapshots, and replicas of your critical files.
In the event of a ransomware attack, you can use the data stored in these volumes to recover data and restore operations almost instantly – after cleaning up the ransomware.
Write-Once Read-Many (WORM) volumes
Write-Once Read-Many (WORM) volumes, or immutable storage, only allow read-access to stored data. The data stored in these volumes cannot be overwritten, edited or deleted – until specified by the storage administrator.
This also implies that data stored in these volumes cannot be maliciously encrypted by ransomware either. Hence, WORM volumes are well suited for volume snapshot, VM replicas, and backup data storage.
In the event of a ransomware attack, the data stored in these volumes can be used to recover operations seamlessly.
S3 object lockdown
S3 object lockdown, similar to WORM volumes, “lock” S3 storage repositories. The object data stored in locked volumes can only be read; and not edited, overwritten, or deleted.
For the same reason as WORM volumes, the data stored in these volumes is safe from ransomware attacks.
5. Set up backup & disaster recovery (DR)
One of the most critical thing to do, to prevent ransomware attacks, is set up automated air-gapped backup, immutable storage, snapshots, and DR.
With backup and DR, you can reduce the recovery time objectives (RTOs) and recovery point objectives (RPOs) and restore operations quickly – after cleaning up the infected systems from ransomware.
To learn more, we recommend reading: Protect your servers from ransomware attacks with backup & DR
Summary
In order to protect your servers from ransomware attacks, you need to:
- Educate & train your users
- Update & patch your OS and software
- Set up anti-virus and anti-ransomware software
- Use highly secure target storage repositories with air-gapped volumes, WORM, and S3 object lockdown features
- Set up backup & DR
By doing all of the above, you have highly secure storage that can resist ransomware attacks. Additionally, if somehow ransomware does manage to infect your systems, you have backup & DR to recover your operations seamlessly.
Related Resources:
Why should you worry about ransomware attacks?
Protect your servers from ransomware attacks with backup & DR
Backups aren’t enough – Here’s why you need air-gapping and immutability
Connect with us on other social media
To learn more about ransomware and how to protect your infrastructure, connect with us on our social media channels:
Twitter: https://www.twitter.com/stoneflyinc
Facebook: https://www.facebook.com/stoneflyinc
Linkedin: https://www.linkedin.com/company/c/stonefly-networks/
Youtube: https://www.youtube.com/stoneflyinc










