Various attacks have been made on data in the form of Ransomware. These attacks are constantly targeted at high profile organizations, government agencies, public utilities and transportation networks around the globe. The outbreak of this new global pandemic indicates that indeed we are living in the era of Ransomware. Data protection and disaster recovery have become ever important to ensure business continuity.
Ransomware: Irrecoverable Threats to Data
Ransomware is a type of malicious software that threatens its victims by exposing the data of the victims publicly. It can also block access to the data by encrypting it unless a ransom is paid. Ransomware spreads without limits downing numerous systems as it spreads. Data is always at a risk of being lost and valuable information can easily land in the hands of people who can use it against the users themselves.
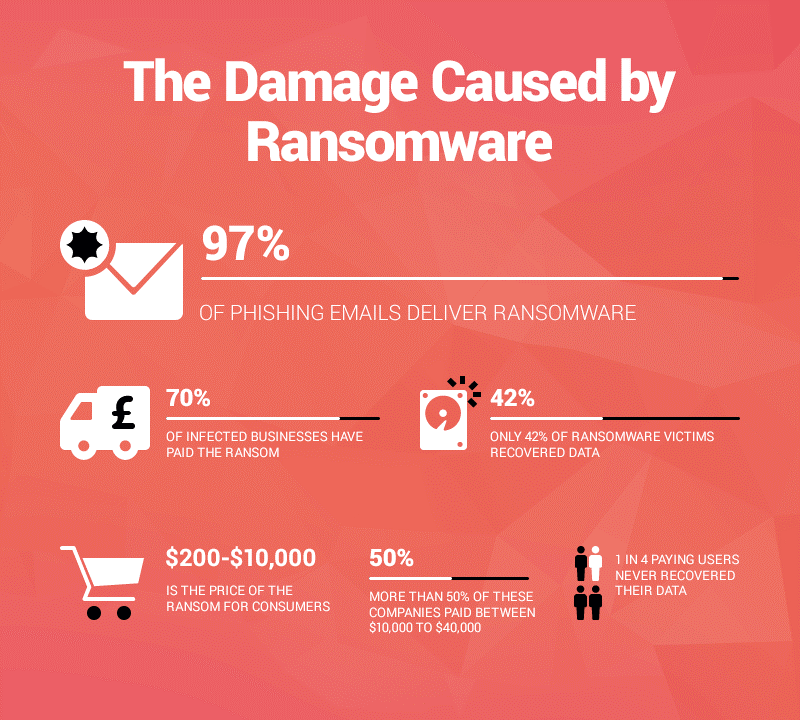
Some ransomware can be reversed easily by knowledgeable people because it does not lock the systems through the latest technology. However, advanced ransomware encrypts the files of the users through a technique called ‘cryptoviral extortion’. This malware encrypts the files of the users making them inaccessible. Users have to pay certain amounts in ransom to get the files decrypted.
A Trojan is used to carry out ransomware attacks. This virus is disguised as a legitimate file that the user is tricked into downloading or opening as an email attachment. Once the download has occurred, users are exposed. Valuable data of the users can be used against them.
StoneFly: Always hearing the Customers’ Voice, Serving to Protect through Freedom of Choice
Indeed the world is being constantly threatened from ransomware which can harm the data of anyone around the globe. There has been development of antimalware software globally, but they do not guarantee safety from advanced ransomware. There is a dire need of using techniques which provide a complete solution in themselves.
StoneFly has taken the responsibility to provide such a solution which not only protects the data entirely, but makes sure that you as a user are always safe from ransomware.
-Ransomware developers often encrypt their software to elude detection.
-Ransomware developers research antivirus solutions to find weakness holes they can use to escape discovery.
-Many strains are zero day exploits that are unknown to signature based antivirus software vendors. Ransomware software exploits these security holes without the knowledge of the antivirus software.
Ultimately your best protection solution against Ransomware software is a strong backup. The StoneFly DR365™ disaster recovery (DR) site in a box is a complete datacenter backup solution appliance for all physical and virtual servers that are integrated with automated business continuity on premises to any remote datacenter, private or public cloud. There is a little to worry about if you are hit by an attack, because you have secure, safe copies of your files that Ransomware can’t get to. The DR365™ is the only datacenter backup appliance that comes with automated offsite backup connection to Microsoft Azure Cloud or Amazon AWS Cloud depending on the choosing of the user.
- Fewer Independencies: Immutable files help reduce resource contention. The system can perform tasks simultaneously without waiting for one task to be done.
- More Flexible Reads and Faster Writes: With fewer resources being used to do the work, it is much easier to access the data.
- Depth of Security: StoneFly provides the ultimate replication and data protection to its users by giving them the option of storing data as read only. This provides the users with protection against ransomware as the data cannot be tapped into and changed.







